
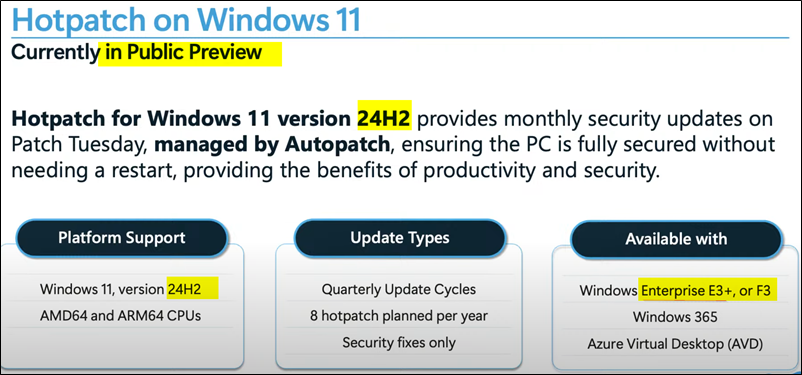
Hotpatching is coming to Windows 11 24H2 Enterprise E3+. Users will be able to patch “Security ONLY” updates on Patch Tuesday without requiring a reboot each time.
- W11 Hotpatch only available for Windows Enterprise E3 or E5 (e.g. Microsoft 365 A3/A5 or Microsoft 365 F3); or a Windows 365 Enterprise subscription.
- Windows 11 version 24H2 LTSC supported
- .NET updates are not covered by hotpatching. If a .NET update requires a reboot, the system will need to restart just as it would outside of hotpatching.
- For M365 Intune AutoPatching, you just need to change ONE slider to “Hotpatch.” It will auto-patch existing W10/W11 until 24H2, but also the new 24H2 with the same policy (auto-decide).
That sounds nice but….
You neeed to activate VBS (Virtualization-Based Security) so hotpatch will work
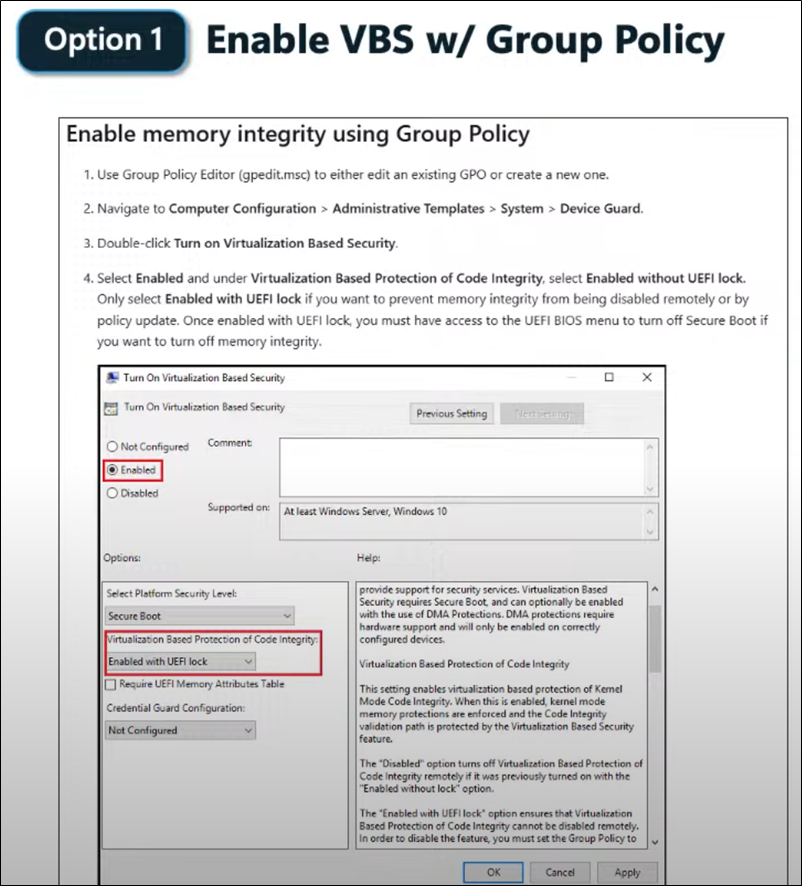
- You need to enable VBS (Virtualization-Based Security) via GPO, a single Registry Key, or through the Windows client GUI itself (see screenshots or the link in the post for how to enable and verify that you meet the prerequisites at the end of the post).
- New Windows 11 install, version 24H2 PCs will have VBS enabled by default. CLient upgraded to Windows 11 24H2 will maintain the older OS’s VBS config state
- VBS does not require nested virtualization support. It can work in Guest mode too. But you will need a hypervisor that can 1) Expose Virtual Trust Levels (VTLs) interfaces (which do not exist other than HyperV) OR 2) Create a VM with nested virtualization support
-
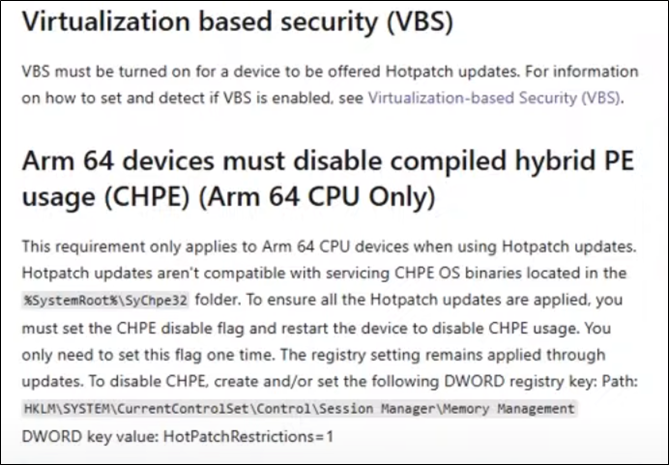
There are things to consider when running VBS on ARM architecture hardware (Q4/2024 and Q1/2025 models). Like most security products, you need to be careful or get a special version of agents, etc.
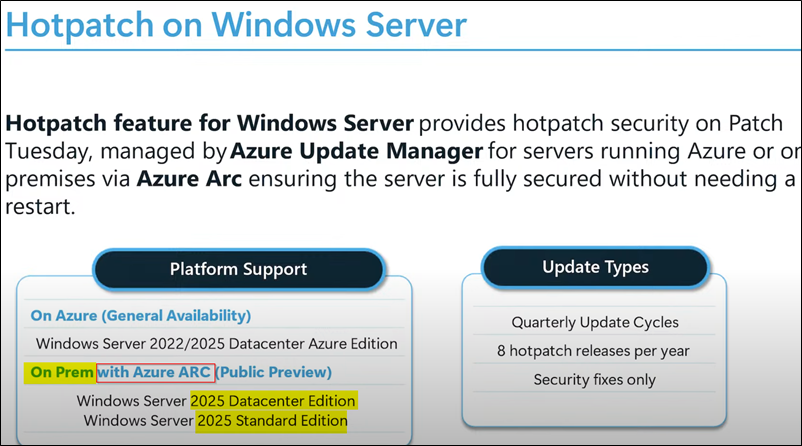
- For Server 2025 on-premises, you need “Azure ARC” (https://learn.microsoft.com/en-us/azure/azure-arc/overview)
- For Azure Arc connected servers, hotpatching is only applicable for Server 2025 and there is no ongoing plan to support Server 2022.
Can you uninstall the Hotpatch?
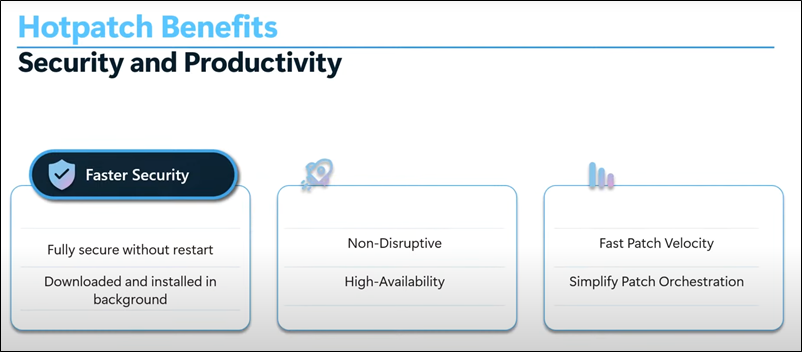
- We understand that reliability is a top concern when applying updates. Hotpatching is designed to minimize disruptions by applying security updates without requiring a reboot. However, if an issue arises, there are multiple safeguards in place:
- Rollback via Uninstall – Hotpatches can be uninstalled individually if needed. After rollback, users can install the standard cumulative update and reboot the device to ensure they remain secure.
- Safe Deployment Practices – Microsoft thoroughly tests hotpatches before release, and customers can validate them in a test environment before broad deployment.
From our side we guess Azure Virtual Desktop VDA was one of the reasons MS spent some time in Hotpatch. Imagine around patchtuesday when you patch millions of VDI desktop? If you can do that without a reboot this may help to keep down storage and power.
Hotpatching for Windows 11 24H2 is only available for Windows Enterprise E3 or E5 (e.g. Microsoft 365 A3/A5 or Microsoft 365 F3); or a Windows 365 Enterprise subscription.
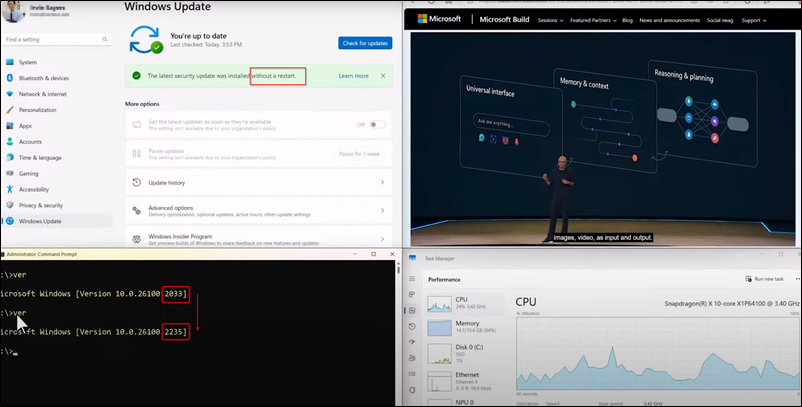
In the sample shown during the MS webcast the user did watch a video and client installed a Windows Update without interrupting the stream. CPU peak looked good we will see how that is goin on effective clients.
Hotptach for Windows 11 24H2 needs Windows Enterprise E1+ or F3 OS version or Windows 365 and this may have been the main reason
for them doing it “Azure Virtual Desktop [AVD]” You can imagine the traffic storage peak on their side when Millions of AVD reboot around patchday?
Hands on view to add Hotpatch to your existing Autiopatch Policy in M35 Intunes
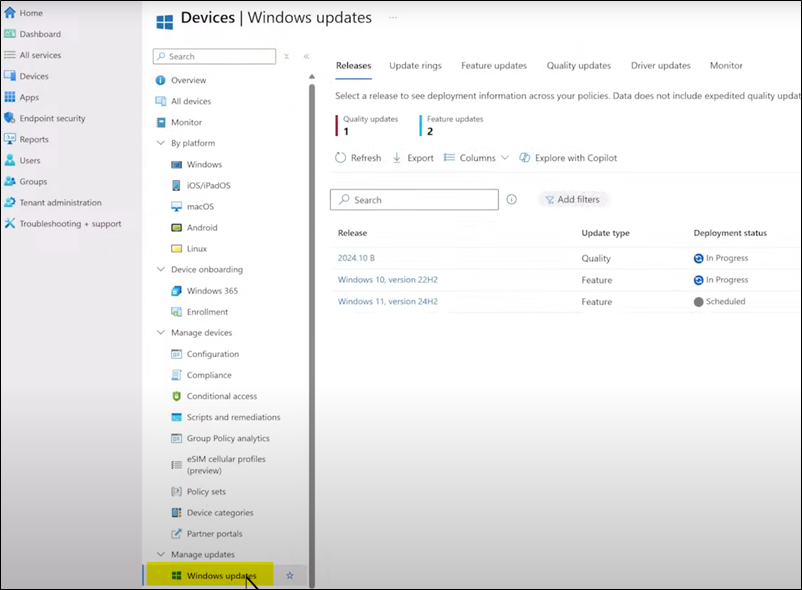
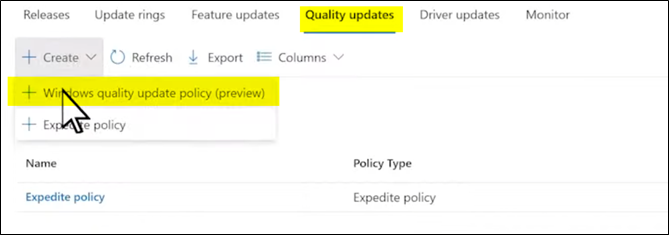
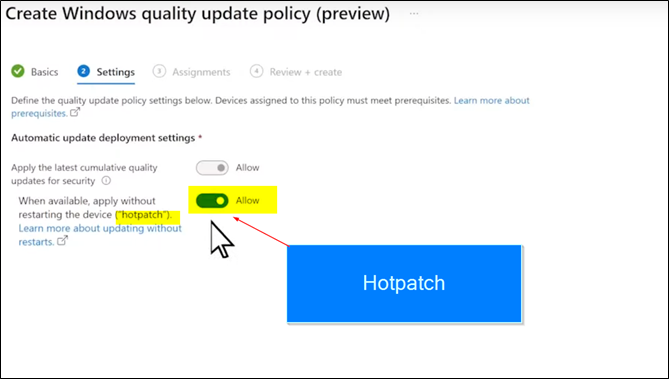
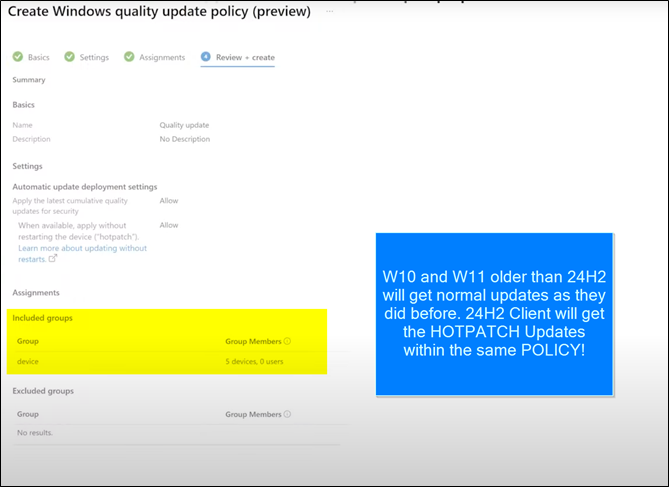
Client side view
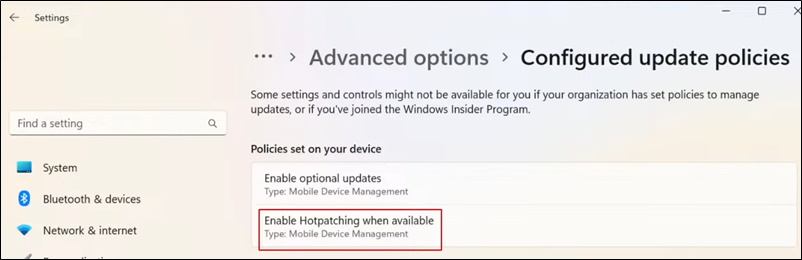
To make a device HOTPATCH compatible you need to enable VBS (Virtualization Based Security)
https://learn.microsoft.com/en-us/windows-hardware/design/device-experiences/oem-vbs
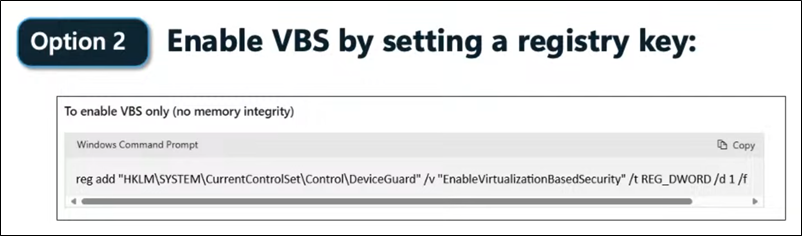
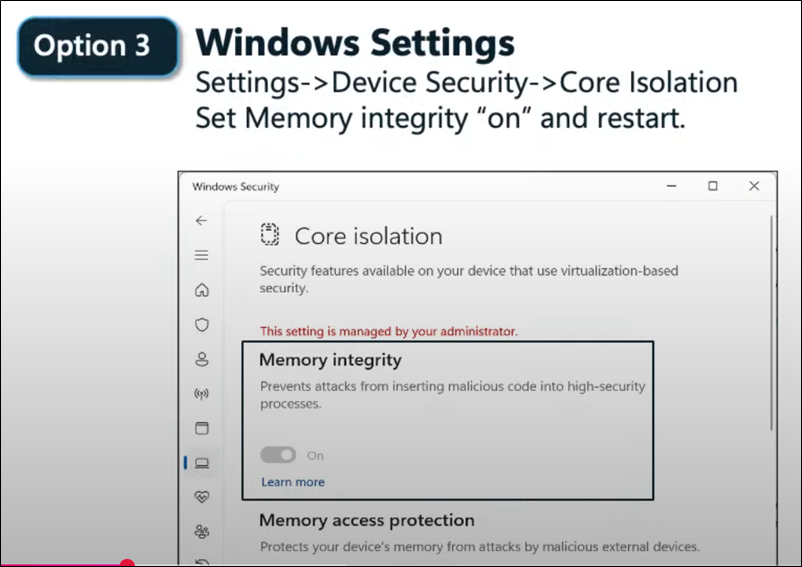
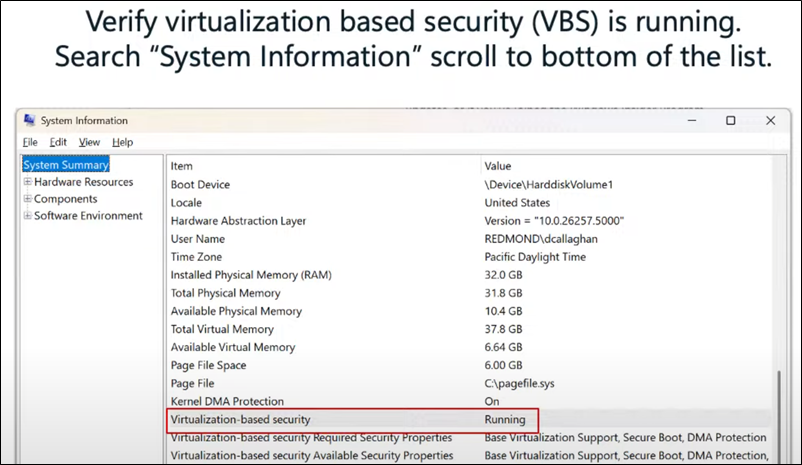
If you have ARM devices (The new clients) make sure you read all about it before trying there. We will not mention in detail because you need as exmaple a special version of Forticlient and also just for example as special Release
From Mcafee/Trellix ENS Protection just for the ARM machines. If you like trouble go ahead maybe with BYOD customers that will show up earlier or if you have customer buying their own hardware.
But we don’t want to secure Amiga and Atatri ST right? SO that is more political there…
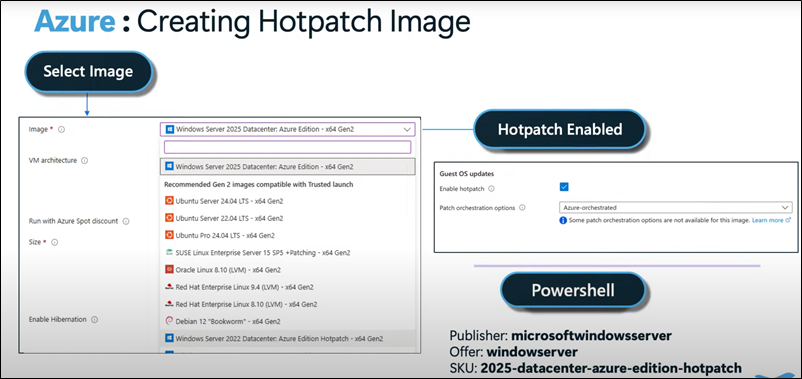
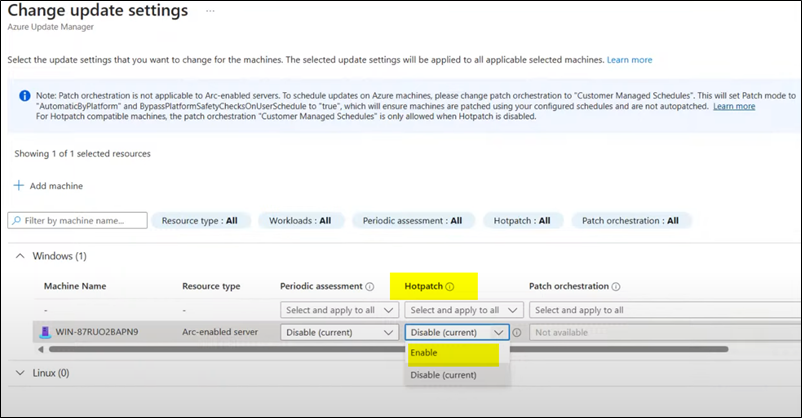
Server Hotpatch
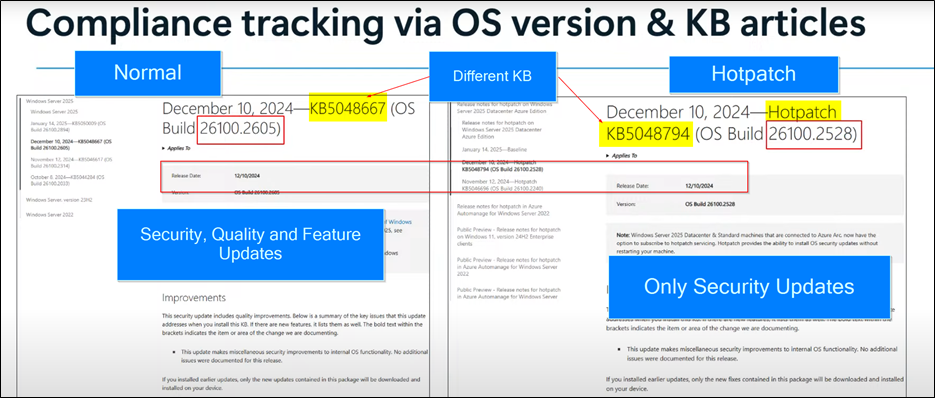
KB-Release Sample / Difference between two updates (Notice different KB for the regular patch and the Hotpatch)
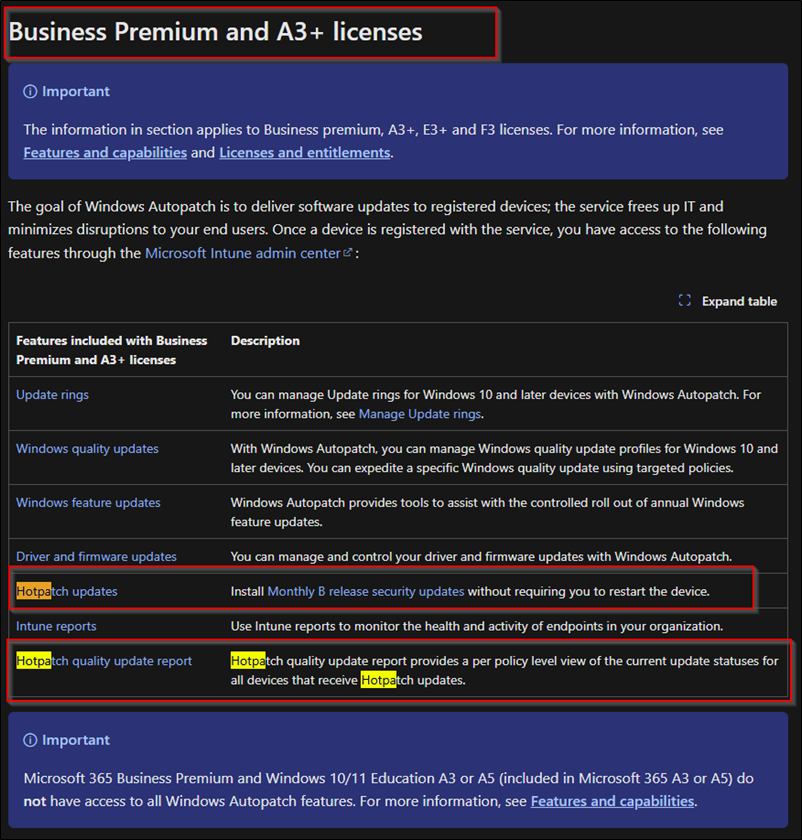
A3+ Licences for W11
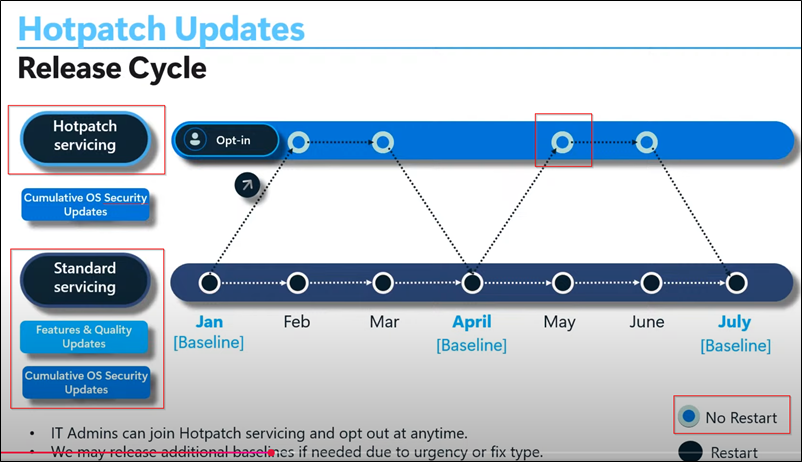
VBS Details to watch:
Virtualization-based Security (VBS)
VBS requires the following components be present and properly configured.
Expand table
|
Hardware requirement |
Details |
|
64-bit CPU |
Virtualization-based security (VBS) requires the Windows hypervisor, which is only supported on 64-bit IA processors with virtualization extensions, including Intel VT-X and AMD-v. |
|
Second Level Address Translation (SLAT) |
VBS also requires that the processor’s virtualization support includes Second Level Address Translation (SLAT), either Intel VT-X2 with Extended Page Tables (EPT), or AMD-v with Rapid Virtualization Indexing (RVI). |
|
IOMMUs or SMMUs (Intel VT-D, AMD-Vi, Arm64 SMMUs) |
All I/O devices capable of DMA must be behind an IOMMU or SMMU. An IOMMU can be used to enhance system resiliency against memory attacks. |
|
Trusted Platform Module (TPM) 2.0 |
For more information, see Trusted Platform Module (TPM) 2.0. |
|
Firmware support for SMM protection |
System firmware must adhere to the recommendations for hardening SMM code described in the Windows SMM Security Mitigations Table (WMST) specification. The WSMT specification contains details of an ACPI table that was created for use with Windows operating systems that support VBS features. Firmware must implement the protections described in the WSMT specification, and set the corresponding protection flags as described in the specification to report compliance with these requirements to the operating system. |
|
Unified Extensible Firmware Interface (UEFI) Memory Reporting |
UEFI firmware must adhere to the following memory map reporting format and memory allocation guidelines in order for firmware to ensure compatibility with VBS. UEFI v2.6 Memory Attributes Table (MAT) – To ensure compatibility with VBS, firmware must cleanly separate EFI runtime memory ranges for code and data, and report this to the operating system. Proper segregation and reporting of EFI runtime memory ranges allows VBS to apply the necessary page protections to EFI runtime services code pages within the VBS secure region. Conveying this information to the OS is accomplished using the EFI_MEMORY_ATTRIBUTES_TABLE. To implement the UEFI MAT, follow these guidelines:
EFI Page Protections –All entries must include attributes EFI_MEMORY_RO, EFI_MEMORY_XP, or both. All UEFI memory that is marked executable must be read only. Memory marked writable must not be executable. Entries may not be left with neither of the attributes set, indicating memory that is both executable and writable. |
|
Secure Memory Overwrite Request (MOR) revision 2 |
Secure MOR v2 is enhanced to protect the MOR lock setting using a UEFI secure variable. This helps guard against advanced memory attacks. For details, see Secure MOR implementation. |
|
Memory integrity-compatible drivers |
Ensure all system drivers have been tested and verified to be compatible with memory integrity. The Windows Driver Kit and Driver Verifier contain tests for driver compatibility with memory integrity. There are three steps to verify driver compatibility:
|
|
Secure Boot |
Secure Boot must be enabled on devices leveraging VBS. For more information, see Secure Boot |
Links Hotpatch:
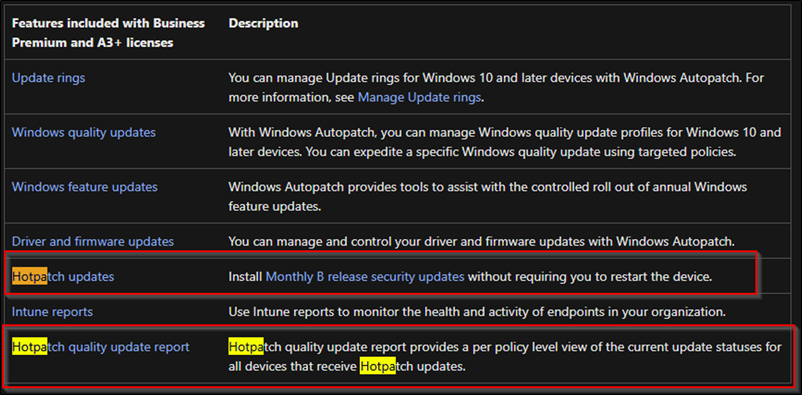
- Hotpatch updates
- Release notes for hotpatch public preview on Windows 11, version 24H2 Enterprise clients
- Release notes: Windows 11, version 24H2 – December 10, 2024 – KB5048667
- December 10, 2024—Hotpatch public preview KB5048794 (OS Build 26100.2528)
- aka.ms/GetHotpatch
- Release notes for Hotpatch on Windows Server 2025 Datacenter Azure Edition
- Skilling snack: Hotpatch on Windows client and server


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.