Mcafee posted a fixed version of the 10.7 June 2022 release.
Hidden in the release notes you will find an important detail.
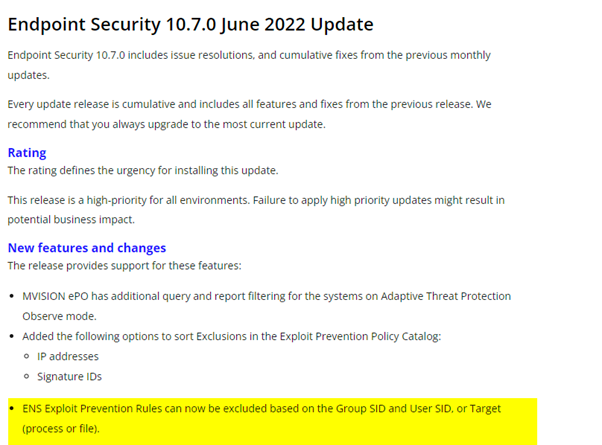
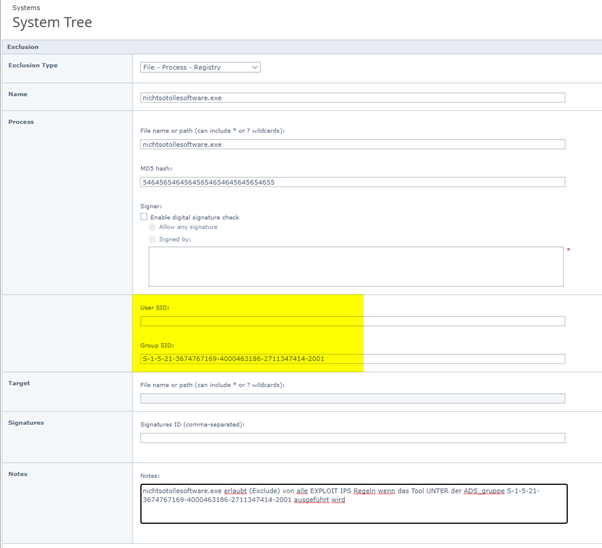
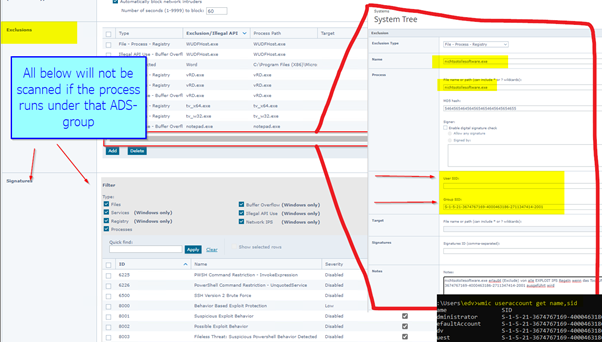
You can now EXCLUDE Signature/Exploit/IPS rules FOR certain Active Directory users or group by SID.
This is like a WMI filter for GPO Group Policy to drill down more granular and to target Exclusion more effective.
A main problem until now is the exclusion with MD5 checksum would be the safest and useful. However if you
Have self updating software (Like a RAPID 7 Agent) you have changing MD5 Checksum.
That’s no problem if you have an enterprise and Mcafee TIE-Server and ATD Sandbox which automatic sess
That there are older version of the Agent in history and checks several other things and then approves the file for running or not.
For Exclusion this will help to limit an Exclusion for a certain file (With the MD5) to limit the exclusion to a certain user group or single user.
If “financetoolstupidcoder.exe” does hit 20 Exploit rules because it was so crappy coded then you can exclude all the Signature based rules
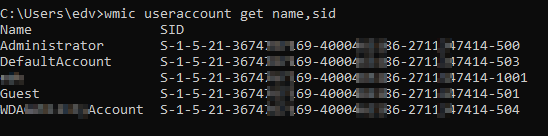
For the single user with the SID 5654654634338998888 (Your CFO who gives IT money). 😉
We would like to point out that Mcafee has the large solution with ATD (TIE-Server, ATD-Sandbox) which allows you to control
EXE with MD5 but in SBS or even a 1000+ shop you sometimes simply can’t handle a strict change and release management.
This will help us all a lot.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.