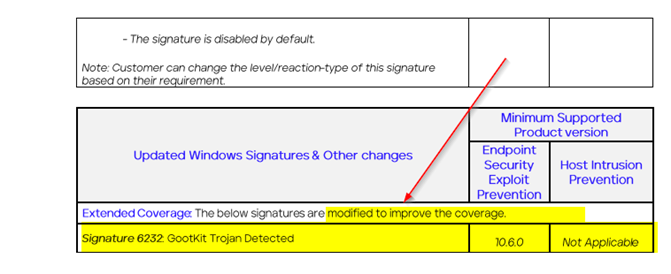
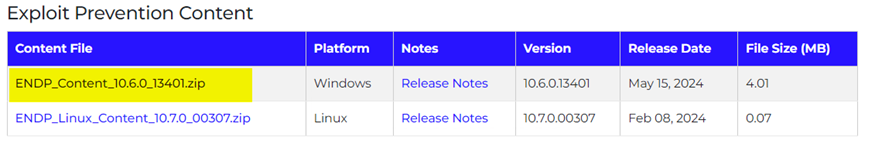
Mcafee/Trellix ENS 10.7 Exploit Prevention Content 13401 Update SIG 6232 from 15.05.2024 brought a false with some customers from us. This comes with good (change) or bad (false) timing after we have seen some Gootloader activity happening in EU/CH these days.
This happens on ENS 10.7 APRIL 2024 and also on Nov 2023 Version
OS W10/W11 DE/EN/OEM/VL/LTSC all affected
|
Produktversion (Endpoint Security Platform) |
10.7.0.6809 |
|
Produktversion (Endpoint Security Threat Prevention) |
10.7.0.6711 |
|
Produktversion (Endpoint Security Advanced Threat Protection ATP) |
10.7.0.6887 |
PROOF:
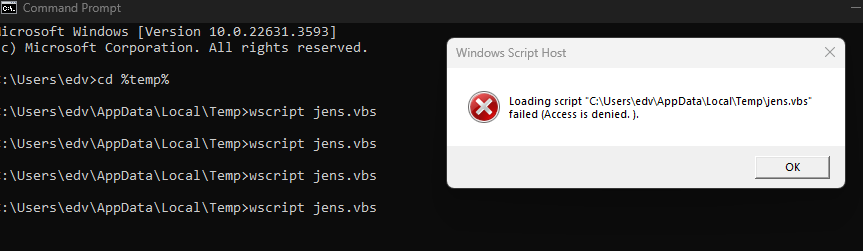
Open Notespad.exe (Leave content empty)
Save As to “c:\users\username\appdata\local\temp\test.vbs”
Wscript.exe c:\users\username\appdata\local\temp\test.vbs
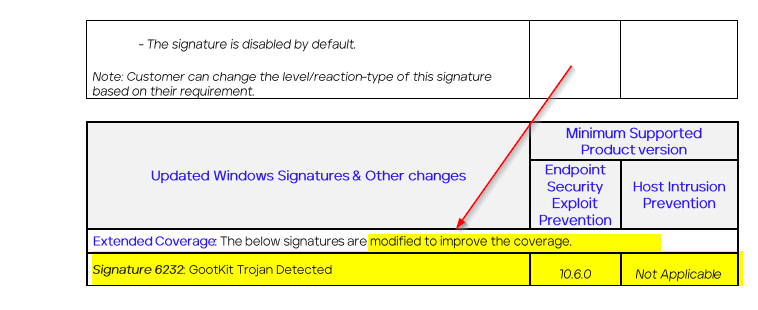
You get a false/postive detection on Gootkit from ENS 10.7 with the IPS/Signature Expoit rule 6232 GOOTkit Trojan Detected which was updated on 15.05.2024 MAY
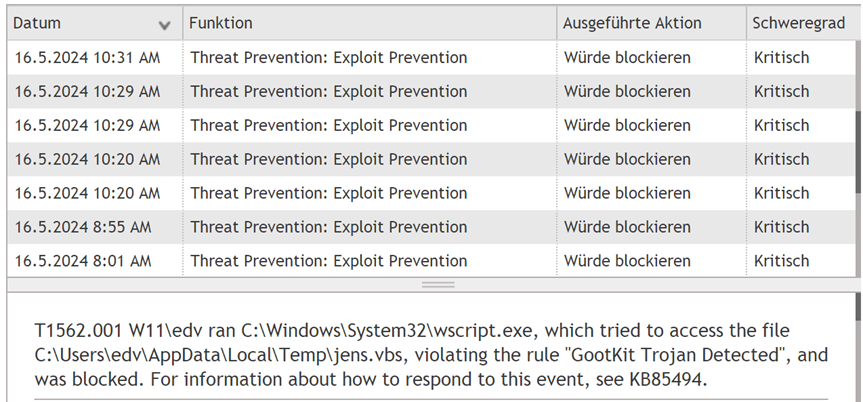
T1562.001 W11\edv ran C:\Windows\System32\wscript.exe, which tried to access the file C:\Users\edv\AppData\Local\Temp\jens.vbs, violating the rule “GootKit Trojan Detected”, and was blocked.
For information about how to respond to this event, see KB85494.
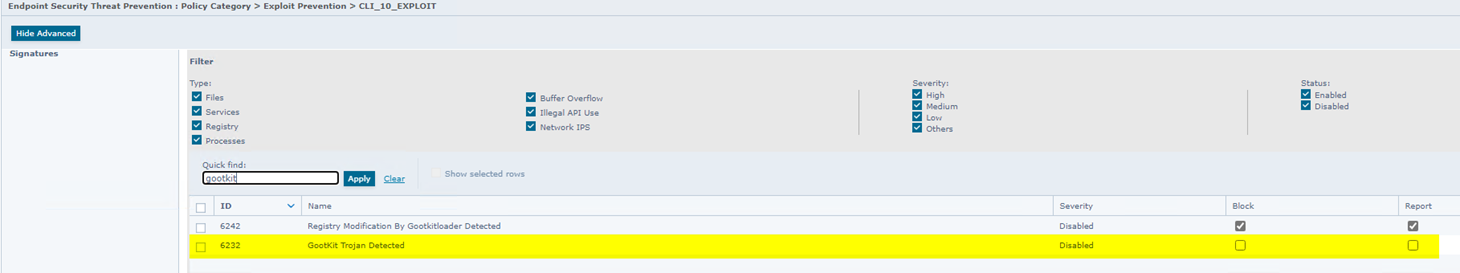
EPO view EXPLOIT search for 6232, turn BLOCK OFF
This comes with good (change) or bad (false) timing after we have seen some Gootloader activity happening in EU/CH these days.
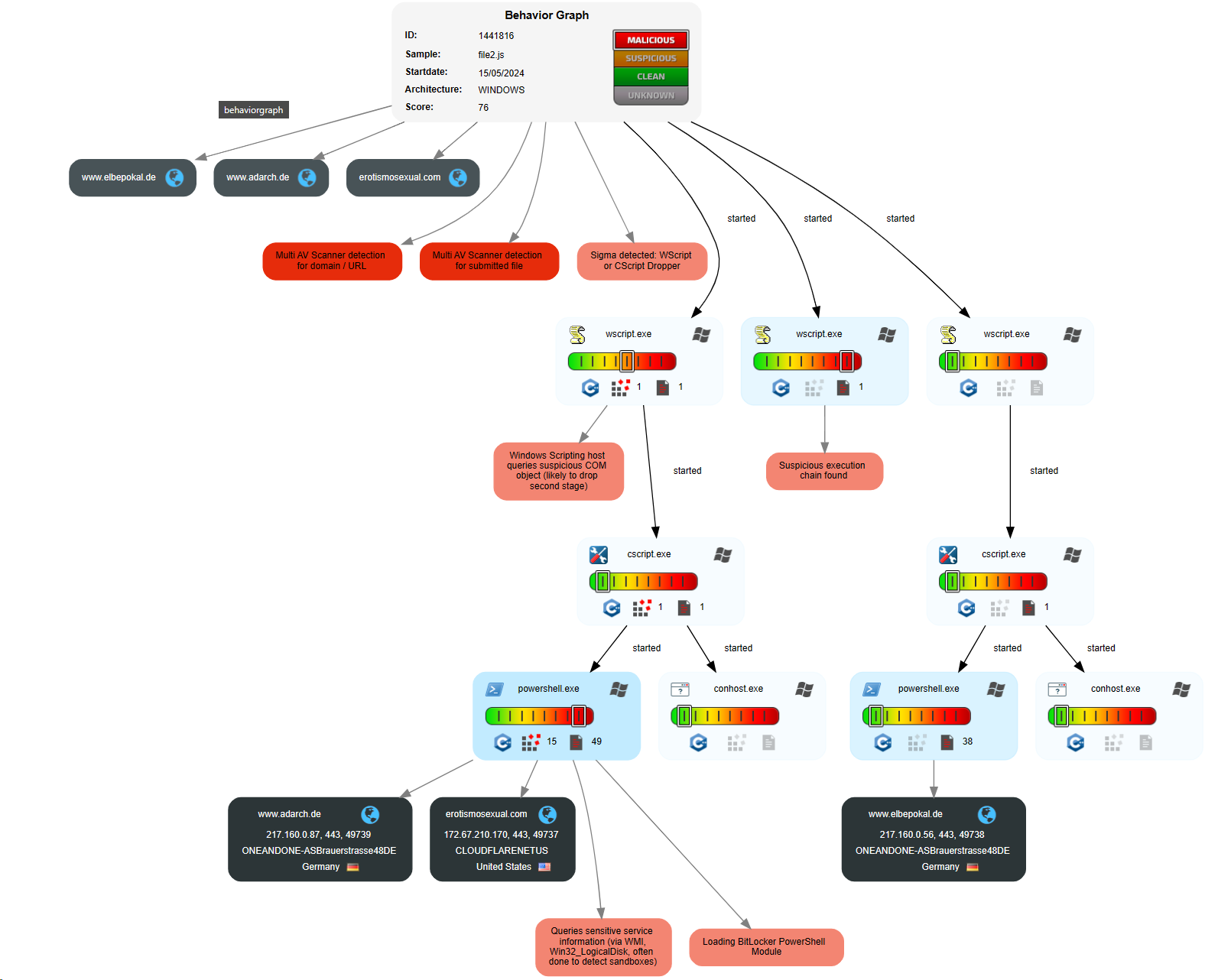
Just one of them on 15.05.2024


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.