ADAC = NOT Deutscher Pannendienst 😉
Fine grained Password Policy in 2013 R2 Domain Active Directory, Error 4625 event
Sometimes you need accounts TO None expire or not getting Locked out. We all now it’s stupid in security terms but if the software has a bug and locks the account you have to hurry. Search on ALL of the Domain Controller for event 4625. There you should see the client who does it. There also lockout/whoislocked scripts which does that. (Account locked)
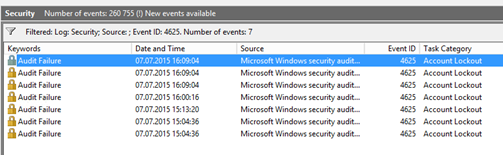
The regular Domain password policy is here:
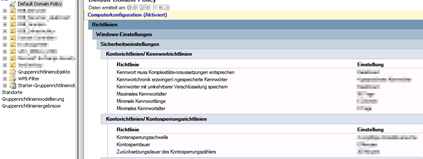
But we want a second one with different settings and only for a few users in a security group
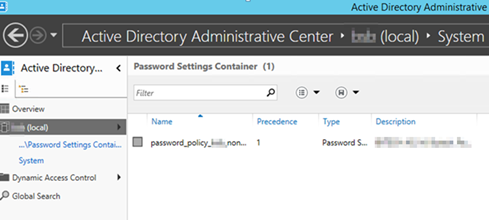
New way with ADAC on 2012R2
https://technet.microsoft.com/de-CH/library/hh831702.aspx
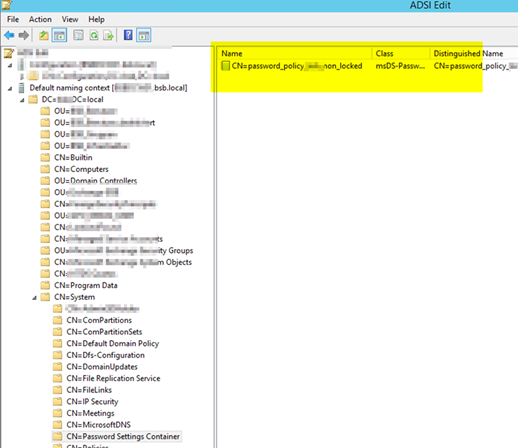
Old way with ADSIEDT.MSC
http://www.grouppolicy.biz/2011/08/tutorial-how-to-setup-default-and-fine-grain-password-policy/
https://technet.microsoft.com/en-us/library/cc754544(v=ws.10).aspx
Make a new ADS group: sg_gpo_password_policy_bsb_non_locked and make the accounts which should have special password policy member of that group “Only user accounts”

Go to SYSTEM
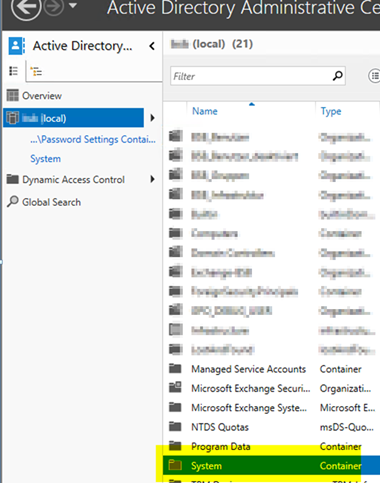
Go to PASSSWORD Settings Container
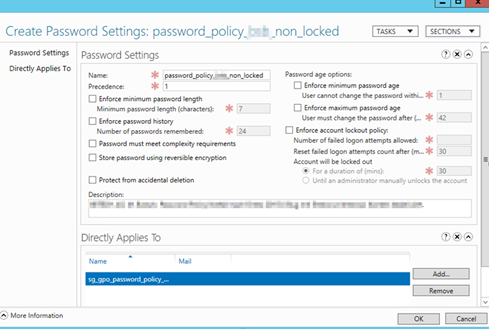
Choose “Directly applies to” and make sure you choose the correct Security Group you made for this.
Under cmd on DC do a:
Repadmin /syncall
Its finished and working
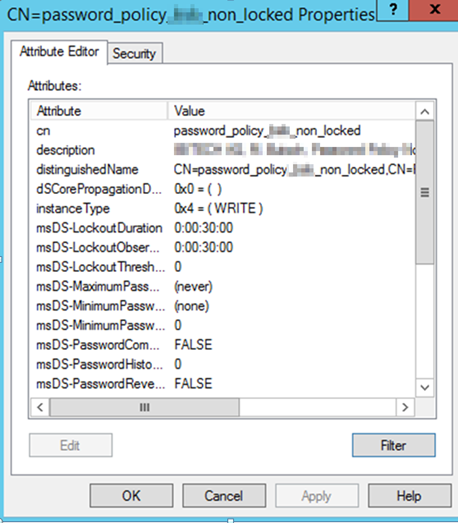
CROSS CHECK old Method with ADSIEDT


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.