Mcafee EPO prevent exe RUNNING FROM %appdata% folders with an Access protection Policy
How to protect from most 0day Flash Exploits and malware like Ransom Cryptowall in summer 2015. You simply can’t keep up with patching even with deployment or
Management solutions in place. Now you should have an IPS Filter like Fortigate with Fortiguard. Fortigate is most of the times involved in detection of Flash Exploits so a good choice in that direction.
But the problems are SSL/HTTPS Virus of you can’t break the stream because of legal concerns.
Here is a solution to strip it down by Mcafee but as always not clear in their documentation.
Sure this covers 80% but it will take out some heat. Another tip would be to use Microsoft EMET from ou side. There is also a GPO to prevent such things but this will take more time to setup.
Mcafee EPO Server Logon
Go to Clients
Assigned Policy
Access Protection Policy
Choose your “Policy” > “My Default”
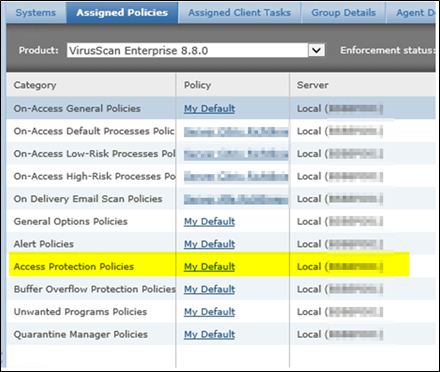
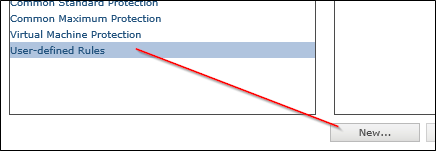
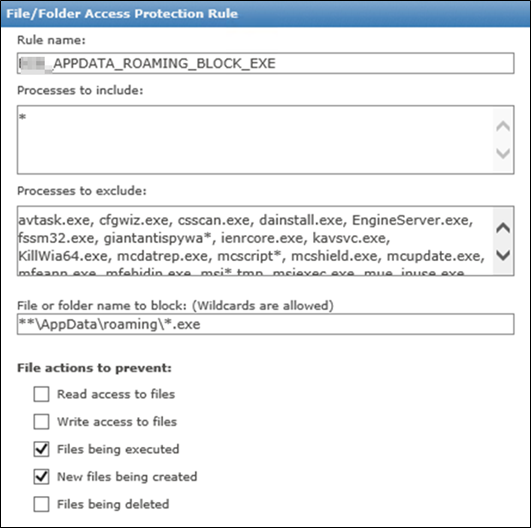
Now the trick was the PATH. I am not sure but ONE Mcafee KB was wrong or not sol effective here.
We are still unsure if it has to be \ or / if you read their docu.
Well here is how it worked for us. We don’t want to catch %appdata%\temp because there is already an
Options in mcafee itself for that and it was not a good idea with some customers and special apps.
| 01_APPDATA_ROAMING_BLOCK_EXE |
| avtask.exe, cfgwiz.exe, csscan.exe, dainstall.exe, EngineServer.exe, fssm32.exe, giantantispywa*, ienrcore.exe, kavsvc.exe, KillWia64.exe, mcdatrep.exe, mcscript*, mcshield.exe, mcupdate.exe, mfeann.exe, mfehidin.exe, msi*.tmp, msiexec.exe, mue_inuse.exe, navw32.exe, ncdaemon.exe, nmain.exe, Patch.log, regsvc.exe, rtvscan.exe, sdat*.exe, svchost.exe, TrolleyExpress.exe, VirusScanAdvancedServer.exe, vmscan.exe, VSE88HF793781.exe, \:::mcadmin.exe, \:::mcconsol.exe, \:::mcupdate.exe, \:::restartVSE.exe, \:::scan32.exe, \:::scncfg32.exe, \:::shcfg32.exe, \:::shstat.exe, \:::VSCore\dainstall.exe, \:::VSCore\x64\dainstall.exe, \:::vstskmgr.exe, \:::x64\scan64.exe |
| C:\users\**\appdata\local\**\*.exe |
| 02_APPDATA_LOCALOW_BLOCK_EXE |
| avtask.exe, cfgwiz.exe, csscan.exe, dainstall.exe, EngineServer.exe, fssm32.exe, giantantispywa*, ienrcore.exe, kavsvc.exe, KillWia64.exe, mcdatrep.exe, mcscript*, mcshield.exe, mcupdate.exe, mfeann.exe, mfehidin.exe, msi*.tmp, msiexec.exe, mue_inuse.exe, navw32.exe, ncdaemon.exe, nmain.exe, Patch.log, regsvc.exe, rtvscan.exe, sdat*.exe, svchost.exe, TrolleyExpress.exe, VirusScanAdvancedServer.exe, vmscan.exe, VSE88HF793781.exe, \:::mcadmin.exe, \:::mcconsol.exe, \:::mcupdate.exe, \:::restartVSE.exe, \:::scan32.exe, \:::scncfg32.exe, \:::shcfg32.exe, \:::shstat.exe, \:::VSCore\dainstall.exe, \:::VSCore\x64\dainstall.exe, \:::vstskmgr.exe, \:::x64\scan64.exe |
| C:\users\**\appdata\local\**\*.exe |
Some sample search patterns:
Find unwanted Google chrome.exe under %appdata%\local everwyhere
C:\users\**\appdata\local\**\chrome.exe
C:\users\**\appdata\local\**\gears-chrome-opt.msi
Check left corner FOR “Workstation” and for “Server”
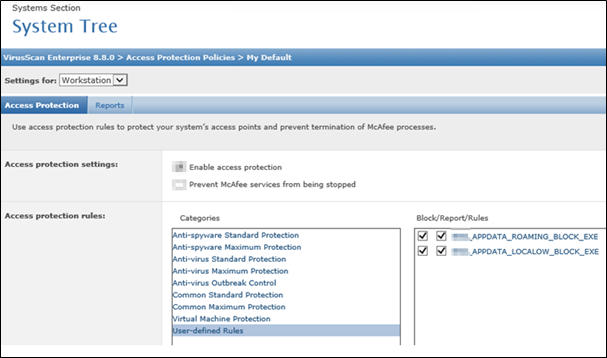
Client side TEST
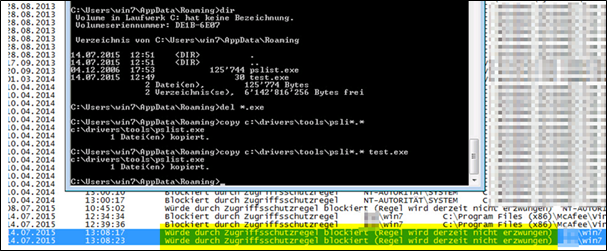
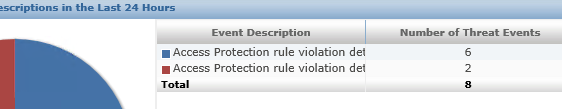
EPO side view
Original Link from Mcafee:
Wildcard patterns mcafee:
https://kc.mcafee.com/corporate/index?page=content&id=KB54812
Adobe:
https://helpx.adobe.com/security/products/flash-player/apsa15-04.html


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.