Problems with Microsoft EDGE Chromium V125 Browser closes on W11 just after you open it
We had some people, including IT, reporting that after they updated to Microsoft Edge Chromium V125 Stable through WSUS on 22.05.2024, they could not start the browser anymore. Any repair attempt failed. The only solution we found this morning on one machine was to download the Beta 125 or Dev 126 Preview version. We did not have any more time to invest in this issue. People on the same domain/network/VLAN did not have any problems with physical or VM/VDI machines with V125. We are unsure if this has been related to the TLS CIPHER change that EDGE CHROMIUM also changed the last few weeks. (Google chrome 124 and Edge Chromium Probleme Webserver SSL-Brechen [DEU] – www.butsch.ch | https://www.butsch.ch/post/google-chrome-124-and-edge-chromium-probleme-webserver-ssl-brechen-deu/)
The affected IT person had an HP laptop with Windows 11 at their home office. Perhaps certificate revocation is blocked in the home office, but we did not have more time to investigate.
Quick Workaround they found number 1:
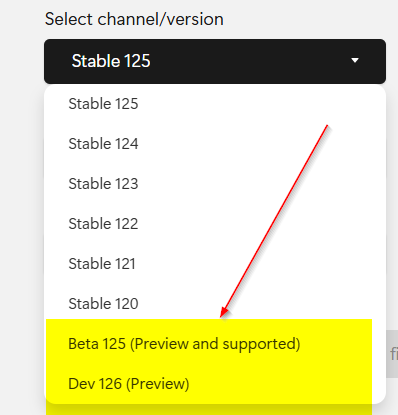
Download Edge for Business (microsoft.com)
https://www.microsoft.com/en-us/edge/business/download?form=MA13FJ
choose the “BETA” if that does not work use the early adapter “DEV”
Other people seeing this but had that earlier while using the BETA AND DEV as standard browser: (Clearly they where hit earlier by the BUG)
Quick Workaround they found number 2:
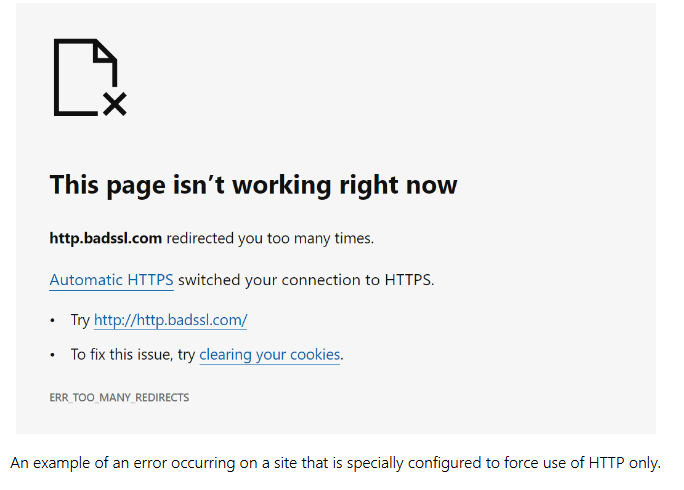
We are unsure if this may be related to the start page the users have and if the start page is http:// not https:// or if they have SECURE DNS turned ON somehow if YOU set the key below it will turn of secure DNS.
Registry HKCU / HKLM
[HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Edge]
“AutomaticHttpsDefault”=dword:00000002
|
GPO Policy Microsoft Edge Browser Policy Documentation | Microsoft Learn https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies |
|
AutomaticHttpsDefault Configure Automatic HTTPS Supported versions: On Windows and macOS since 92 or later Description This policy lets you manage settings for AutomaticHttpsDefault, which switches connections from HTTP to HTTPS.
This feature helps protect against man-in-the-middle attacks by enforcing more secure connections, but users might experience more connection errors.
Microsoft Edge attempts to upgrade some navigations from HTTP to HTTPS, when possible. This policy can be used to disable this behavior. If set to “AlwaysUpgrade” or left unset, this feature will be enabled by default.
The separate HttpAllowlist policy can be used to exempt specific hostnames or hostname patterns from being upgraded to HTTPS by this feature.
Starting in Microsoft Edge 111, “UpgradePossibleDomains” is deprecated and is treated the same as “DisableAutomaticHttps”. It won’t work in Microsoft Edge version 114.
Policy options mapping:
DisableAutomaticHttps (0) = Automatic HTTPS functionality is disabled.
UpgradeCapableDomains (1) = (Deprecated) Navigations delivered over HTTP are switched to HTTPS, only on domains likely to support HTTPS.
AlwaysUpgrade (2) = All navigations delivered over HTTP are switched to HTTPS. Connection errors might occur more often.
Use the preceding information when configuring this policy.
Supported features: Can be mandatory: Yes Can be recommended: Yes Dynamic Policy Refresh: Yes Per Profile: Yes Applies to a profile that is signed in with a Microsoft account: Yes Data Type: Integer Windows information and settings Group Policy (ADMX) info GP unique name: AutomaticHttpsDefault GP name: Configure Automatic HTTPS GP path (Mandatory): Administrative Templates/Microsoft Edge/ GP path (Recommended): Administrative Templates/Microsoft Edge – Default Settings (users can override)/ GP ADMX file name: MSEdge.admx Windows Registry Settings Path (Mandatory): SOFTWARE\Policies\Microsoft\Edge Path (Recommended): SOFTWARE\Policies\Microsoft\Edge\Recommended Value Name: AutomaticHttpsDefault Value Type: REG_DWORD
Example value:
0x00000002 Mac information and settings Preference Key Name: AutomaticHttpsDefault Example value: XML
<integer>2</integer> Back to top |
NOTE: If you were using “secure DNS,” it will be disabled by this! This can, undoubtedly, also be corrected with a policy (i.e., the resulting registry value), but I have not investigated this further.
NOTE: Edge cached that. Clearing all browser history solved this problem (if you experiment yourself, regularly clear the browser history)
Here are the locations mentioned:
Path (Mandatory): SOFTWARE\Policies\Microsoft\Edge
Path (Recommended): SOFTWARE\Policies\Microsoft\Edge\Recommended
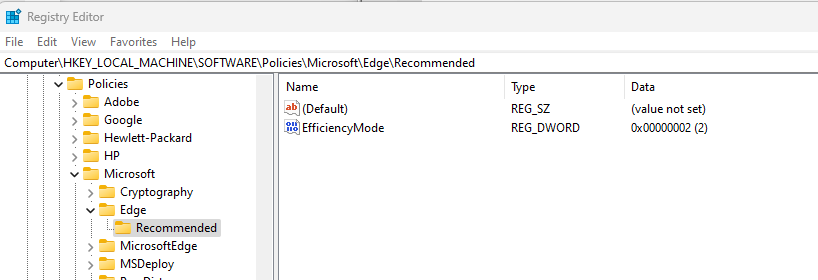
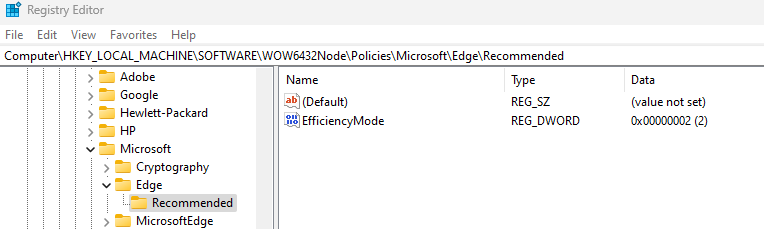
The Registry KEY AutomaticHttpsDefault
leads us to followinh change:
We are unsure at the moment if this has anything to with this option which came in V92 and has been redone.
When sites are loaded over HTTP, attackers can view or change page content in transit, or redirect you to a different location than you had expected. Most websites now support HTTPS, which can help protect against these man-in-the-middle attacks. However, too many of these sites aren’t configured to require HTTPS, leaving open a short window of opportunity for attackers before the site can redirect to the more secure protocol. Some sites may not redirect visits from HTTP to HTTPS at all, leaving some visitors with a less secure connection. To help protect your information as you browse, we are introducing a feature called Automatic HTTPS: now available for preview in Canary and Developer channels with Microsoft Edge 92.
Automatic HTTPS switches your connections to websites from HTTP to HTTPS on sites that are highly likely to support the more secure protocol. The list of HTTPS-capable websites is based on Microsoft’s analysis of the web, and helps enable a more secure connection on hundreds of thousands of top domains. Automatic HTTPS upgrades your connection only on HTTPS-capable domains by default in order to prevent connection errors and potential performance issues.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.