Trellix ENS 10.X, T1056 – Key capture using PowerShell detected, Host intrusion buffer overflow
ExP:Illegal API Use Blocked an attempt to exploit
C:\WINDOWS\SYSTEM32\WINDOWSPOWERSHELL\V1.0\POWERSHELL.EXE, which targeted the GetAsyncKeyState API.
For efficient M365 and Exchange Online management, there are various methods available. While utilizing the PowerShell button within the Admin Portal is one option, it requires an Azure license for a separate IT account. Additionally, we explored the use of Remote Shell on various servers and working clients, uncovering some key insights.
We also tried the Remote shell to M365 on Several Server and working clients and found some important fact.
Most antivirus solutions, especially those adhering to MITRE rules, categorize the connection made through Remote Shell as a phishing attack for credentials (MITRE T1056 – Keylogger). It’s crucial to note that exclusions should be applied judiciously. We recommend excluding the T1056 rule only on machines where Exchange Admins will be actively working.
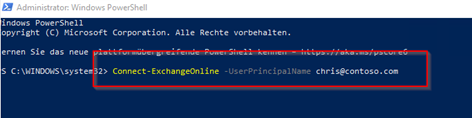
Install-Module -Name ExchangeOnlineManagement –Force
Connect-ExchangeOnline


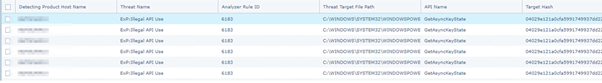
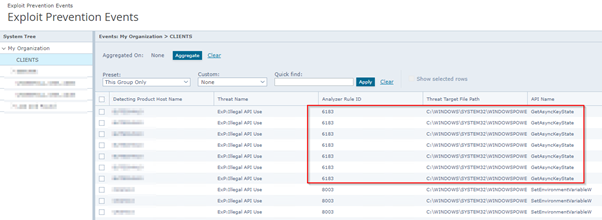
You can find and also exclude the API function call in Trellix EPO like this. I would like to state that you should only exclude the T1056 on machines where the Exchange Admin will work.
Select the EXPLOIT, checkbox, then bottom page left side, ADD Exclusion

Choose the POLICY applicable to the clients you wish to modify.
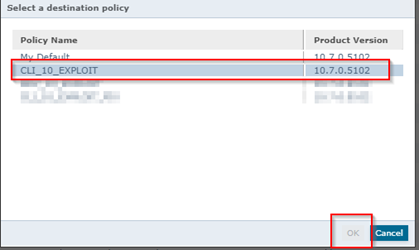
It’s imperative to exercise caution and refrain from excluding the MITRE rule for all end users, reserving this action for IT machines. Trellix ENS allows for comprehensive policies that cover a wide range, with the flexibility to add more fine-grained policies for specific machines or targets.
For your reference, the details of the detected threat are as follows:
T1056
|
Should you choose to disable the 6183 Analyzer rule in its entirety, navigate to your POLICY settings under “OTHERS.” Please note that this rule may not be enabled by default in your McAfee/Trellix environment.
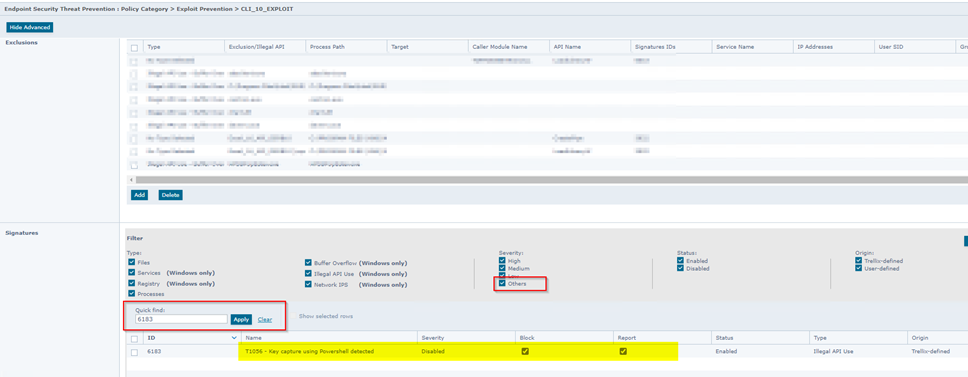
After the change the Connection should work:



 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.