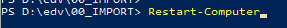03/2024, out of Band patches for DC crash KB5037422, KB5037425, KB5037423, KB5037426
DEUTSCH
ENGLISCH
We explain how to import the 4-5 manual patches for Server 2012R2, 2016, 2019, 2022 and what to fix if you get an error when you run the script to ImportUpdateToWSUS.ps1 to import the patches into WSUS.
Source of problem:
Following installation of the March 2024 security update, released March 12, 2024 (KB5035857), Local Security Authority Subsystem Service (LSASS) may experience a memory leak on domain controllers (DCs). This is observed when on-premises and cloud-based Active Directory Domain Controllers service Kerberos authentication requests.
Extreme memory leaks may cause LSASS to crash, which triggers an unscheduled reboot of underlying domain controllers (DCs).
https://learn.microsoft.com/en-us/windows/release-health/status-windows-server-2022#3271msgdesc
What changed or why is this so complicated?
You have to manual import the patches into WSUS which dies not work easy anymore with IMPORT function in WSUS.
Since a few months the WSUS Update from Windows Update Ctaalog solution is not working anymore. The trick with IE/EDGE and Zone Files and ActiveX Plugin does not work anymore.
https://www.butsch.ch/post/SRV-2012R2-WSUS-Server-Unable-to-import-from-Windows-Update-Catalog/
The new solution is to import the patches with a Powershell from MS but we have seen problems doing that on SRV 2019 + 2022 out of the box with nothing changed for WSUS Server.
Overview of the patches per 26.03.2024 with 2019 Patch
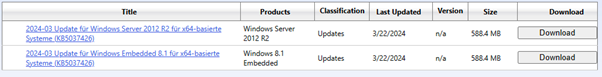
2012R2, KB5037426
2012R2, https://www.catalog.update.microsoft.com/Search.aspx?q=KB5037426
W10 + 2016, KB5037423
2016: https://www.catalog.update.microsoft.com/Search.aspx?q=KB5037423
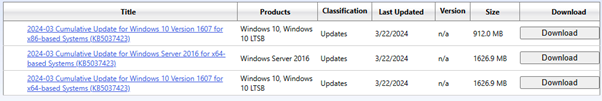
W10, X64: https://www.catalog.update.microsoft.com/Search.aspx?q=KB5037423
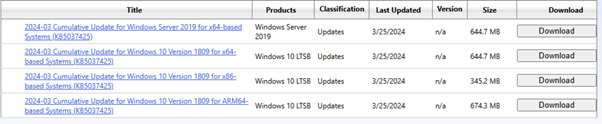
March 25, 2024—KB5037425 (OS Build 17763.5579) Out-of-band – Microsoft Support
2019, KB5037425
https://catalog.update.microsoft.com/Search.aspx?q=KB5037425
2022, KB5037422
2022: https://www.catalog.update.microsoft.com/Search.aspx?q=KB5037422
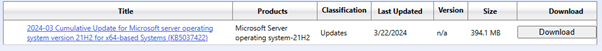
The ID of the patches:
|
2012R2 (KB5037426) |
|
.\ImportUpdateToWSUS.ps1 -UpdateId f2aaaf6d-b74b-4b64-aa72-535b1831124c |
|
W10 (KB5037423) |
|
.\ImportUpdateToWSUS.ps1 -UpdateId e2d5822a-19f1-4f96-95ad-3974a58f0a00 |
|
2016 (KB5037423) |
|
.\ImportUpdateToWSUS.ps1 -UpdateId 0683858a-06db-4f1a-b1eb-6ba0998d83f0 |
|
2019 |
|
.\ImportUpdateToWSUS.ps1 -UpdateId 69c36f19-90e0-49fb-b0f2-f317be093b59 |
|
2022 |
|
.\ImportUpdateToWSUS.ps1 -UpdateId 1bc3fe3f-74dc-48da-a3f3-65a6c06f4335 |
Step by step for 2016/2019/2022 SRV OS.
- Download the powershell ImportUpdateToWSUS.ps1 from WSUS and the Microsoft Update Catalog | Microsoft Learn | https://learn.microsoft.com/en-gb/windows-server/administration/windows-server-update-services/manage/wsus-and-the-catalog-site?branch=pr-4097#powershell-script-to-import-updates-into-wsus or https://github.com/MicrosoftDocs/windowsserverdocs/blob/main/WindowsServerDocs/administration/windows-server-update-services/manage/wsus-and-the-catalog-site.md
- To find out IF you have to change something regarding TLS or SchUseStrongCrypto just download the PS and run following command from Powershell where you downloaded the script. If you have a Server 2016 that may already work as it is.
|
Try out if you are need to change TLS or SchUseStrongCrypto run this command where you downloaded the PS |
|
.\ImportUpdateToWSUS.ps1 -UpdateId f2aaaf6d-b74b-4b64-aa72-535b1831124c |
If all went fine and NO red error YOU can direct go to the STEP how to import the “IMPORT the out of band patches into WSUS” in this post.
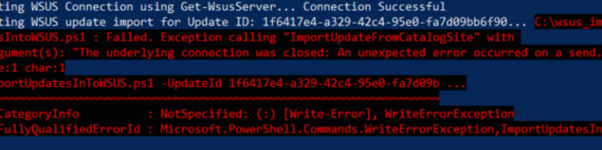
IF you see following error (Probaly on SRV 2019 or 2022 OS) you need to change some TLS or SchUseStrongCrypto in a first step.
|
|
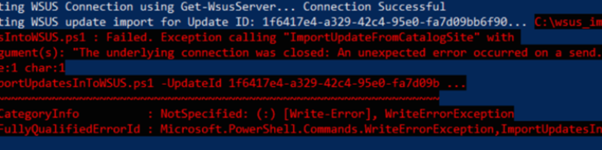
|
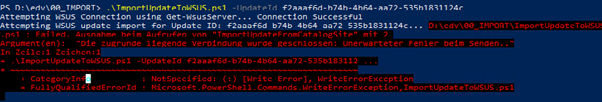
PS D:\edv\00_IMPORT> .\ImportUpdateToWSUS.ps1 -UpdateId f2aaaf6d-b74b-4b64-aa72-535b1831124c Attempting WSUS Connection using Get-WsusServer… Connection Successful Attempting WSUS update import for Update ID: f2aaaf6d-b74b-4b64-aa72-535b1831124c… D:\edv\00_IMPORT\ImportUpdateToWSUS.ps1 : Failed. Ausnahme beim Aufrufen von “ImportUpdateFromCatalogSite” mit 2 Argument(en): “Die zugrunde liegende Verbindung wurde geschlossen: Unerwarteter Fehler beim Senden..” In Zeile:1 Zeichen:1 + .\ImportUpdateToWSUS.ps1 -UpdateId f2aaaf6d-b74b-4b64-aa72-535b183112 … + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : NotSpecified: (:) [Write-Error], WriteErrorException + FullyQualifiedErrorId : Microsoft.PowerShell.Commands.WriteErrorException,ImportUpdateToWSUS.ps1 |
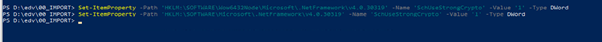
ONLY: If you see ABOVE error then you need to change SchUseStrongCrypto
for Microsoft .net 4 Framework. Do this with follwing command which will also reboot the server automatic.
|
Change SchUseStrongCrypto for .net 4 32/64BIT for Server 2019/2022 |
|
Set-ItemProperty -Path ‘HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NetFramework\v4.0.30319’ -Name ‘SchUseStrongCrypto’ -Value ‘1’ -Type DWord Set-ItemProperty -Path ‘HKLM:\SOFTWARE\Microsoft\.NetFramework\v4.0.30319’ -Name ‘SchUseStrongCrypto’ -Value ‘1’ -Type DWord Restart-Computer |
|
|
|
Or with a Registry patch. Save to “strong.reg” and doubleclick file. |
|
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319] “SchUseStrongCrypto”=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319] “SchUseStrongCrypto”=dword:00000001 |
|
reg.exe add “HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319” /v “SchUseStrongCrypto” /t REG_DWORD /d 1 /f
reg.exe add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319” /v “SchUseStrongCrypto” /t REG_DWORD /d 1 /f |
IMPORT all the out of band patches into WSUS
You have Server 2016 and did see no RED Powershell ERRROR with the try above OR you have SRV2019 and SRV 2022 and did FIX the SchUseStrongCrypto and did the Reboot. Then retry the import of all patches.
RUN:
.\ImportUpdateToWSUS.ps1 -UpdateId f2aaaf6d-b74b-4b64-aa72-535b1831124c
.\ImportUpdateToWSUS.ps1 -UpdateId e2d5822a-19f1-4f96-95ad-3974a58f0a00
.\ImportUpdateToWSUS.ps1 -UpdateId 0683858a-06db-4f1a-b1eb-6ba0998d83f0
.\ImportUpdateToWSUS.ps1 -UpdateId 1bc3fe3f-74dc-48da-a3f3-65a6c06f4335
.\ImportUpdateToWSUS.ps1 -UpdateId b40feb45-69fa-4ed7-aff2-608a93c9512f
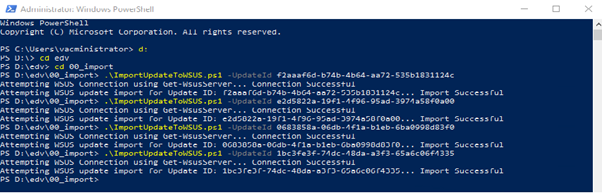
You will see the mentioned Updates in WSUS Server.
You can check with PS on the WSUS if they are there:
(Get-WsusServer).SearchUpdates(‘KB5037426’)
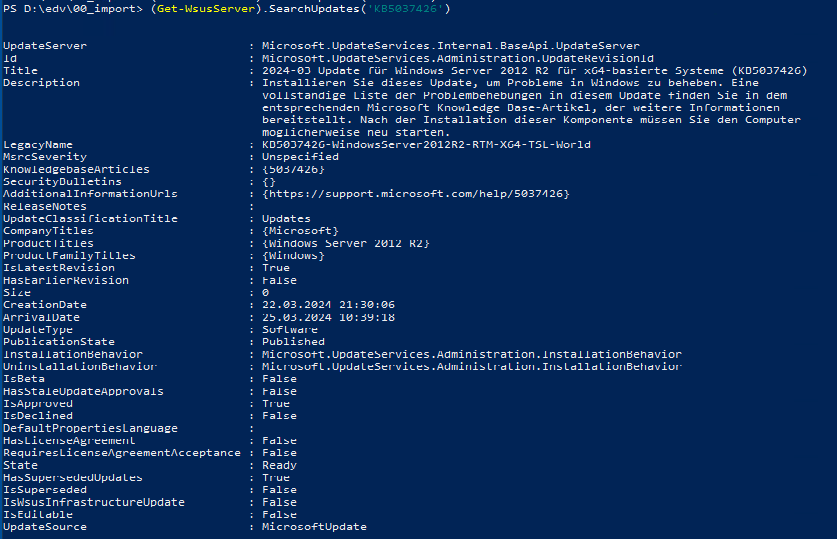
If you still have the RED error in PS:
- Run the PS on the WSUS itself
- Play around with options for the script for Port 8530 and 8531 and SSL
- Check Certificate Revovation CRL and Firewall on the Server with our tool crlcheck.exe, CRLcheck.exe Certificate Revocation List Check Tool to verify all CRL and OCSP on Windows client – www.butsch.ch | https://www.butsch.ch/post/crlcheck-exe-certificate-revocation-list-check-tool-to-verify-all-crl-and-ocsp-on-windows-client/
- TRY 127.0.0.1 as WSUS in the script
- Download Nartac Software – IIS Crypto | https://www.nartac.com/Products/IISCrypto/ choose best pratice and reboot the Server (Yes, it works on SRV 2022 also).
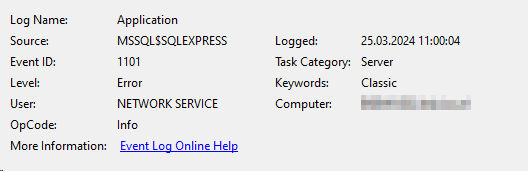
- Check Events or Server for 1827 or 1101 > Make sure you have NOT reached the limit of the WID or SQL Express Database (See below)
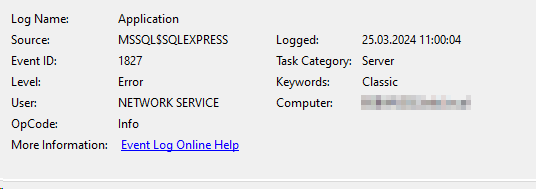
CREATE DATABASE or ALTER DATABASE failed because the resulting cumulative database size would exceed your licensed limit of 10240 MB per database.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.