Windows Server 2019
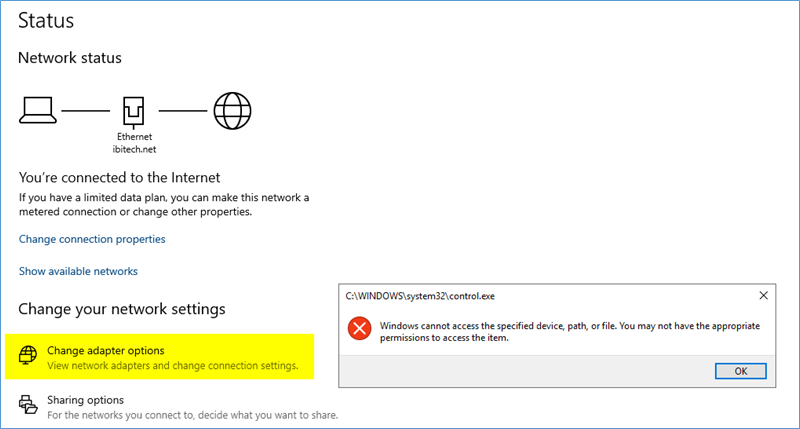
Windows cannot access the specified device, path, or file. You may not have the appropriate permissions to access the item

Reason is this local GPO on the Server:
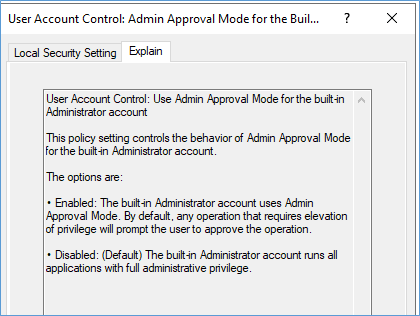
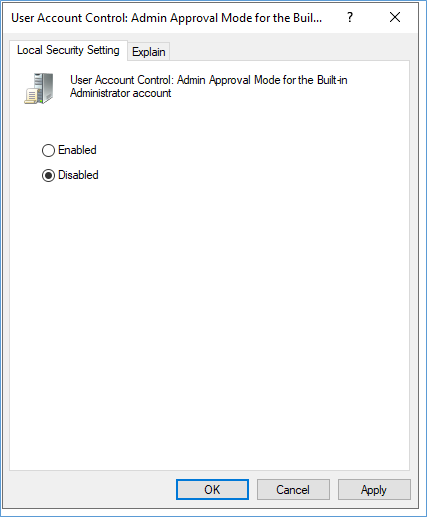
User Account Control: Admin Approval Mode for the Built-in Administrator account
If you follow the process below with gpedit.msc you WILL FIND OUT
That this NOT a permanent solution because you always get blocked with UAC
On everything you do on the DC. So maybe use direct calls would be better.
Shortcuts to open the things direct via cmd.exe or run.
|
Command |
Opens |
|
control |
Control Panel |
|
control firewall.cpl |
Windows Defender Firewall |
|
control ncpa.cpl |
Network Connections |
|
control appwiz.cpl |
Programs and Features |
|
control desk.cpl |
Display Settings |
|
control hdwwiz.cpl |
Add Hardware Wizard |
|
control timedate.cpl |
Date and Time Settings |
|
control intl.cpl |
Region and Language Settings |
|
control sysdm.cpl |
System Properties |
|
control powercfg.cpl |
Power Options |
|
control mmsys.cpl |
Sound Settings |
|
control keyboard |
Keyboard Settings |
|
control mouse |
Mouse Settings |
|
control printers |
Devices and Printers |
Sample of the error:
gpedit.msc
User Account Control: Admin Approval Mode for the Built-in Administrator account | Microsoft Learn
Possible values
Enabled
The built-in Administrator account logs on in Admin Approval Mode so that any operation that requires elevation of privilege displays a prompt that provides the administrator the option to permit or deny the elevation of privilege.
Disabled
The built-in Administrator account logs on in Windows XP Mode, and it runs all applications by default with full administrative privileges.
Best practices
Do not enable the built-in Administrator account on the client computer, but use the Standard User account and User Account Control (UAC).
Location
GPO_name\Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
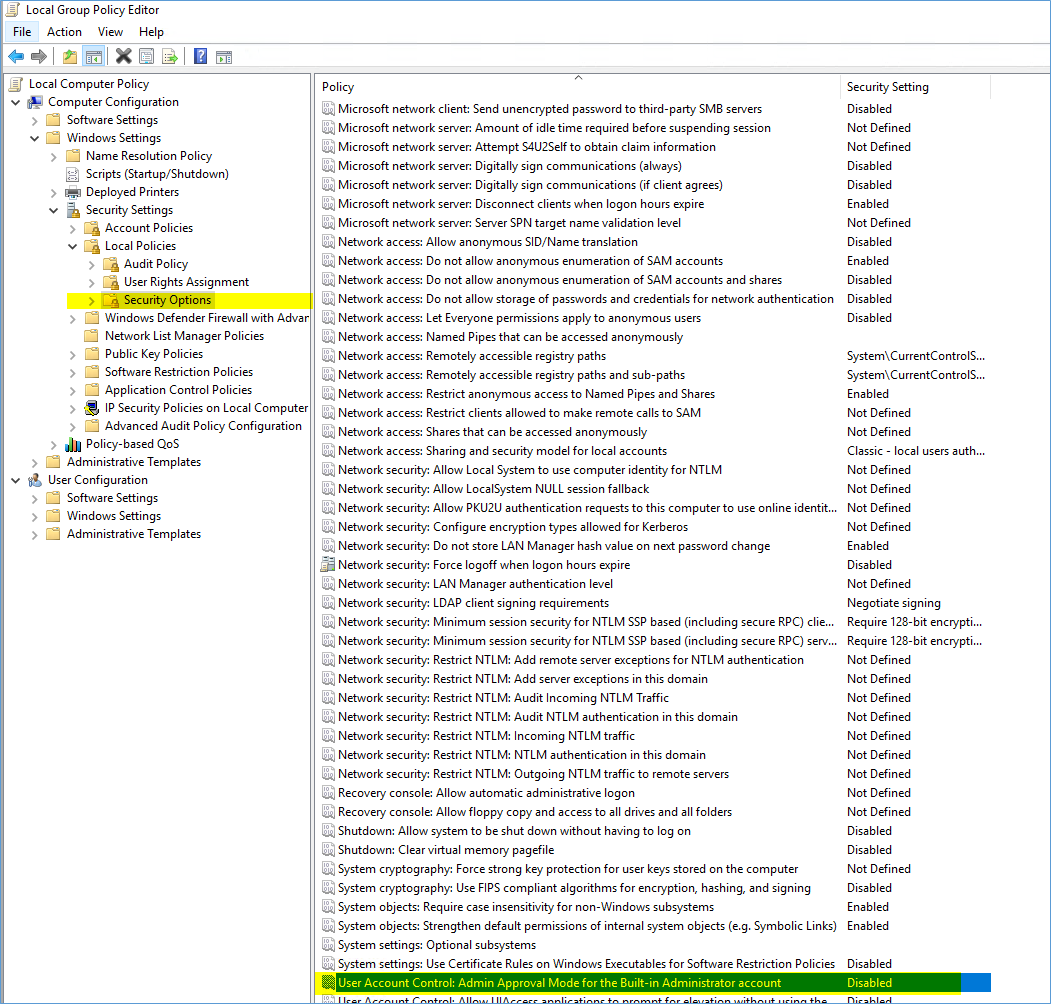
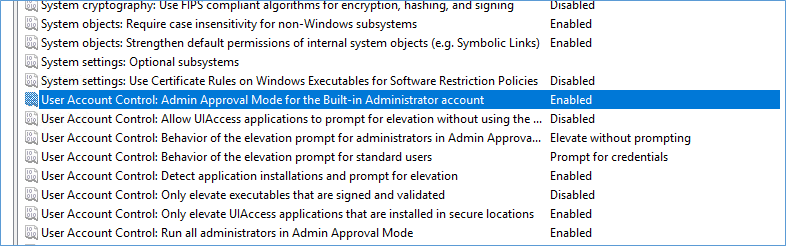
Reboot
NOW this will SOLVE the one error BUT you have NOW UAC active for built in accounts. This looks like this and almost impossible to work productive on a server in that way.
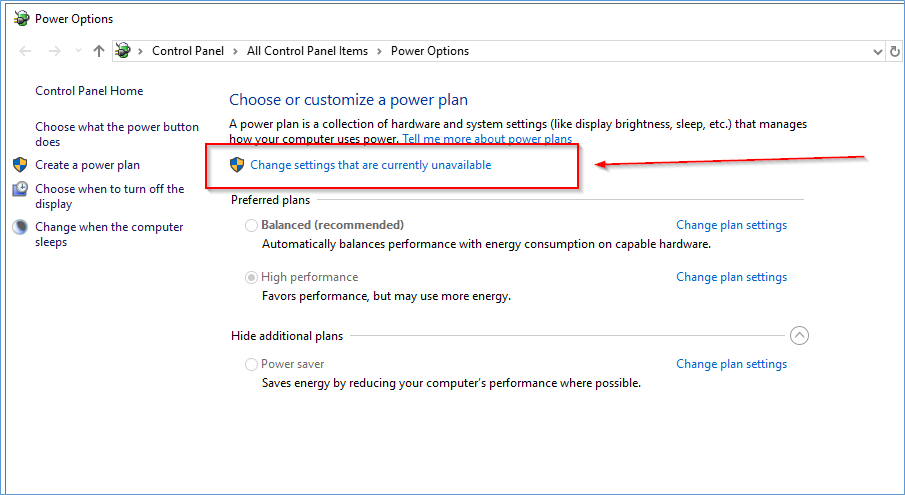
After you click the elevated UAC symbol
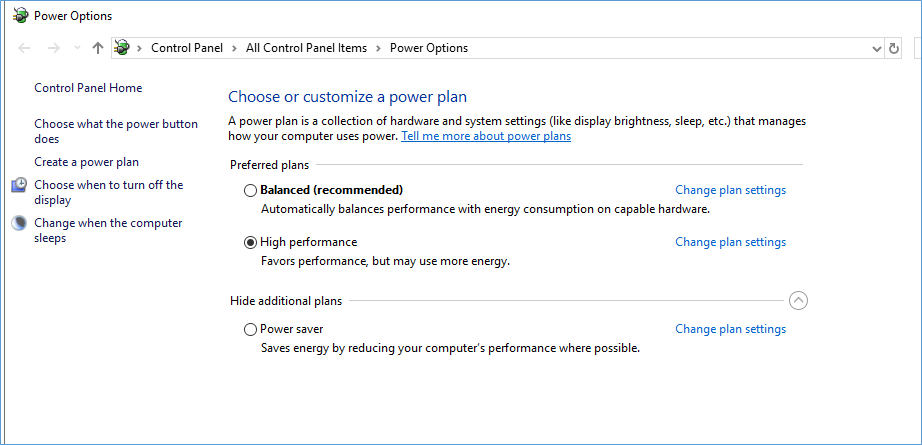
Change it back maybe if you don’t need to access those settings anymore and server setup is done and ready?


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.