Mastering Firewalls for Intunes and Autopilot Success
In the realm of IT, especially with the advent of cloud-based systems like M365 and Intune, managing firewalls has evolved into a complex challenge. Gone are the days of a handful of external ports; now, it’s like navigating a digital maze of ports and IP ranges. Enter the Firewall Team, tasked with untangling these complexities to ensure a seamless 100% functionality for Intune and other critical processes.
And let’s not forget the Firewall’s critical role in Intune deployments. As Intune downloads its packages via HTTP/Port 80, it’s essential that the Firewall handles the Port 80 stream according to Microsoft’s specifications, be it Palo Alto, Fortigate, or other contenders. This unassuming box holds the power to determine whether Intune and Autopilot will operate at 10% or achieve a flawless 100%, and sometimes, it’s a game-changer.
Do NOT Break SSL, do not watch into SSL
That one should be really clear and no don’t try it. It will look like it works than a few minutes later, or next client or package it want.

Allow HTTP Protocoll “Partial Repsonse” or “Partial Downloads”
RFC for HTTP requests (Section 14.35.2): https://www.w3.org/Protocols/rfc2616/rfc2616-sec14.html#sec14.35.
This is security related. If the attacker can download small parts of an large file (Code) in small parts and then merge them together. As we understood as example
The IPS Filter or Realtime file Sandbox (Whatever FW producers use as terms) can’t analyse the file or try to analyse. That sound strange but because he download 3 separate parts 1xGIF, 1xJPG, 1xHTML and merge that together somehow.
The HTTP range option is like a secret handshake tucked away in the HTTP header. It’s the way client machines subtly ask servers for only specific chunks of a file. Picture it as a covert dance, where the client gracefully seeks out particular bytes from the server. This nifty protocol proves its worth when you’re resuming a download that took a pause or when you’re snatching parts of an executable file from a website.
Imagine you’re downloading an exe file, excited to unleash its power. The client doesn’t demand the whole file; instead, it politely whispers to the server, “Just a snippet, please.” This is the moment where the HTTP range option steps into the spotlight.
But here’s the intriguing part: sometimes, the client doesn’t devour the entire file immediately. It stores a portion away for safekeeping, like a squirrel stashing acorns for later. When it craves the rest, it sends an HTTP Accept-Ranges header, a subtle signal to the server that it’s ready for the next chapter.
We tried to explain this to ourself (Like RESUME in FTP)
The “Accept-Ranges” field in a server’s response is like a little flag telling the client whether it’s cool to make partial requests for a specific resource. Imagine you’re downloading a file, and this field says, “Hey, I’m okay with you asking for just a piece of this file if you want.”
For example, if a server is all about byte-range requests (where you request specific chunks of a file), it will include:
Accept-Ranges: bytes
This is like a green light for the client to use byte range requests for that specific resource. It’s like saying, “Feel free to download this file in parts if you need to. Bytes are the units we’re talking about here.” The technical term for these units is defined in Section 14.1 of the RFC.
Now, here’s the twist: a client can decide to make range requests even if it didn’t get this “Accept-Ranges” field. It’s not a strict rule; it’s more like a suggestion to help things run smoother and save on unnecessary data transfers.
But—and there’s always a but—the client should never assume that just because it got an “Accept-Ranges” field, future range requests will always get partial responses. The content might change, the server might only allow range requests at certain times, or maybe a different middleman will handle the next request.
If a server is not into any kind of range requests for a specific resource, it might shoot back:
Accept-Ranges: none
This is like saying, “Don’t bother asking for parts of this file. I’m not into that range request thing for this particular resource.” The term “none” is reserved just for this purpose.
Now, the tech wizards say this “Accept-Ranges” info can be sent in a trailer section, but it’s better to send it as a header field. Why? Because it’s super helpful when you’re trying to restart a big download that got interrupted. It gives the client a heads up on whether it’s worth trying to download in parts or not before it reaches the trailer section of the response.
We have found info regarding this issue for Palo Alto FW:
Firewall breaks SCCM communication for agent push/download between client and server
Check the box for: Device >> Setup >> Content-ID >> Content -ID Settings >> Allow HTTP Partial response
When it is valid for an SCCM Agent it also valid for a M365 Intunes Deployment standalone.
Microsoft side CRL, FQDN andd IP list you need Intunes and Microsoft Store (Company Portal) working
You want something working the FW-Teams wan’s a KB or a list with targets you must reach and how they can handle the stream (Break SSL, etc.)
Most firewall producers have Databases you can use as target objects like Fortigate. There are over 4’000 FQDN in that Service database. However sometimes Fortinet is not fast enough to update those or there are simply error in the data. Also keep in mind for any Round Robin DNS that cache may play a role.
Microsoft offers a Source list which will give you all FQDN and IP you need to open. The FQDN is depending on your Firewalls Round Robin mechanism and HOW fast this will update or cache. Behind a an FQDN there could be several IP address and depending on your FW or client system this may be outdated sometimes (Load Balancers).
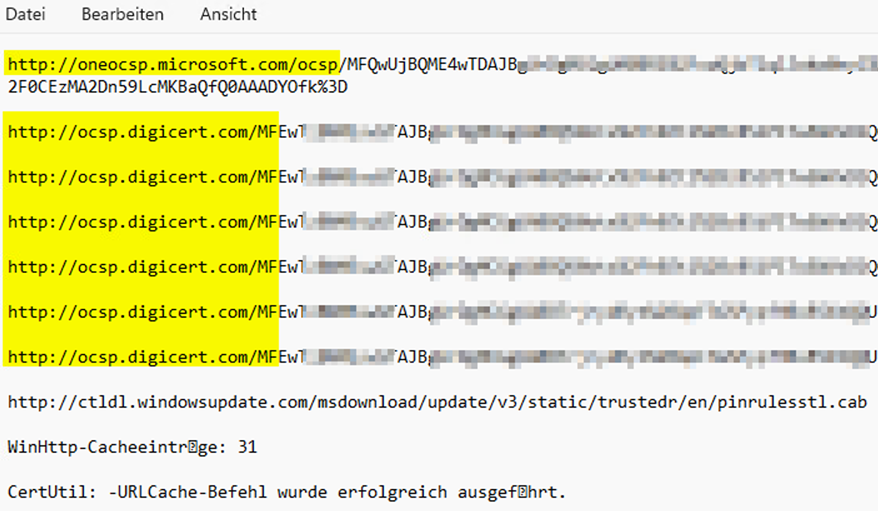
Here is how to get the most important FQDN/IP’s from an INTUNES client which is already connected to MDM/Intunes and did run a deployment. (For the Parts with certutil). The certutil part will show you what CRL Cert Revocation Lists are used by Code Signing (EXE/DLL) on your machine. You MUST 100% have those URL open and working.
| Get all FQDN that Intunes needs in a textfile with PowerShell |
| (invoke-restmethod -Uri (“https://endpoints.office.com/endpoints/WorldWide?ServiceAreas=MEM`&`clientrequestid=” + ([GUID]::NewGuid()).Guid)) | ?{$_.ServiceArea -eq “MEM” -and $_.ips} | select -unique -ExpandProperty ips > Intunes_FQDN.txt |
 |
| Get all IP that Intunes needs in a textfile with Powershell |
| (invoke-restmethod -Uri (“https://endpoints.office.com/endpoints/WorldWide?ServiceAreas=MEM`&`clientrequestid=” + ([GUID]::NewGuid()).Guid)) | ?{$_.ServiceArea -eq “MEM” -and $_.urls} | select -unique -ExpandProperty urls > Intunes_IP.txt |
 |
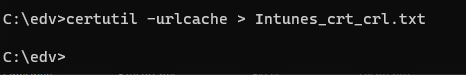
| Get a list off all Certificate related CRL (Certificate Revocation List) that your Intunes clients needs |
| Certuitl –urlcache > Intunes_crt_crl.txt |
 |
 |
| 16.11.2023 FQDN List needed for Intunes, Microsoft Store, Company Portal |
| *.swdd02.manage.microsoft.com
*.channelservices.microsoft.com *.delivery.mp.microsoft.com *.dl.delivery.mp.microsoft.com *.do.dsp.mp.microsoft.com *.emdl.ws.microsoft.com *.go-mpulse.net *.infra.lync.com *.itunes.apple.com *.manage.microsoft.com *.mzstatic.com *.notify.windows.com *.officeconfig.msocdn.com *.phobos.apple.com *.prod.do.dsp.mp.microsoft.com *.resources.lync.com *.s-microsoft.com *.support.services.microsoft.com *.swda01.manage.microsoft.com *.swda01-mscdn.manage.microsoft.com *.swda02.manage.microsoft.com *.swda02-mscdn.manage.microsoft.com *.swdb01.manage.microsoft.com *.swdb01-mscdn.manage.microsoft.com *.swdb02.manage.microsoft.com *.swdb02-mscdn.manage.microsoft.com *.swdc01.manage.microsoft.com *.swdc01-mscdn.manage.microsoft.com *.swdc02.manage.microsoft.com *.swdc02-mscdn.manage.microsoft.com *.swdd01.manage.microsoft.com *.swdd01-mscdn.manage.microsoft.com *.swdd02-mscdn.manage.microsoft.com *.trouter.skype.com *.update.microsoft.com *.vortex.data.microsoft.com *.windowsupdate.com *.wns.windows.com 5-courier.push.apple.com approdimedatahotfix.azureedge.net approdimedatapri.azureedge.net approdimedatasec.azureedge.net ax.itunes.apple.com.edgesuite.net clientconfig.passport.net config.office.com contentauthassetscdn-prod.azureedge.net contentauthassetscdn-prodeur.azureedge.net contentauthrafcontentcdn-prod.azureedge.net contentauthrafcontentcdn-prodeur.azureedge.net devicelistenerprod.eudb.microsoft.com devicelistenerprod.microsoft.com edge.skype.com ekcert.spserv.microsoft.com ekop.intel.com emdl.ws.microsoft.com enterpriseregistration.windows.net euprodimedatahotfix.azureedge.net euprodimedatapri.azureedge.net euprodimedatasec.azureedge.net fd.api.orgmsg.microsoft.com ftpm.amd.com graph.windows.net intunecdnpeasd.azureedge.net intunemaape1.eus.attest.azure.net intunemaape10.weu.attest.azure.net intunemaape11.weu.attest.azure.net intunemaape12.weu.attest.azure.net intunemaape13.jpe.attest.azure.net intunemaape17.jpe.attest.azure.net intunemaape18.jpe.attest.azure.net intunemaape19.jpe.attest.azure.net intunemaape2.eus2.attest.azure.net intunemaape3.cus.attest.azure.net intunemaape4.wus.attest.azure.net intunemaape5.scus.attest.azure.net intunemaape6.ncus.attest.azure.net intunemaape7.neu.attest.azure.net intunemaape8.neu.attest.azure.net intunemaape9.neu.attest.azure.net itunes.apple.com lgmsapeweu.blob.core.windows.net login.microsoftonline.com login.windows.net manage.microsoft.com naprodimedatahotfix.azureedge.net naprodimedatapri.azureedge.net naprodimedatasec.azureedge.net ocsp.apple.com payloadprod*.blob.core.windows.net phobos.apple.com phobos.itunes-apple.com.akadns.net remoteassistanceprodacs.communication.azure.com ris.prod.api.personalization.ideas.microsoft.com swda01-mscdn.azureedge.net swda02-mscdn.azureedge.net swdb01-mscdn.azureedge.net swdb02-mscdn.azureedge.net swdc01-mscdn.azureede.net swdc02-mscdn.azureedge.net swdd01-mscdn.azureedge.net swdd02-mscdn.azureedge.net swdin01-mscdn.azureedge.net swdin02-mscdn.azureedge.net time.windows.com tsfe.trafficshaping.dsp.mp.microsoft.com windowsphone.com www.msftconnecttest.com www.msftncsi.com |
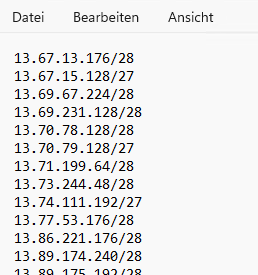
| 16.11.2023 IP List needed for Intunes, Microsoft Store, Company Portal |
| 13.67.13.176/28
13.67.15.128/27 13.69.67.224/28 13.69.231.128/28 13.70.78.128/28 13.70.79.128/27 13.71.199.64/28 13.73.244.48/28 13.74.111.192/27 13.77.53.176/28 13.86.221.176/28 13.89.174.240/28 13.89.175.192/28 20.37.153.0/24 20.37.192.128/25 20.38.81.0/24 20.41.1.0/24 20.42.1.0/24 20.42.130.0/24 20.42.224.128/25 20.43.129.0/24 20.44.19.224/27 20.49.93.160/27 20.189.172.160/27 20.189.229.0/25 20.191.167.0/25 20.192.159.40/29 20.192.174.216/29 20.204.193.10/31 20.204.193.12/30 40.67.121.224/27 40.70.151.32/28 40.71.14.96/28 40.74.25.0/24 40.78.245.240/28 40.78.247.128/27 40.79.197.64/27 40.79.197.96/28 40.80.180.208/28 40.80.180.224/27 40.80.184.128/25 40.82.248.224/28 40.82.249.128/25 40.119.8.128/25 52.150.137.0/25 52.162.111.96/28 52.168.116.128/27 52.182.141.192/27 52.236.189.96/27 52.240.244.160/27 104.46.162.96/27 |
Please see our other related posts:


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.