
Google Chrome.exe 124 and Edge Chromium may have problems connecting Webserver behind older firewalls or proxy OR certain security device do not filter HTTPS/TLS websites anymore.
The problem has started around 22.04.2024 and is growing.
This could effect you if:
You run or someone else runs a Webserver or any service with https / SSL / TLS 1.3 behind:
- PPPoE WAN
- Celuar Media like G4/G5 networks (Depending on SIM ISP/provider > One SIM card works the other SIM not OVER same GX routers > People reported who have DUAL IM for data)
The new cipher X25519Kyber768 that is activated on client side with the Chrome 124 seems at the end to generate larger paket header and old friend the MTU-Size [maximum segment size (MSS)] comes into play again.
It will affect your user who use chrome to access a webserver, which has that problem.
The latest version of Chrome, 124, introduces a new encryption mechanism called X25519Kyber768, designed to resist quantum attacks.
Anounced NOV 2023 now seems to be getting default and active > As a step down this path, Chrome will begin supporting X25519Kyber768 for establishing symmetric secrets in TLS, starting in Chrome 116, and available behind a flag in Chrome 115.
This hybrid mechanism combines the output of two cryptographic algorithms to create the session key used to encrypt the bulk of the TLS connection.
However, this feature might inadvertently lead to more immediate connectivity issues than it seeks to solve.
Quick workaround:
For Google Chrome Browser
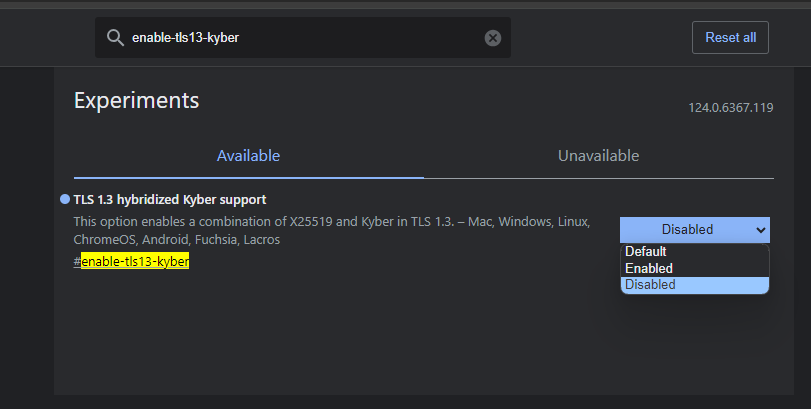
chrome://flags
enable-tls13-kyber
For MS Edge Chromium Browser
edge://flags
enable-tls13-kyber
MTU/ MSS Size
For diagnose of MTU/MSS sizes of your PPPoE WAN customers/problems you can use our freeware tool crlcheck.exe. It should help you to calculate the correct sizes from LAN>WAN.
You can even change the sizes per mouseclick with that tool if you run it elevated.
Change MTU size Fortigate
“set tcp-mss 1452” to the LAN/INSIDE interface/s configuration of Fortigate. Same problems may accout with other FW like PaloAlto, Sonicwall etc.
Setting TCP MSS value – Fortinet Community
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Setting-TCP-MSS-value/ta-p/194518
Long Term workaround > Update what is bewtween your Browser and the Webserver. Google says you had since NOV 2023? Firewall/IPS, Webfilter, SSL Sniffers, Proxy, Web protection etc.
Fortigate with new IPS engine
Webfilter is in place on a flow mode firewall policy on the FortiGate to block certain websites through a static URL filter.
The websites are blocked when using Firefox or Edge browser, but it is possible to navigate to these websites when using Chrome.
Web filter is not blocking websites on Go… – Fortinet Community
PaloAlto

Chrome Blog
Chromium Blog: Protecting Chrome Traffic with Hybrid Kyber KEM
https://blog.chromium.org/2023/08/protecting-chrome-traffic-with-hybrid.html
envoyproxy
x25519kyber768 support · Issue #33941 · envoyproxy/envoy · GitHub
https://github.com/envoyproxy/envoy/issues/33941
PureVPN
Google Chrome’s Post Quantum Cryptography Breaks TLS Connections (purevpn.com)
https://www.purevpn.com/blog/news/google-chromes-post-quantum-cryptography-breaks-tls-connections/
Some Posts
https://www.reddit.com/r/chrome/comments/1c8ucus/problems_with_chrome_and_cloudflare/
https://www.reddit.com/r/chrome/comments/1c83js4/firewall_issues_after_latest_update/
https://www.reddit.com/r/sonicwall/comments/1cac4ii/content_filter_blocking_cfs_legitimate_traffic/
https://www.reddit.com/r/sysadmin/comments/1ca1chq/hello_im_new_to_both_this_subreddit_and_a/
What is X25519Kyber768?
X25519Kyber768 is a cryptographic algorithm that combines two different primitives: X25519 for key exchange and Kyber768 for post-quantum secure encryption. Let’s break it down:
-
X25519
This is an elliptic curve Diffie-Hellman (ECDH) key exchange algorithm. It’s widely regarded as secure and efficient, even against potential quantum computing threats.
-
Kyber768
Kyber is a post-quantum secure key encapsulation mechanism based on the Learning With Errors (LWE) problem. It provides security against attacks from both classical and quantum computers. The “768” in Kyber768 refers to the security level it provides, indicating that it offers a high level of protection.
Combining these two primitives, X25519Kyber768 aims to provide strong cryptographic security against both classical and quantum computer attacks. In the context of Chrome’s latest version, implementing X25519Kyber768 is a proactive measure to ensure that users’ data remains secure in the face of advancing cryptographic threats, particularly those posed by quantum computing technologies.
https://www.rfc-editor.org/rfc/rfc8410
Fortigate reverse effect that their URL filter is NOT working an users are unprotected because of the new Cipher.
This would mainly happen to Fortiagte Device which have not active Fortiguard Service and do not get
updated IPS engines through those updates.
|
Technical Tip: Google Chrome Not Blocking Websites with FortiGate Web Filter |
|
Description: This technical tip addresses the issue of the web filter not functioning properly on Google Chrome browsers, while working correctly on other browsers. Solution: Users may encounter the following scenario: the web filter is configured on a flow mode firewall policy within FortiGate to restrict access to certain websites via a static URL filter Scope: This tip pertains to FortiGate users encountering difficulties with their web filter specifically on Google Chrome. While websites are successfully blocked on Firefox or Edge browsers, users find they can still access these sites when using Google Chrome. If encountering this issue, there are three potential solutions: 1. Manually update the IPS engine of the relevant FortiGate device. Refer to the following procedure: “Technical Tip: How to manually upgrade the IPS Engine.” 2. Open a support ticket with Fortinet to obtain the latest IPS Engine and manually update it. 3. Disable TLS 1.3 hybridized Kyber support in the Google Chrome browser: – Navigate to chrome://flags/ – Search for “TLS 1.3 hybridized Kyber support.” – Set the action to “Disable.” Additionally, for users employing flow-based inspection, ensure that the “unsupported-ssl-cipher” setting is configured to “block” within the firewall policy: config firewall ssl-ssh-profile edit “profile-name” config https set unsupported-ssl-cipher block end end By default, this option bypasses the session when an unsupported cipher is detected. To enforce blocking, set the “unsupported-ssl-cipher” parameter to “block.” set unsupported-ssl-cipher ? allow Bypass the session when the cipher is not supported. block Block the session when the cipher is not supported. Following these steps should ensure that the designated websites are properly blocked, and the web filter functions as expected. |
Google Chrome, Chrome browser,
Web browser, Google, Chrome update, Chrome issues, Chrome troubleshooting, Chrome settings,
Chrome flags, Edge Chromium, Microsoft Edge, Chromium browser, Edge browser, Edge update, Edge issues,
Edge troubleshooting, Edge settings


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.