Mcafee EPO Server 5.3.3 seems to have problems on some older OS like 2008R2 regarding TLS ciphers (We did not see this in 2012R2 to date with our customers). The A-Z sort order of those is the source. This had such an impact that Mcafee did release this info to all customer with SNS-Alert.
This has been a month where we on our side have seen why PKI Engineer has to be Senior and understand all Levels of the full enterprise (Appliance, Software, Hardware etc.) The times where you could slip through that gray zone without really understanding what it does 100% are over. When it comes to Exchange or Sharepoint SAN Certificates to CRL Certificate Revocation list you have to understand what it does.
https://kc.mcafee.com/corporate/index?page=content&id=KB89858
This issue can manifest in many ways including, but not limited to:
- McAfee Agent Wake Ups and Run Client Task Nows succeeding on the endpoint, but never reporting back status.
- Drive Encryption activation failures.
The ePO server_servername.log (located in ePO_install_dir\db\log) will include messaging that demonstrates its inability to communicate to the Application Server service, similar to the following:
20170918133528 E #05472 MCUPLOAD SecureHttp.cpp(987): Failed to send HTTP request. Error=12029 (12029)
20170918133528 E #05472 NAIMSERV server.cpp(583): Failed to send request, err=0x80004005, HTTP status code=0
20170918133528 E #05472 NAIMSERV server.cpp(968): Error sending data channel message to application server
System Change
Upgraded ePO to 5.3.3.
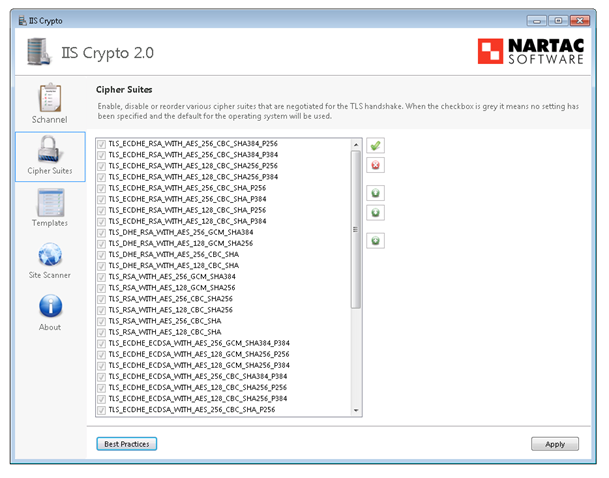
Reorder the ciphers to have the following at the top:
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_RSA_WITH_AES_256_GCM_SHA384
- TLS_RSA_WITH_AES_128_GCM_SHA256
This is an interesting tool which we used before at ISP’s.
www.nartac.com/Products/IISCrypto



 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.