14.05.2017, Good News MS Release KB4012598 for XP/VISTA/2003 (32/64) BIT and you can patch your old special machines.
14:05.2017, Most of Swiss Media inlcuding SFDRS sf.tv (Swiss TV) did mention that they are no current infections to date in switzerland.
We think that’s wrong and as normal the corporate who are infected keep that under the hood. It’s possible because we have seen
Ransomware in the past which checks Country and keyboard codes of the OS and does only run in certain countrys.
One other Problem is that large enterprise often RENT IP-Subnets (Like people with AS-Records) from global ISP and their Source-IP is often extra hidden or in another country.
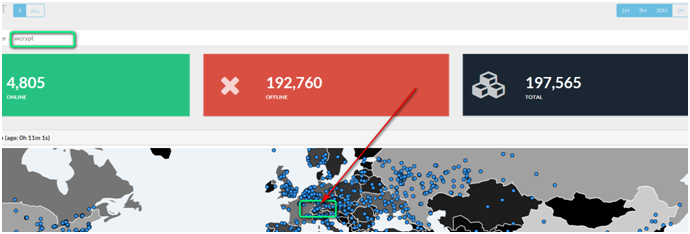
If we asume that https://intel.malwaretech.com/botnet/wcrypt/?t=1h&bid=all does Analyse the URL request he get’s in on his domain
We can say that there are infections in Switzerland. Around EVERY second when not more customer was hit by Ransomware the last
12 months in switzerland. Criminials know where to ski in the winter, buy nice watches and where to steal money. Ther more Expat CEO and managers
who never understood a single part of IT-security the more money you can do with Ransomware in Switzerland. So yes switzerland i a pretty good place to run ransomwre.
Status Switzerland, Europe WANNA infections 13.05.2017 around 23:45 o’clock. Check the blue dots in Zürich.
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
Microsoft solution available to protect additional products
Today many of our customers around the world and the critical systems they depend on were victims of malicious “WannaCrypt” software. Seeing businesses and individuals affected by cyberattacks, such as the ones reported today, was painful. Microsoft worked throughout the day to ensure we understood the attack and were taking all possible actions to protect our customers. This blog spells out the steps every individual and business should take to stay protected. Additionally, we are taking the highly unusual step of providing a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003. Customers running Windows 10 were not targeted by the attack today.
Details are below.
-
In March, we released a security update which addresses the vulnerability that these attacks are exploiting. Those who have Windows Update enabled are protected against attacks on this vulnerability. For those organizations who have not yet applied the security update, we suggest you immediately deploy Microsoft Security Bulletin MS17-010.
-
For customers using Windows Defender, we released an update earlier today which detects this threat as Ransom:Win32/WannaCrypt. As an additional “defense-in-depth” measure, keep up-to-date anti-malware software installed on your machines. Customers running anti-malware software from any number of security companies can confirm with their provider, that they are protected.
We also know that some of our customers are running versions of Windows that no longer receive mainstream support. That means those customers will not have received the above mentioned Security Update released in March. Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download (see links below).
This decision was made based on an assessment of this situation, with the principle of protecting our customer ecosystem overall, firmly in mind.
Some of the observed attacks use common phishing tactics including malicious attachments. Customers should use vigilance when opening documents from untrusted or unknown sources. For Office 365 customers we are continually monitoring and updating to protect against these kinds of threats including Ransom:Win32/WannaCrypt. More information on the malware itself is available from the Microsoft Malware Protection Center on the Windows Security blog. For those new to the Microsoft Malware Protection Center, this is a technical discussion focused on providing the IT Security Professional with information to help further protect systems.
We are working with customers to provide additional assistance as this situation evolves, and will update this blog with details as appropriate.
Phillip Misner, Principal Security Group Manager Microsoft Security Response Center
Further resources:
Download English language security updates: Windows Server 2003 SP2 x64, Windows Server 2003 SP2 x86,
Windows XP SP2 x64, Windows XP SP3 x86, Windows XP Embedded SP3 x86, Windows 8 x86,
Windows 8 x64
To download localized versions for the security update for Windows XP, Windows 8 or Windows Server: http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
General information on ransomware: https://www.microsoft.com/en-us/security/portal/mmpc/shared/ransomware.aspx
MS17-010 Security Update: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Tags cyberattacks
Microsoft Windows
ransomware
Security Update
Windows
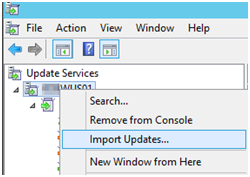
Here is how to integrate the special Patch for XP/VISTA/2003 in your WSUS via Windows Update Catalog (With all possible errors with Ie11 on your Server 😉
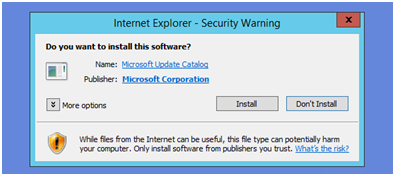
If this comes up please Install
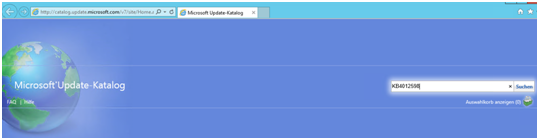
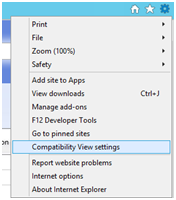
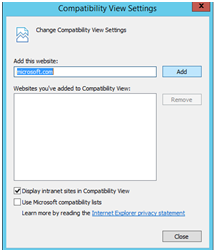
If you see this error in the Windows Update catalog. Add the Microsoft.com to the Compatiblity Mode. It’s really das that MS does not do that theirself.. ;-(
If you see error below > Try again (Windows Update down) or add the site Microsoft.com into comptiblity mode on the WSUS Server.
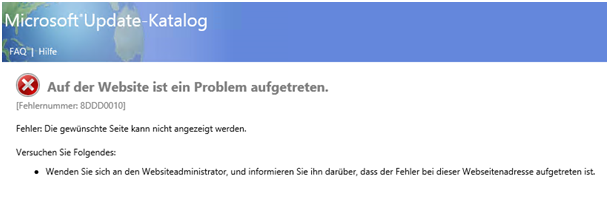
fehlernummer 8ddd0010
Now search again for KB4012598 and choose your supported platforms:
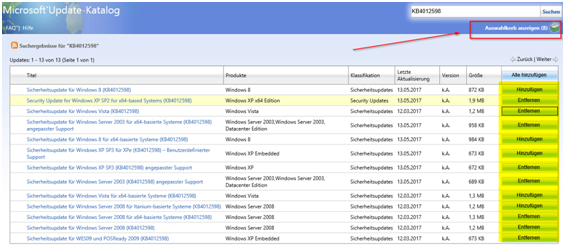
Choose herunterladen/Download
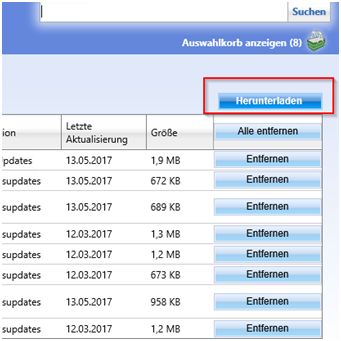
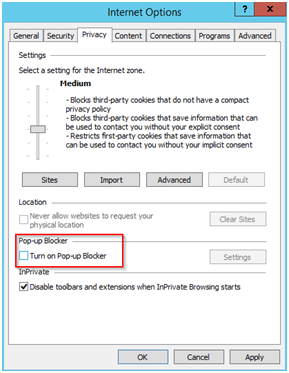
If the Basket does not Appear turn of POPUP blocker
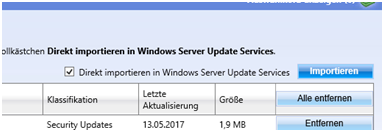
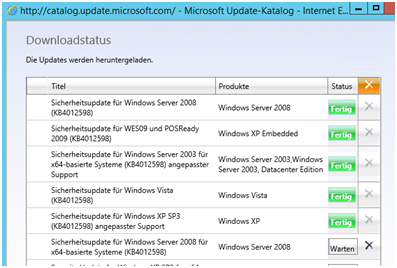
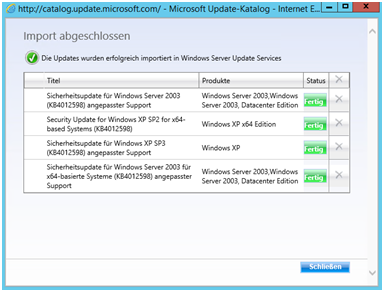
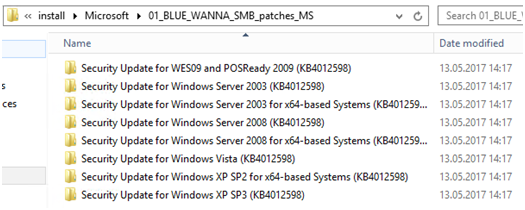
Here we go 😉
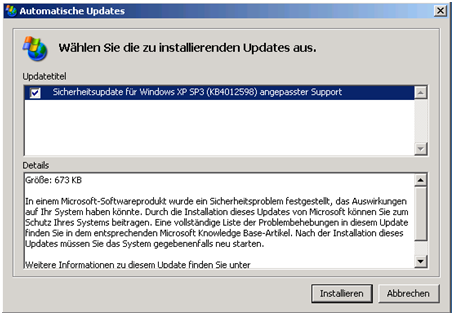
Server 2003 😉 Don’t laugh it’s a 2003 we use to edit a Gpo Setting that was made
For IE9 but still is valid for IE11 in IEAK 11. So you need a) And old Server/Client, an Old Browser to modify those Proxy settings.
Dont believe it? https://www.butsch.ch/post/Internet-Explorer-911-GPO-old-IE9-not-visible-WMI-checks.aspx
Regarding blocking the Extension.
For mcafee customers Please read:


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.