M365/Intunes | MDM and MAM enrolled difference explained
First, let’s take a look at two different models: MDM and MAM. These models provide options for managing endpoints, including computers, clients, mobiles, and smartphones.
|
|
|
|
|
Mobile Device Management (MDM) Often device corporate owned and paid (Regular employee of SBS or Enterprise)
MDM primarily focuses on managing the entire device. It allows IT administrators to control and secure the entire device, enforcing policies such as device encryption, passcode requirements, and device compliance. In the context of M365 Intune, this means having a comprehensive view and control over the Windows device itself. |
|
Mobile Application Management (MAM) Often BYOD Bring your own device private
MAM, on the other hand, shifts the focus to managing and securing specific applications and their data rather than the entire device. This is particularly beneficial in BYOD scenarios where maintaining a balance between security and user privacy is crucial. |
|
1. Mobile Device Management (MDM) Often device corporate owned and paid (Regular employee of SBS or Enterprise) |
|
MDM primarily focuses on managing the entire device. It allows IT administrators to control and secure the entire device, enforcing policies such as device encryption, passcode requirements, and device compliance. In the context of M365 Intune, this means having a comprehensive view and control over the Windows device itself. |
|
|
|
Pros of MDM:
Cons of MDM:
|
|
2. Mobile Application Management (MAM) (Often BYOD) |
|
MAM, on the other hand, shifts the focus to managing and securing specific applications and their data rather than the entire device. This is particularly beneficial in BYOD scenarios where maintaining a balance between security and user privacy is crucial. |
|
MAM, on the other hand, focuses on securing and managing only the apps and data on a device, rather than the entire device itself. Key aspects of MAM include:
In summary, the primary difference between MDM and MAM for IT professionals is that MDM focuses on managing and securing the entire device, while MAM focuses on managing and securing the apps and data on the device. In practice, many organizations use both MDM and MAM in combination to create a comprehensive mobile device management and security strategy that addresses the unique needs of their workforce. |
|
Pros of MAM:
Cons of MAM:
|
Both?

Control what how?
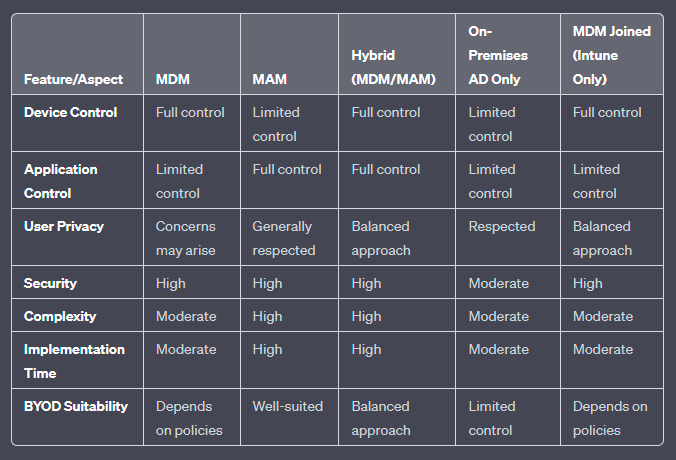
In the MDM Joined (Intune Only) scenario, devices are enrolled and under the management umbrella of Microsoft Intune for Mobile Device Management.
Notably, they do not undergo a conventional on-premises Active Directory join before integrating with Intune. This signifies a departure from traditional methods.
Instead, it involves a streamlined process where devices are directly enrolled in Intune, bypassing the necessity for a local Active Directory join. In this cloud-centric approach, policies and configurations are exclusively orchestrated through Intune, presenting a contemporary and adaptable management solution.
- Device Control: Signifies the extent of influence and governance over the complete device, encompassing policies related to security, access, and configurations.
- Application Control: Encompasses the authority over specific applications and their associated data, allowing administrators to regulate access and permissions at an individual app level.
- User Privacy: Represents the delicate equilibrium between maintaining robust security measures and respecting the privacy of the end user. It addresses concerns related to the collection and use of personal data.
- Security: Evaluates the overall robustness and effectiveness of the security measures implemented within the solution, safeguarding against potential threats and unauthorized access.
- Complexity: Gauges the intricacy involved in setting up and managing the solution. A higher complexity might entail more sophisticated configurations and administration.
- Implementation Time: Refers to the duration needed for the deployment and configuration of the solution, providing insight into the efficiency of the on boarding process.
- BYOD Suitability: Assesses how well a particular option aligns with the principles and requirements of a Bring Your Own Device (BYOD) environment, considering factors such as user-friendliness and the balance between security and user freedom.
Explaining scenarios from the above information will help illustrate and clarify the settings.
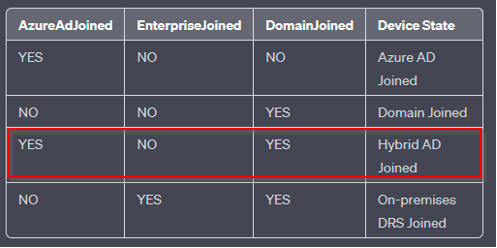
Hybrid AD JOINED sample
|
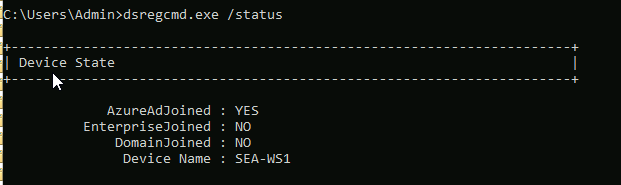
dsregcmd /status Lines Relevant to Manual Join Process: |
dsregcmd /status Lines Relevant to MDM Enrollment: |
|
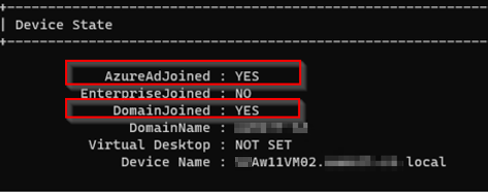
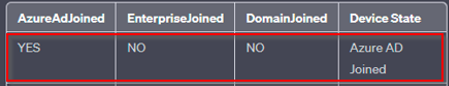
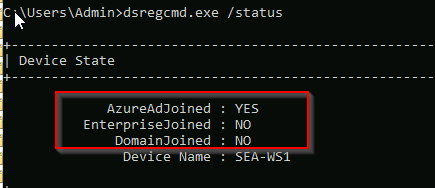
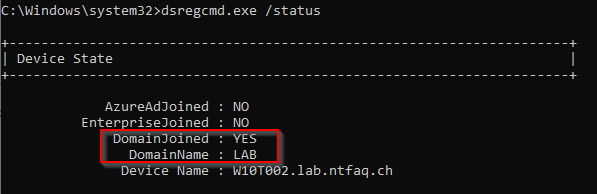
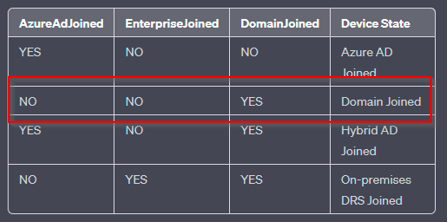
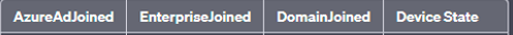
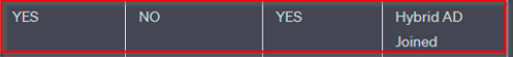
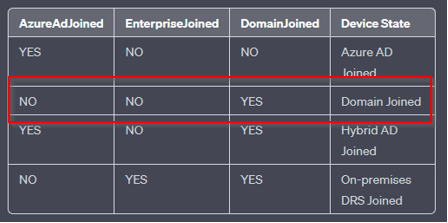
1. AzureAdJoined: This line indicates whether the device is Azure AD joined. If it says “YES,” the device has been manually joined to Azure AD.
2. DomainJoined: This line indicates whether the device is joined to an on-premises Active Directory domain. If it says “YES,” the device is domain-joined.
https://learn.microsoft.com/en-us/azure/active-directory/devices/troubleshoot-device-dsregcmd
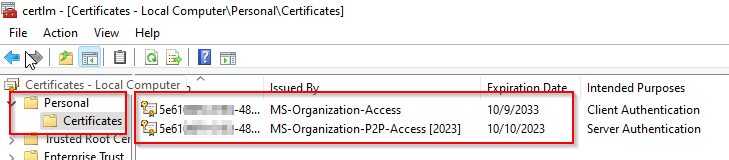
3. DeviceId: The DeviceID uniquely identifies the device within Azure AD. This can be useful for tracking the device’s Azure AD association.
|
1. MdmEnrolled: This line indicates whether the device is enrolled in Mobile Device Management (MDM). If it says “YES,” the device is enrolled in an MDM solution, such as Microsoft Intune.
2. UserEmail: Displays the email address of the user associated with the device. This is relevant as the user’s enrollment status in MDM is tied to the device.
3. ManagementServerAddress: This line provides information about the MDM server’s address. In an Intune-managed environment, this should point to Intune’s service endpoint.
4. EnrollmentServerAddress: Similar to ManagementServerAddress, this line indicates the server address used for enrollment. In an Intune scenario, this would be relevant to the Intune enrollment service.
5. UserToken: This token represents the user’s identity in the MDM system. If the device is MDM enrolled, this token would be associated with the user’s MDM profile. |
|
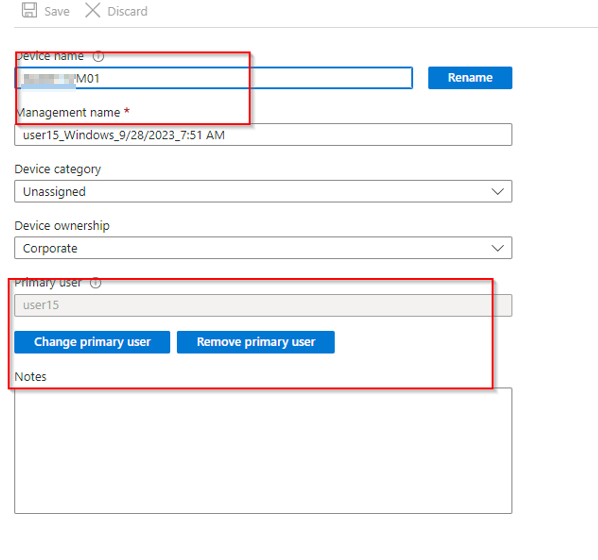
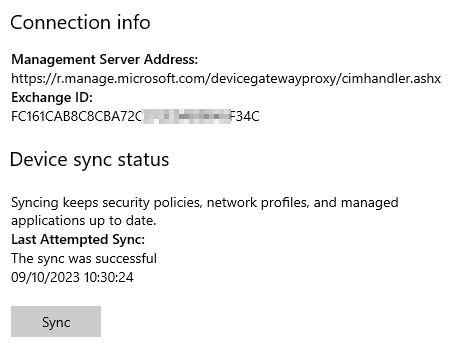
Here you see a HYBRID Joined device and THEN MDM Enrolled > you can change the PRIMARY user in Intunes.
|
|
|
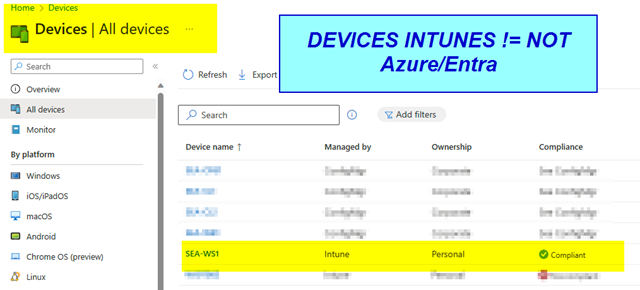
Owenership shows “Corporate”. Devices where ADS (On Premisis Joined) and then via Hybrid Azure synced. After that AUTO Enrolled in MDM via GPO Settings. |
|
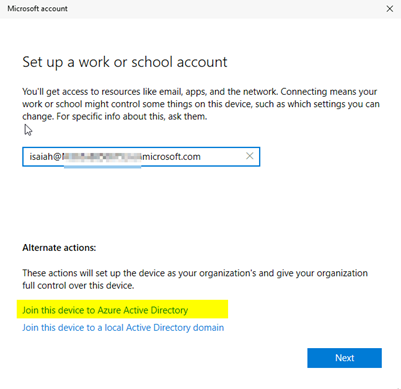
What happens or not with this setting? What affect does it have if you Azure JOIN by hand/user?
Let’s explore what happens, observe the changes in variations when the user account that initiates the joining of Entra/Azure or AND performs MDM enrollment in Intune is restricted by this setting. We aim to limit users from joining whichever they like.
|
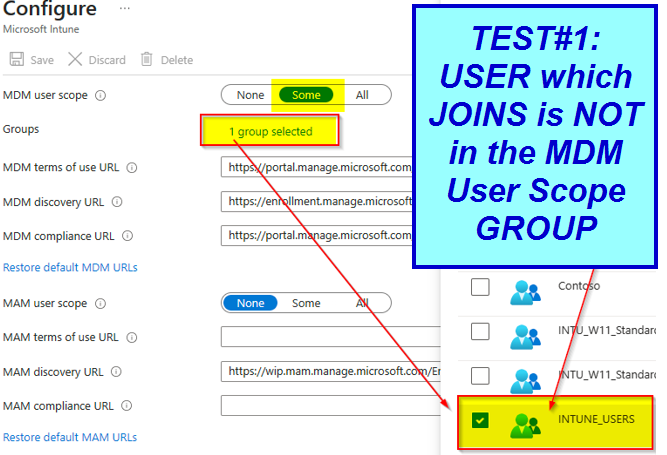
TEST #1 to show what happens if users which does enrollment is not allowded to Enroll into MDM.
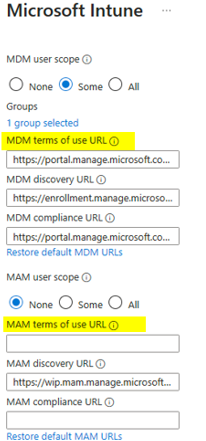
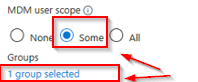
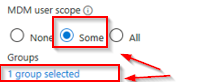
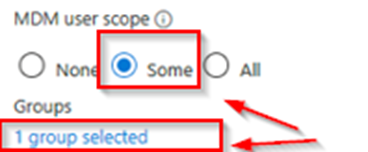
CLIENT: SEA-WS1 DOMAIN ADS on-premises: NO IS workgroup: YES Azure Security Group “Intunes_USERS” member: NO MDM User scope: > SOME > Azure Security Group “Intunes_USERS”
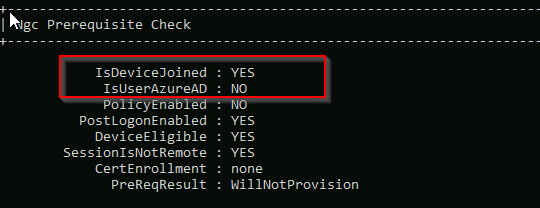
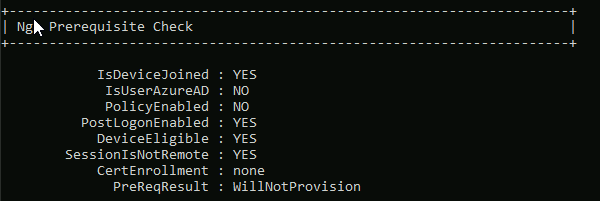
The user initiating the joining process is not a member of the ‘Intunes_USERS’ security group, which is specified in the Microsoft Intune MDM scope (with only one group selected). As a result, the user lacks the necessary rights to enroll a device into Intune MDM management. |
||
|
|
|
|
|
|
|
|
|
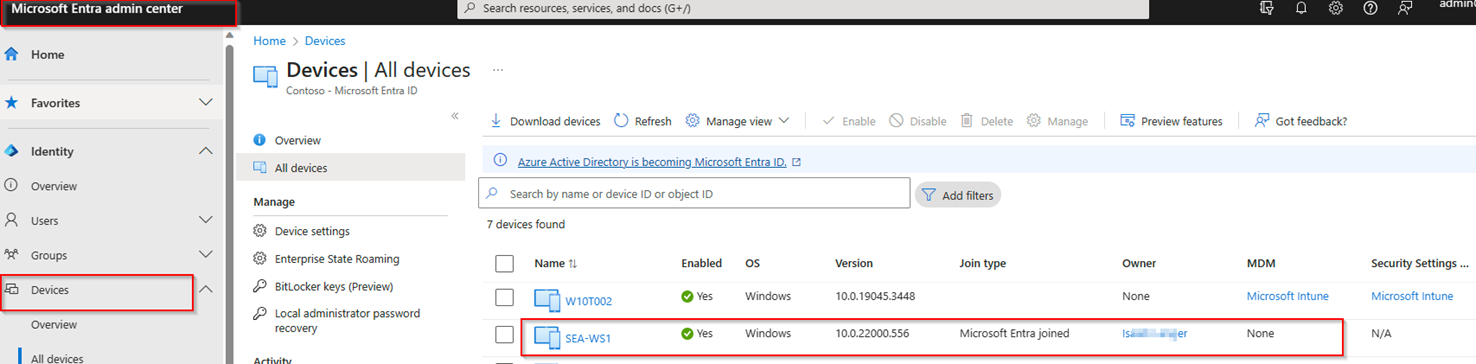
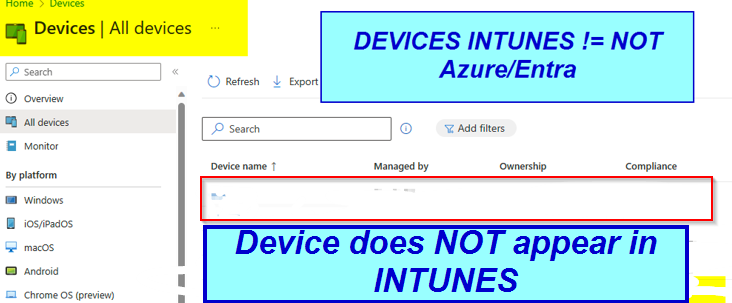
Because the user which joined the DEVICE to AZURE was NOT listed in the Security Group which we have limited on INTUNES MDM / MAM enrollment the client only appears UNDER Entra/Azure. You will not see it under INTUNES Devices. Because the user did NOT have the right to ENROLL the device for INTUNE MDM.
You will not see it under INTUNES Devices. Because the user did NOT have the right to ENROLL the device for INTUNE MDM.
|
||
|
https://learn.microsoft.com/en-us/azure/active-directory/devices/troubleshoot-device-dsregcmd
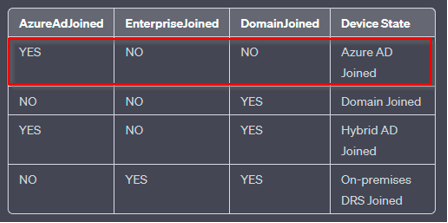
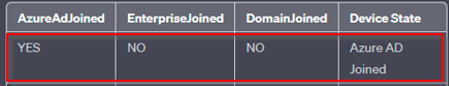
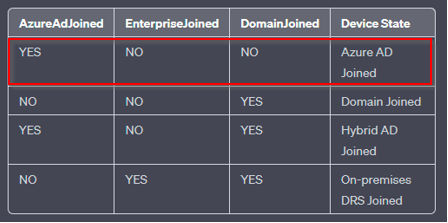
AzureAdJoined: Set the state to YES if the device is joined to Microsoft Entra ID. Otherwise, set the state to NO. EnterpriseJoined: Set the state to YES if the device is joined to an on-premises data replication service (DRS). A device can’t be both EnterpriseJoined and AzureAdJoined. DomainJoined: Set the state to YES if the device is joined to a domain (Active Directory). DomainName: Set the state to the name of the domain if the device is joined to a domain. |
|
|
|
Test #2 aims to demonstrate the outcome when users allowed to enroll in MDM are given the opportunity to do so. Let’s repeat the same test with the user included in the Azure Security group INTUNE_USERS.
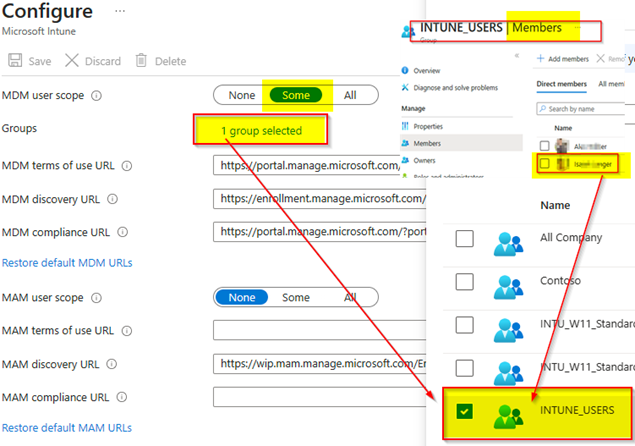
CLIENT: SEA-WS1 DOMAIN ADS on-premises: NO IS workgroup: YES Azure Security Group “Intunes_USERS” member: YES MDM User scope: > SOME > Azure Security Group “Intunes_USERS”
User which joins is MEMBER of the Security Group “Intunes_USERS” which is listed on the MICROOSFT Intune MDM SCOPE (1 Group selected) |
|
|
|
|
|
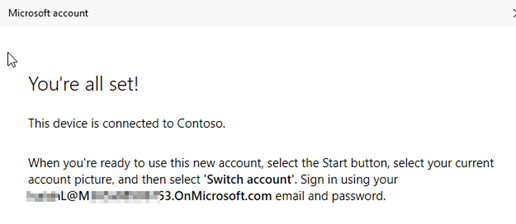
As the user joining the workgroup (BYOD) device to Azure is also a member of the Azure Security Group INTUNES_USERS, and this group is listed under Microsoft Intune Autojoin, the user has the capability to: a) Join the device to Azure and b) Simultaneously enroll the device into MDM/Intune.
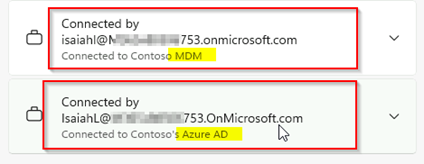
Above: MDM
Below: Azure JOINED |
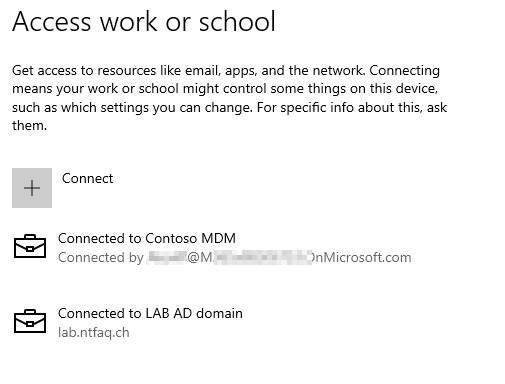
In Entra/Azure you see the device like this now:
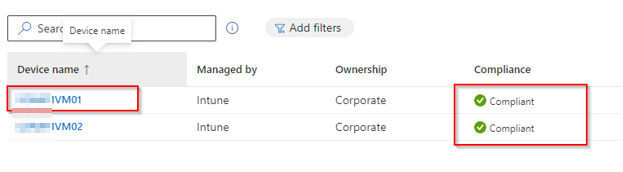
In Intunes/MDM you see the device like this:
|
|
|
|
|
|
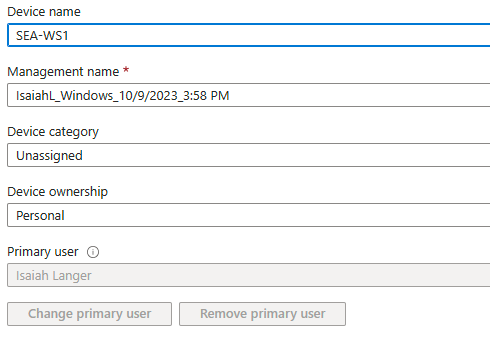
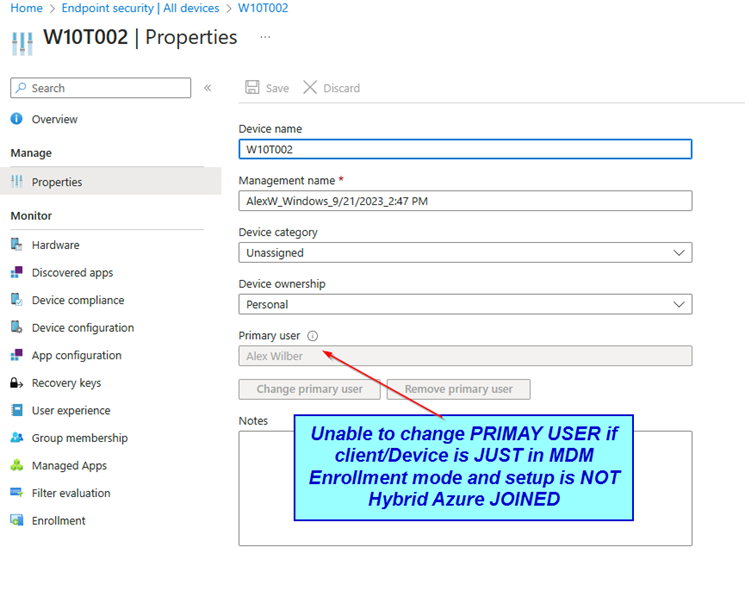
< You can’t change the PRIMARY user in Intunes/M365 Portal |

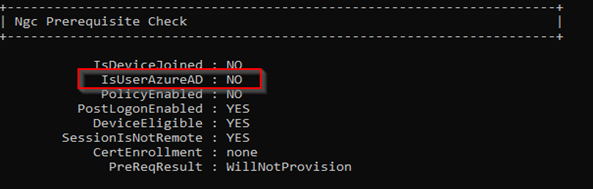
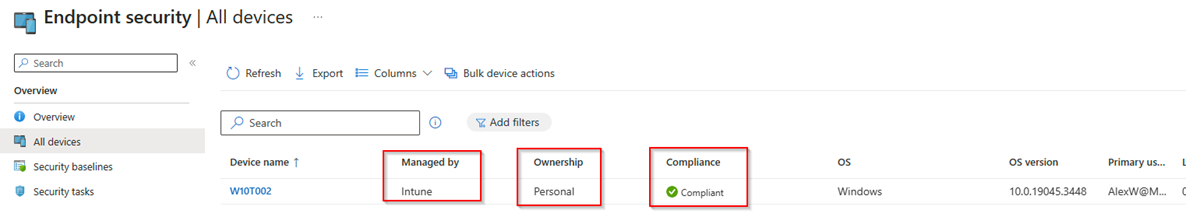
CLIENT: W10T002.lab.ntfaq.ch
DOMAIN ADS on-premises: YES
IS workgroup: NO
Azure Security Group “Intunes_USERS” member: YES
MDM User scope: > SOME > Azure Security Group “Intunes_USERS”
The sample client, W10T002.lab.ntfaq.ch, is joined to the on-premises Active Directory (ADS), without Hybrid Azure for devices. The MDM enrollment was manually done in Intune.
|
|
|
|
|
Ownership shows as ‘Personal,’ even if the device was joined to on-premises Active Directory (ADS) and then enrolled exclusively to MDM, without Hybrid Azure existing. |
|
Is this scenario you are NOT able to change the PRIMARY USER in Intunes. The buttons are greyed out.
Possible Steps to Address:
Keep in mind that the ability to change the primary user might be influenced by various factors specific to your organization’s setup and configurations, and the guidance provided might need to be adapted based on the details of your environment. |
Troubleshoot devices by using the dsregcmd command
https://learn.microsoft.com/en-us/azure/active-directory/devices/troubleshoot-device-dsregcmd


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.