M.A.S.U
(M)CAFEE (A)TD (S)ANDBOX (U)PLOADER
V4.1, Mike Butsch, Senior System Engineer, www.butsch.ch
Remark 2024: Everything will work for TIS / Trellix Intelligent Sandbox we have been using the same tool with every release of TIS. Hopefully there is a ready solution for FireEye without using Python
The tool is freeware, feel free to use it. If you like it and if you use it, please mention us in a blog or in a comment on McAfee/Trellix Forum (If it once will exist again after NOV 2023?). Maybe connect with us on LinkedIn? Or visit our blog www.butsch.ch.
MASU is a tool we wrote to bulk upload Binary Files (EXE/DLL/COM) to the ATD Sandbox from McAfee/Trellix. The main purpose and usage are the pre-feeding of new files in an enterprise environment to the sandbox so they are already known to ATP/TIE before the binary drops into production.
A big fallback for us is that the ATD is only able to handle files, which are up to 15MB in total. This may be a good idea for Malware in general (Who says it has to be that small?), but in terms of the pre-validation of files to the McAfee/Trellix system, it is a weak point. If you run the ATD Sandbox beside TIE Server and want to use it to fully automatically test new files, this is a downside, which does not work out of the box.
The procedure’s target is ONLY to feed the ATD Sandbox with bulk files. You could get feedback and results via FTP to a local FTP Server (From the ATD Sandbox). However, if you go more into that, I recommend using the ATD API.
We just want to BULK Submit files from A Directory to the ATD. That is the main goal.
Short if you have no time and love RTFM
masu.exe c:\myfoldertoscanrecursive ALL 178.44.55.254 atduserforftp atdftppass
With masu.exe you can:
- Recursive scan a Directory for a mentioned file extension (EXE/DLL/COM)
- Exclude Directory or File pattern you don’t want to scan and upload
- In a separate pre-run Extract ZIP Files to a Sub Directory (ZIP_UNPACK)
- In a separate pre-run Extract MSI with a tried Admin to a Sub Directory (MSI_UNPACK)
- Upload the found relevant files which are under a size value to the ATD with FTP
Download:
|
Date |
Version |
Built for min. Microsoft .NET Framework |
Link |
Checksumm SHA-256 |
|
05.04.2024 |
4.1.0.0 |
4.0 |
https://www.butsch.ch/wp-content/uploads/tools/Masu/4.1.0.0/MASU.7z |
60d76d7811ad0a8a0bf519a4feedfccb09407e0fc132f7f06b98c7094c7c944e |
Security AV check done for file crlcheck.exe
|
23.03.2024 |
Check |
1 of 72 this may be related to. One is a chinese supplier (BKFAVpro) for enduser protection. |
|
MD5 |
83fce96af5df91a3d126f5b59730980b |
|
|
SHA-1 |
a1e60aa917ae3d0d2a73fb9f802e7a1ea5117e6a |
|
|
SHA-256 |
60d76d7811ad0a8a0bf519a4feedfccb09407e0fc132f7f06b98c7094c7c944e |
|
|
23.03.2024 |
AV |
Checked with Enterprise AV-solution Mcafee/Trellix ENS 10.7.0.6177 05.04.2024 |
The main goal was to have a hot scan folder at large customers where internal IT can place files, and a batch calls our atupload.exe every few hours, which then uploads all files to the ATD.
The solution has been working well for almost a year now at some healthcare customers. We have also integrated the automatic unpacking of MSI and ZIP files (normally, this is done by the person who drops files into the folder with different methods).
|
atupload.exe |
Our MASU tool written in c# which scans a Directory and upload file to ATD This needs Microsoft Framework to run |
|
settings.config |
Configuration file with Exclusions, File size, 7ZIP filename |
|
7z*.* |
This is the path to the 7ZIP Commandline tool and dll’s to extract ZIP Files. This is Opensource and you can download from http://www.7-zip.de/download.html |
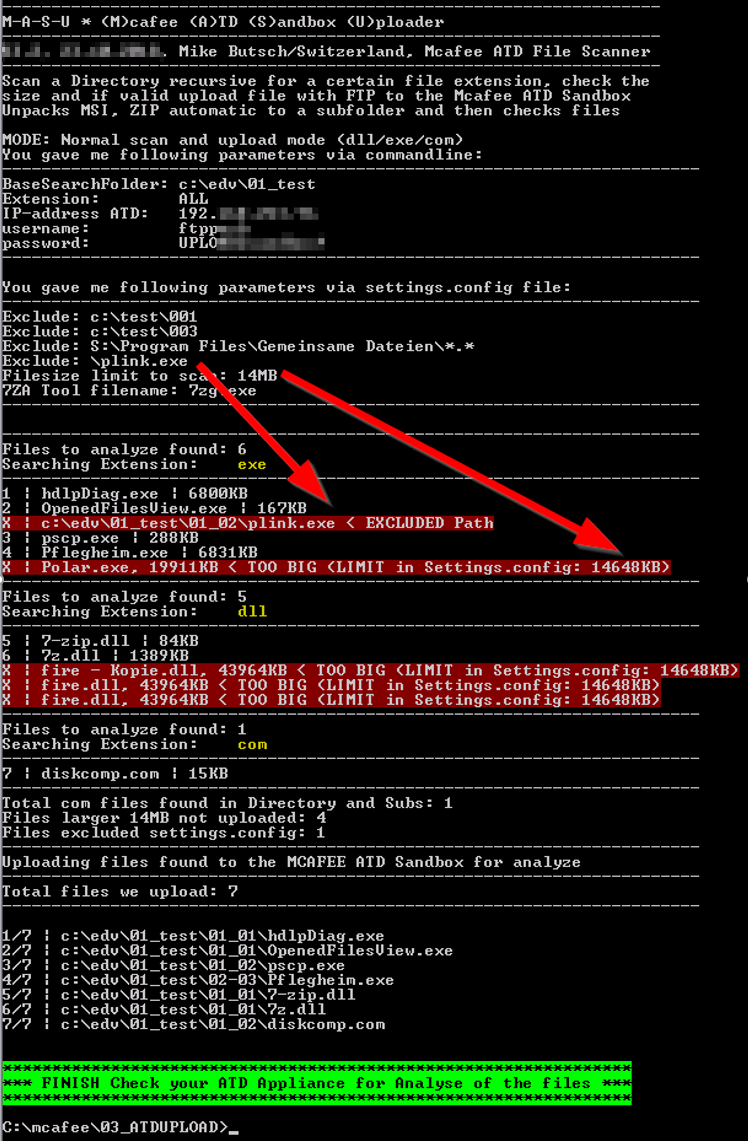
There is help if you just start masu.exe without anything
FILE: Settings.config
|
FILE: settings.config |
|
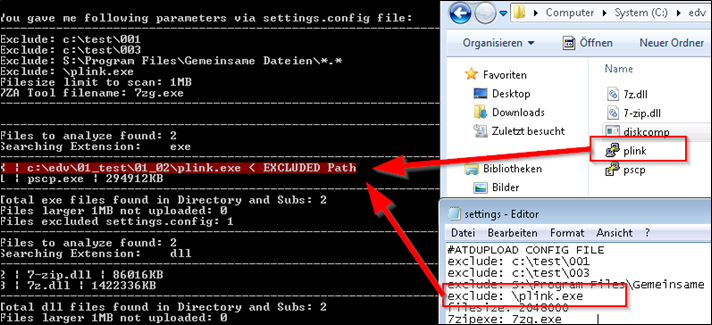
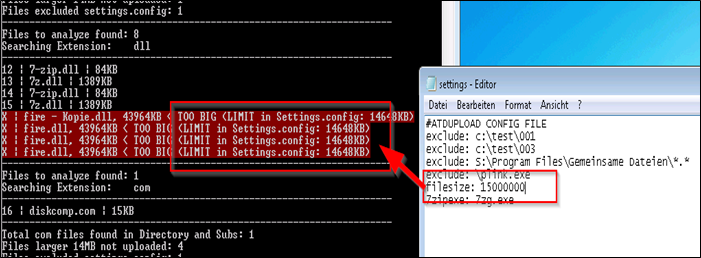
# MASU.EXE CONFIG FILE settings.config for MASU.exe # Syntax you can use in the config file: exclude, filesize # All other paramters are overgiven via commandline to the EXE direct # ———————————————————————————— # Parameter exclude # What it does: To exclude a Full directory or all folder recursive # ———————————————————————————— # exclude: c:\test\001 # exclude: \001\mysubdirectory\ exclude: c:\test\003 exclude: \plink.exe exclude: mytextfreetogofromfileirfolder filesize: 15000000 7zipexe: 7zg.exe |
Starting with each “exclude:” line, you can exclude directory or file patterns you don’t want to scan and upload to the Sandbox. Just add a new line per exclusion, following the sample format.
FILE: settings.config
LINE: exclude: \mypath\
LINE: exclude: justawordyouthinkofflikeconfifential
This is the path to the 7-Zip Command-line tool to extract ZIP files. This is open-source, and you can download the tool free from http://www.7-zip.de/download.html and place it into the directory where you have atupload.exe and settings.config. The filename of the 7-Zip executable may vary with each release, so you can mention the correct name.
FILE: settings.config
LINE: 7zipexe: 7zg.exe
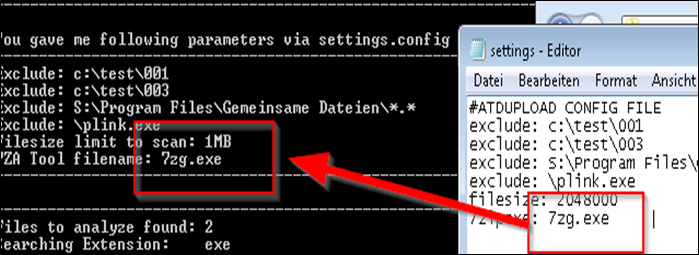
Since the ATD only validates files not larger than 15MB, we have an option where you can specify the maximum size of the files that atupload.exe will upload to the ATD. Please mention the size in kilobytes (KB).
FILE: settings.config
LINE: filesize: 15000000
Means DO not SCAN any files larger than 15MB
Setup solution Batch to run all together fully automatic on a scanner client:
Just is just an idea do that however you want OR do it manual each time when you have new files to submit to the ATD.
- Make a new USER on the ATD Sandbox web interface. Enable FTP. (See Mcafee manual)
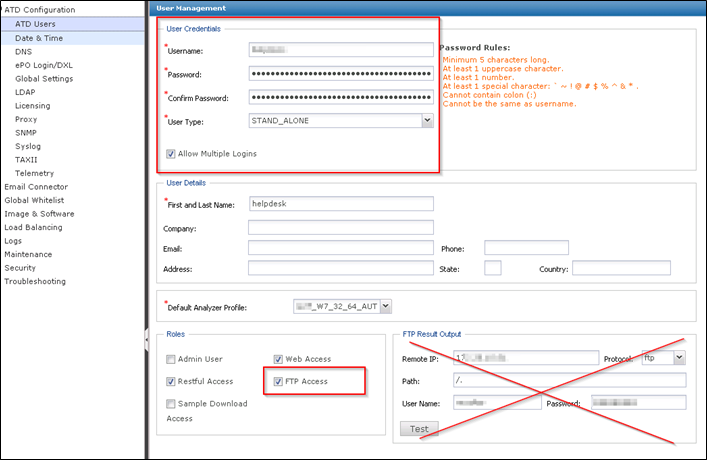
- Test with ftp.exe if all works and you have FTP open from your client to the ATD which for sure is in special VLAN with special Firewall Perimeter rules!
On the Scanner client (Just a Windows Box or Server)
- Make Directory called “c:\mcafee\01_SCAN”
- Share that folder for the people who want to drop files, zips, msi to scan (Sample scan$)
- Make Directory called “c:\mcafee\03_masu”
- Put masu.exe, settings.config and all 7ZIP Commandline binary into the folder “c:\mcafee\03_masu”
- Write a batch like “masu.cmd” with following content. Run that batch hourly with Schedule Task.
He will use 7Z commandline tool to try to extract Packed files like .ZIP or .RAR if found any
The password and username YOU see in the batch is WRITING ONLY to the FTP account.
c:
cd\
cd “C:\mcafee\03_masu
:: —————————————————————————-
:: ONLY SCAN AND UNZIP files if any
:: —————————————————————————-
masu.exe C:\mcafee\01_SCAN zip
ping 127.0.0.1 -n 30
del C:\mcafee\01_SCAN\*.zip /q /f
ping 127.0.0.1 -n 30
:: —————————————————————————-
:: ONLY SCAN AND UNPACK MSI-Files if any
:: —————————————————————————-
masu.exe C:\mcafee\01_SCAN msi
ping 127.0.0.1 -n 30
del C:\mcafee\01_SCAN\*.msi /Q /f
:: —————————————————————————-
:: SCAN regular way (All extracted) and upload to ATD via FTP
:: —————————————————————————-
masu.exe C:\mcafee\01_SCAN ALL 192.168.233.16 helo mypassword
:: —————————————————————————-
:: Loeschen aller Files nach scan
c:\mcafee\removefolder.cmd “C:\mcafee\01_SCAN”
if not Exist “C:\mcafee\01_SCAN” md “C:\mcafee\01_SCAN”
Here is the help file of masu.exe
|
MASU HELP |
|
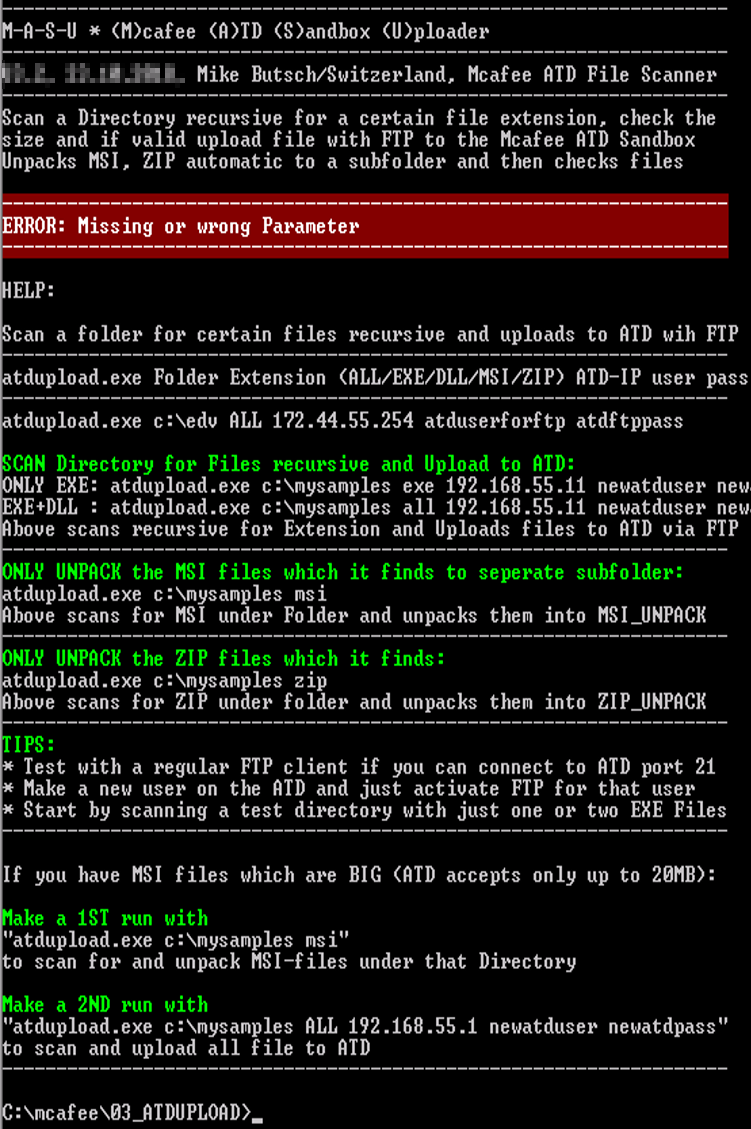
——————————————————————- M-A-S-U * (M)cafee (A)TD (S)andbox (U)ploader ——————————————————————- V3.2, Mike Butsch/Switzerland, Mcafee ATD File Scanner ——————————————————————- Scan a Directory recursive for a certain file extension, check the size and if valid upload file with FTP to the Mcafee ATD Sandbox Unpacks MSI, ZIP automatic to a subfolder and then checks files ——————————————————————- ERROR: Missing or wrong Parameter ——————————————————————- HELP:
Scan a folder for certain files recursive and uploads to ATD wih FTP ——————————————————————- atdupload.exe Folder Extension (ALL/EXE/DLL/MSI/ZIP) ATD-IP user pass ——————————————————————- atdupload.exe c:\edv ALL 178.44.55.254 atduserforftp atdftppass
SCAN Directory for Files recursive and Upload to ATD: ONLY EXE: atdupload.exe c:\mysamples exe 192.168.55.11 newatduser pass EXE+DLL : atdupload.exe c:\mysamples all 192.168.55.11 newatduser pass Above scans recursive for Extension and Uploads files to ATD via FTP ——————————————————————- ONLY UNPACK the MSI files which it finds to seperate subfolder: atdupload.exe c:\mysamples msi Above scans for MSI under Folder and unpacks them into MSI_UNPACK ——————————————————————- ONLY UNPACK the ZIP files which it finds: atdupload.exe c:\mysamples zip Above scans for ZIP under folder and unpacks them into ZIP_UNPACK ——————————————————————- TIPS: * Test with a regular FTP client if you can connect to ATD port 21 * Make a new user on the ATD and just activate FTP for that user * Start by scanning a test directory with just one or two EXE Files ——————————————————————- If you have MSI files which are BIG (ATD accepts only up to 20MB):
Make a 1ST run with “atdupload.exe c:\mysamples msi” to scan for and unpack MSI-files under that Directory
Make a 2ND run with “atdupload.exe c:\mysamples ALL 192.168.55.1 newatduser pass” to scan and upload all file to ATD ——————————————————————- |
|
FILE: settings.config |
|
# MASU.EXE CONFIG FILE settings.config for MASU.exe # Syntax you can use in the config file: exclude, filesize # All other paramters are overgiven via commandline to the EXE direct # ———————————————————————————— # Parameter exclude # What it does: To exclude a Full directory or all folder recursive # ———————————————————————————— # exclude: c:\test\001 # exclude: \001\mysubdirectory\ exclude: c:\test\003 exclude: \plink.exe exclude: mytextfreetogofromfileirfolder filesize: 15000000 7zipexe: 7zg.exe |
FAQ
There are some files we can’t delete in the 01_SCAN folder?
This is a LOCK from the 7ZIP tool. Use OpenedFilesView – View opened/locked files in your system (sharing violation issues) (nirsoft.net)
https://www.nirsoft.net/utils/opened_files_view.html to find the FILE LOCKS and close them.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.