English:
In-Place Upgrade: WSUS Server from Server 2016 to Server 2025
Good news for IT admins and engineers: An in-place upgrade from Windows Server 2016 to Server 2025 for WSUS is now fully feasible. During our tests, we successfully migrated the entire WSUS server role, including all prerequisites, WSUS content, console views, and approval settings, directly to the new OS version without issues.
In the past, we performed swing migrations for customers based on Technet/Learn articles. However, these did not always go smoothly. We often encountered issues that required re-approving all patches, even when using the downsync of approvals and views. This made the process time-consuming and error-prone.
The new in-place upgrade option eliminates these challenges, preserving all configurations and data seamlessly. If you are managing a WSUS environment and considering an OS upgrade, this one-step path to Server 2025 is a reliable and efficient alternative.
German:
In-Place-Upgrade: WSUS-Server von Server 2016 auf Server 2025
Gute Nachrichten für IT-Admins und -Ingenieure: Ein In-Place-Upgrade vom Windows Server 2016 auf Server 2025 für WSUS ist jetzt vollständig möglich. In unseren Tests haben wir die gesamte WSUS-Serverrolle erfolgreich migriert, einschließlich aller Voraussetzungen, WSUS-Inhalte, Konsolenansichten und Genehmigungseinstellungen, direkt auf die neue OS-Version ohne Probleme.
In der Vergangenheit haben wir für Kunden auf Basis von Technet/Learn-Artikeln Swing-Migrationen durchgeführt. Diese verliefen jedoch nicht immer reibungslos. Häufig mussten wir nach der Migration alle Patches erneut genehmigen, selbst bei Verwendung des Downsyncs der Genehmigungen und Ansichten. Dies machte den Prozess zeitaufwendig und fehleranfällig.
Die neue In-Place-Upgrade-Option beseitigt diese Herausforderungen und erhält alle Konfigurationen und Daten nahtlos. Wenn Sie eine WSUS-Umgebung verwalten und ein OS-Upgrade in Betracht ziehen, ist dieser ein-schrittige Weg zu Server 2025 eine zuverlässige und effiziente Alternative.
We mention:
- How to Backup the WSUS WID Windows Internal Database to Disk on the Server 2016
- Show the steps to upgrade the Server 2016 to 2025
- Re-Run the WSUS Post Setup
- Show the steps and categroy to patch Server 2025 from a 2016/2019/2022/2025 WSUS Server
- Check that all roles awhewre migrated correct
| Warning / Caution / Please read and keep in mind |
| There’s a lot of discussion about in-place upgrades of server OS. Microsoft seems under immense pressure from customer managers who were told that everything in the cloud would be easier, or they expect server migrations to work the same way as client OS upgrades (e.g., W10 to W11 or W11 to W11). You can even migrate directly from Server 2016 to 2025. However, an issue with the Windows Update Catalog led to certain patch management solutions incorrectly approving new server OS releases for both small and large customers. As a result, many were unexpectedly forced to try in-place upgrades for thousands of servers. As a reminder, the key factor in deciding whether an in-place upgrade is possible is the main application on or the role of the server. This will determine if an in-place upgrade is feasible. In the worst-case scenario, you could lose support SLAs for certain vendors or products if you handle it this way. This is a significant risk if you don’t approach the process carefully. We’ve seen IT service companies that clean up old storage and VMs to quick to reduce costs, but this approach adds another layer of risk to the migration process. We highly recommend creating an image or Veeam backup of the server’s state before starting the migration to ensure a fallback option. Sometimes, this isn’t possible with interconnected systems, and the risk of migration remains even with precautions in place. |
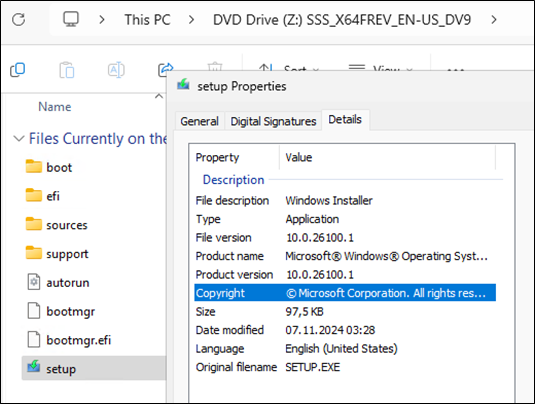
Here is the Server 2025 media we used for the inplace update of the Server 2016 to 2026.
10.0.26100.1 from 07.11.2024
Before you do an inplace upgrade we highly recommand to Backup:
- Make a Snapshots as example on the Hypervisor Vmware etc. of the machine
- Make or check your VEEAM Image of the machine
- A good options would be to make a DUMP of the SQL WID Windows Internal Database
For the SQL and WSUS you can find other usefull info in our two category:
https://www.butsch.ch/post/category/wsus/
https://www.butsch.ch/post/category/microsoft-server-os/sql/ (Backup, Size, Limits etc.)
| Steps to make a BACKUP/DUMP of the WSUS Server Windows Internal Database |
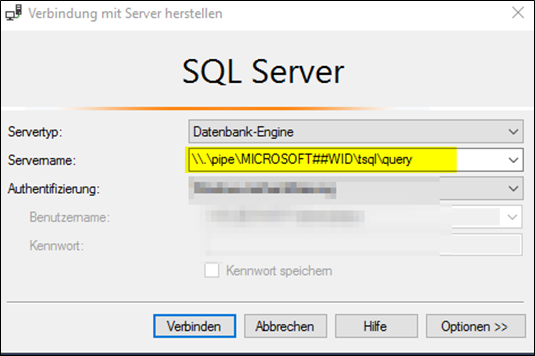
How to Connect to the Internal WID on WSUS Server 2016 and Backup/Dump the SQL Database to DiskIf you’re working with WSUS on a Server 2016 instance and need to back up or dump the internal WID (Windows Internal Database), here’s how you can proceed: Step 1: Access the Internal Database (WID)
Step 2: Install SQL Server Management Studio (SSMS)
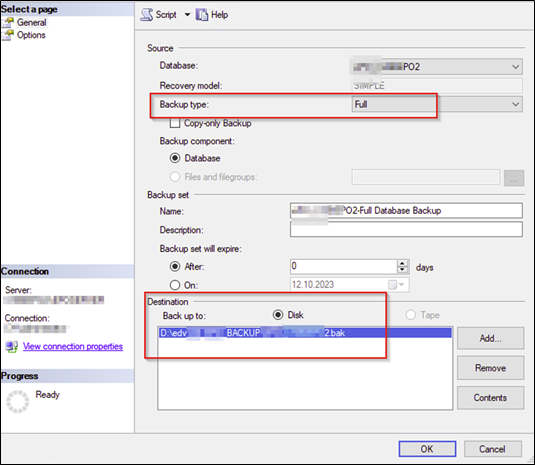
Step 3: Backup the WID Database (WSUS Database)
Sample:
|
Or reference this MS Learn article for the backup:
|
If you are sure you have a backup of all from the Server 2016 WSUS you can go ahead with the inplace upgrade.
Here are the steps for the in–place upgrade Server 2016 to 2025
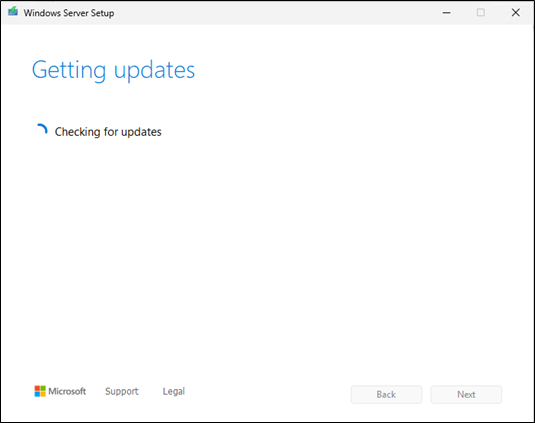
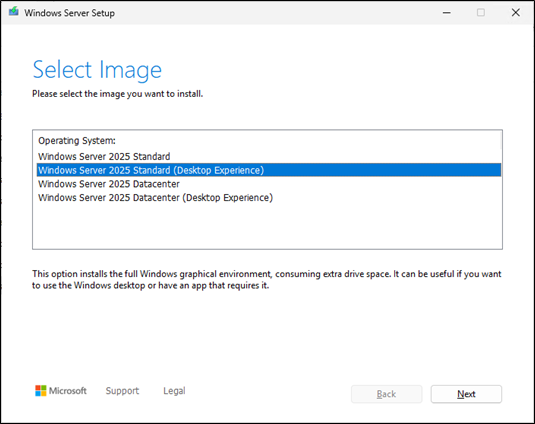
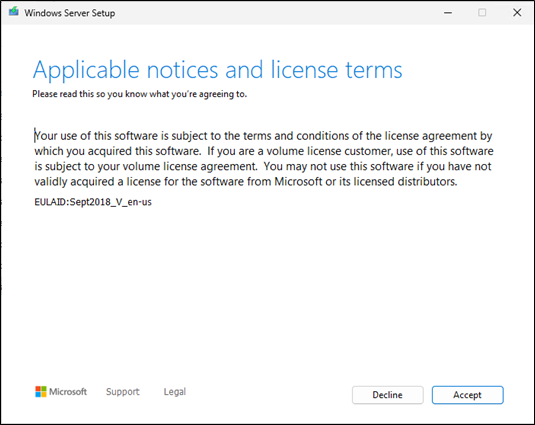
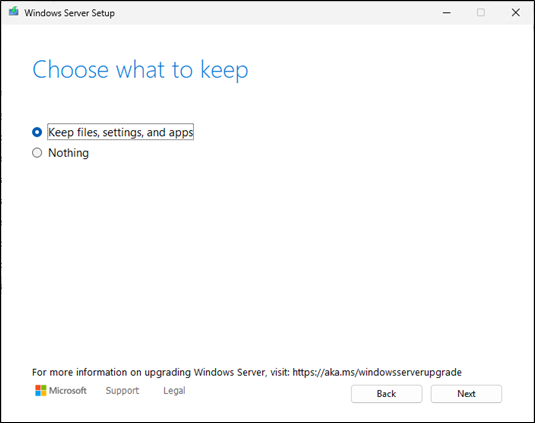
Server will do an auto reboot if all works fine
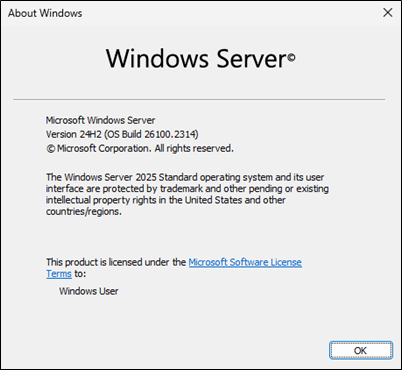
After first logon

Check the version so you know if he did a rollback or not.
Now the post setup for WSUS has to be re-done
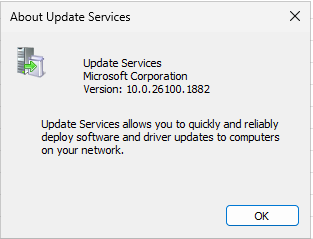
Checking WSUS release: 10.0.26100.1882
Lets see if he migrated / updated the WSUS Server role correct and also the WID (Windows Internal database)
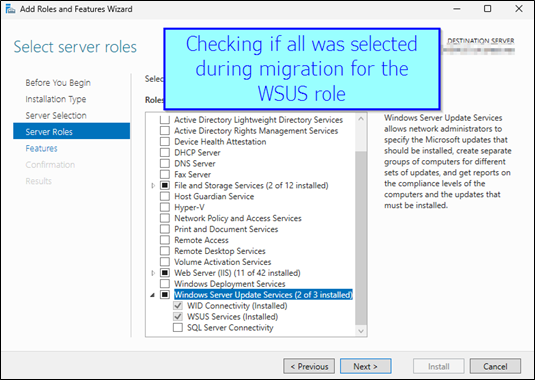
Just press Cancel, we just wanted to re-check if all is there it needs > All OK
If we open the WSUS MCC all is there and migrated from the 2016 WSUS
- The Computer Groups
- Assigning method via GPO
-
The View and Groups for sorting the updates
That looks very nice
compared to SWING Migration where we no matter how we did it we often did loose those views. 😉
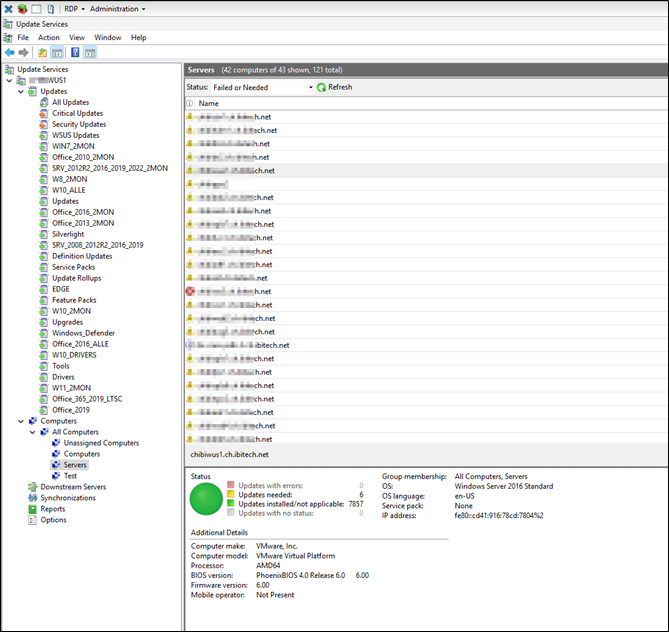
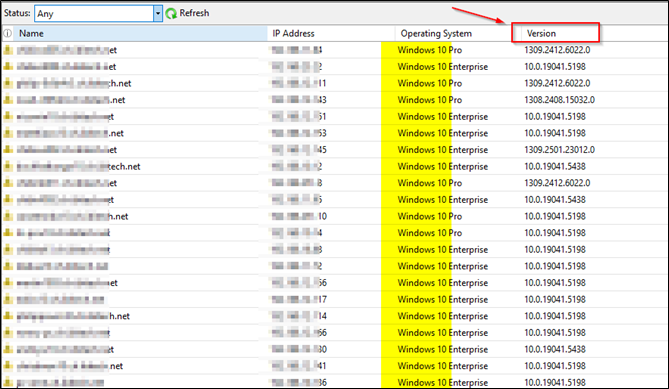
It sadly still shows “Opeating System” as Windows 10 Pro and Enterprise for our Windows 11 clients.
If you enable/show the “Version” column you can at least see it is a W11 client IS. But that is the case with allmost
any Management Server also like in Trellix EPO Server 5.10 SP1 so fair enough.
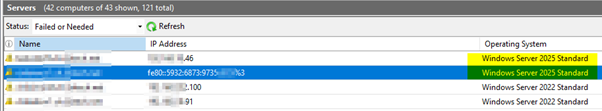
But it show the Server 2022 and 2025 OS correct
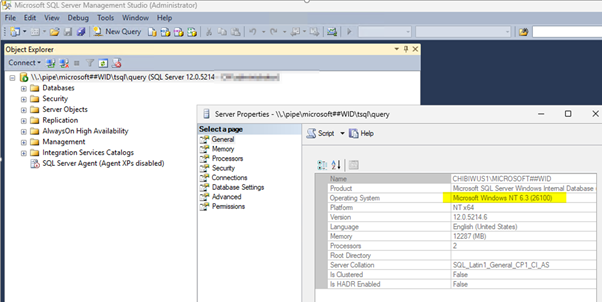
The SQL Server Management Studio we have on our WSUS Server was migrated nicely
Integrate Server 2025 category in WSUS
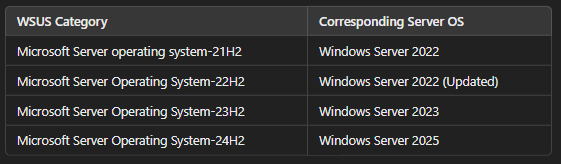
WSUS Category, Corresponding Server OS
| Microsoft Server operating system | 21H2, Windows Server 2022 |
| Microsoft Server Operating System | 22H2, Windows Server 2022 (Updated) |
| Microsoft Server Operating System | 23H2, Windows Server 2023 |
| Microsoft Server Operating System | 24H2, Windows Server 2025 |
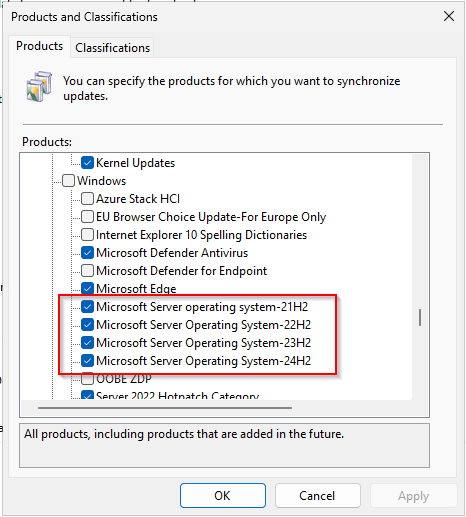
Lets patch the 2025, try selfupdate because of the IPV6 address we see for itself > OK works fine
Side notes:
We observed a McAfee/Trellix alert, but for the record, nothing was blocked.
We also saw this Tiworker.exe alert on a client running Windows 11 with the February 2025 Windows Updates. Therefore, it is not specifically related to Server 2025, but keep this in mind if you are updating in February or March.
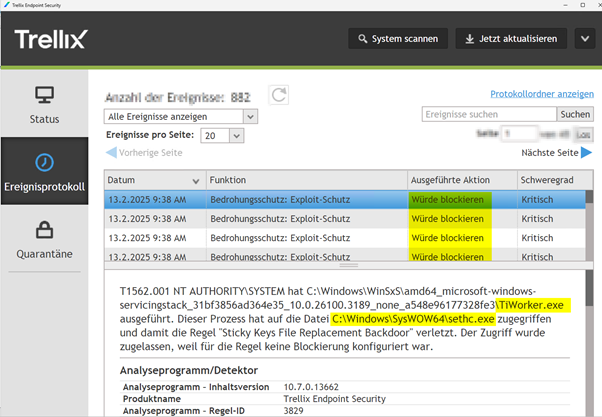
For those using McAfee/Trellix ENS 10.7 (latest as of December 2024), we encountered a “WOULD BLOCK” alert triggered by an Exploit/IPS rule involving Tiworker.exe. The Server 2016 instance had the latest ENS 10.7 release, with the Platform and Exploit modules istalled (no irewall, ATP, or Web modules).
| T1562.001 |
| T1562.001 NT AUTHORITY\SYSTEM hat C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.26100.3189_none_a548e96177328fe3\TiWorker.exe ausgeführt. Dieser Prozess hat auf die Datei C:\Windows\SysWOW64\sethc.exe zugegriffen und damit die Regel “Sticky Keys File Replacement Backdoor” verletzt. Der Zugriff wurde zugelassen, weil für die Regel keine Blockierung konfiguriert war. |
For the “McAfee bashers”: This is a MITRE standard T1562.001 compliance rule. If enterprise customers want to be MITRE compliant, they can enable this best-practice MITRE rule. If properly integrated into any AV product, it would likely have triggered as well, in our opinion. We did not check the Windows Defender PASSIVE Mode logs, which also run in parallel when Trellix is active for script scanning.
Workaround: You could exclude Tiworker.exe using its MD5 checksum in the EXPLOIT rules of ENS. A better approach would be to integrate your ePO and Trellix infrastructure with the TIE server, which can manage file changes with the same name based on certificates and history (recommended for environments with 1000+ clients). However, we do not recommend running the ENS ATP module or TIE components on Server OS without external consulting or sufficient internal expertise.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.