Exchange CVE-2024-21410 2013/2016/2019 Extended Protection Kemp-F5 and Modern Hybrid Mode problem
Primary target which is part of the attack: Make sure you ROLLOUT the Outlook.exe 02/2024 Patch. That is the most important thing. Esp. On Home Office/Remote Office which may have SMB/445 to WAN open and for VPN users NO traffic to/via VPN-2-HQ policy (Which is not good in this case)
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-21413
Microsoft Office 2016 (32-bit edition) 5002537 Security Update 16.0.5435.1001
Microsoft Office 2016 (32-bit edition) 5002467 Security Update 16.0.5435.1001
Microsoft Office 2016 (32-bit edition) 5002522 Security Update 16.0.5435.1001
Microsoft Office 2016 (32-bit edition) 5002469 Security Update 16.0.5435.1001
Microsoft Office 2016 (32-bit edition) 5002519 Security Update 16.0.5435.1001
For the current Exchange NTLM Leaks CVE-2024-21410
For older Leaks: CVE-2022-24516,CVE-2022-21979,CVE-2022-21980,CVE-2022-24477,CVE-2022-30134
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-21410
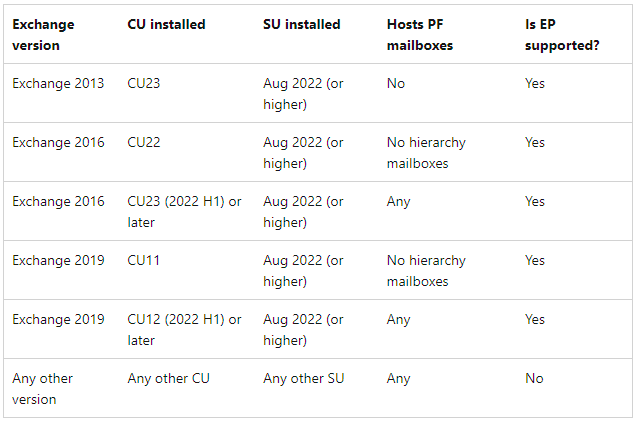
- Exchange 2019 Update CU14: Ensure to apply Exchange 2019 Update CU14 for necessary security enhancements. (*LINK4)
- Exchange 2013/2016: If you’re using Exchange 2013/2016 with the latest CU, you NEED to enable Extended Protection (EP) with the Powershell Script (Read all important pitfalls FIRST > This is not a TRIAL and ERROR best practice)
-
Exchange 2013 madatory needs all Windows Updates up to 02/2024 so the EP will work. It will not work with PUBLIC FOLDER’s on 2013 in Coexistence Mode (2013+2016) or (2013+2019).
https://microsoft.github.io/CSS-Exchange/Security/ExchangeExtendedProtectionManagement/
Powershell: ExchangeExtendedProtectionManagement.ps1 (EP)
Warning: Even in a DAG Cluster setup you will NEED downtime and can’t change things adhoc live.
-
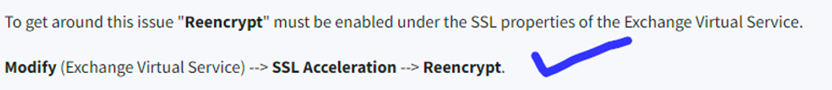
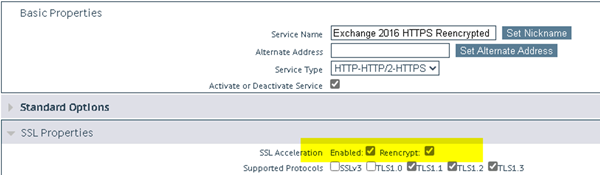
EP > Please take care for KEMP/F5 Load Balancer Enviroments (You need to change KEMP/F5 things rather complex/downtime). SSL Offloading and EP = NO, SSL Bridging (You need same Certificate on every device!)
-
EP > Please take care for “Retention Policy containing Retention Tags which perform Move to Archive actions”
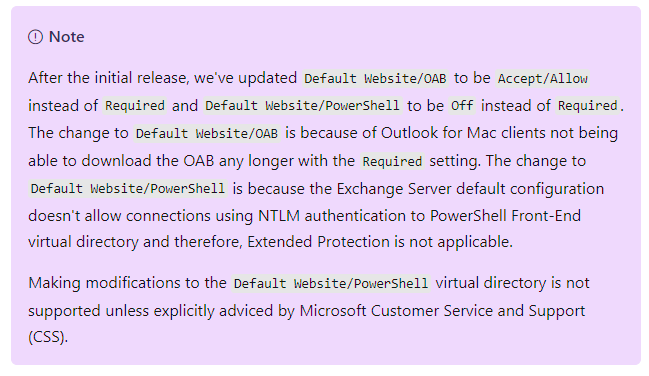
- EP > Microsoft fixed/changed/reduced-security for Outlook for MAC for OAB (Offline Adressbook) yo yes it work MAC now
- EP > Please take care if in Modern Hybrid Mode. (Do not activate Extended Protection just for test). If you have a FULL Hybrid mode with a long running MIGRATION PHASE you are with high chance in CLASSIC mode (Good/You can enable EP)
-
Exchange 2013 PUBLIC FOLDER and EP does not work in Coexistence Mode (1×2013+1×2016) or (1×2013+1×2019).. You have to finiesh the migration and move of the PUBLIC folder finally to 2016/2019 or M365/EXO. This will take 1-3 days of runtime (Replication) and downtime. Regarding Authentication NTLM/Kerberos/TLS this is the part which mostly generates Authentication POP’ups WHICH you don’t want! (The problem is THAT is what we change with EP!)
Public Folder an EP
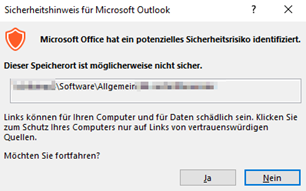
Running ExchangeExtendedProtectionManagement.ps1 we have just seen a case where the OAUTH Certificate was expired.
To run the ExchangeExtendedProtectionManagement.ps1 your OAUTHcertificate has to be valid and also your INTERNAL Self Signed 5 years “Exchange Server” certificate (builtin) has to be non-expired.
EP Run script ELEVATED and check the “OAUTH” and internal “Exchange Certificate”
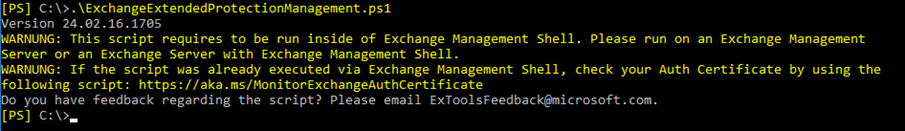
Here is how to renew the OAUTH cert (Plan 1-2H waiting time because of timezone bug)
Already Expired:
Some tool to catch the moment you have to renew (Because of the time zone difference behaviour)
https://microsoft.github.io/CSS-Exchange/Admin/MonitorExchangeAuthCertificate/
For OAUTH please take care if you are in hybrid mode also here. The change of the OAUTH certificate normaly should be DONE prior it getting expired. See more info (And why this happens) with time zone difference here: https://www.butsch.ch/post/M365Exchange-Hybrid-OAuth-Testing-command-OAuth-Cert-out-of-sync-4001-IIS-VDIR-OAuth-wrong/

Warning built in now:
|
|
|
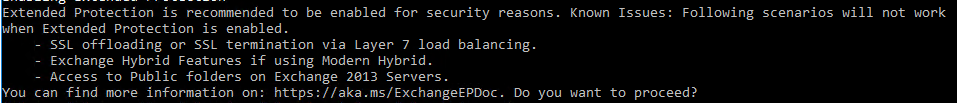
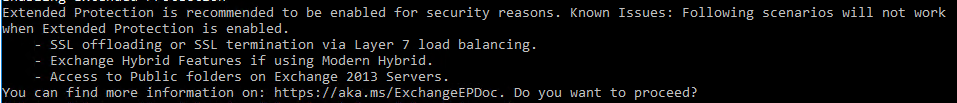
Enabling Extended Protection Extended Protection is recommended to be enabled for security reasons. Known Issues: Following scenarios will not work when Extended Protection is enabled. – SSL offloading or SSL termination via Layer 7 load balancing. – Exchange Hybrid Features if using Modern Hybrid. – Access to Public folders on Exchange 2013 Servers. You can find more information on: https://aka.ms/ExchangeEPDoc. Do you want to proceed? |
Warning Load Balancer:
-
Load Balancer Considerations: Users with KEMP or F5 Load Balancers and DAG Exchange Clusters must adjust Load Balancer settings cautiously. Ad-hoc installations can disrupt the Exchange environment.
- Load Balancer or WAF/PROXY: SSL Offloading is not working with Extended Protection
-
Load Balancer or WAF/PROXY: SSL Bridging, you MUST use the same Serial Certificate for all boxes/appliance and on the exchange.
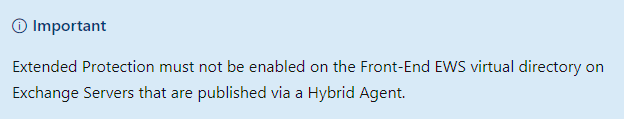
Warning MODERN Hybrid Mode (The Hybrid setups with HYBRID-Agents MSI)
-
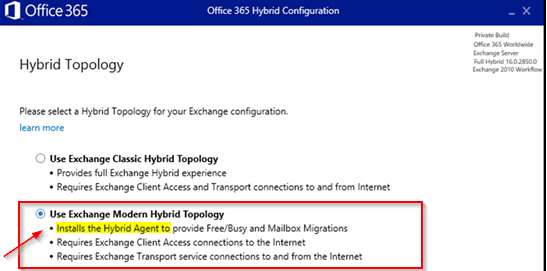
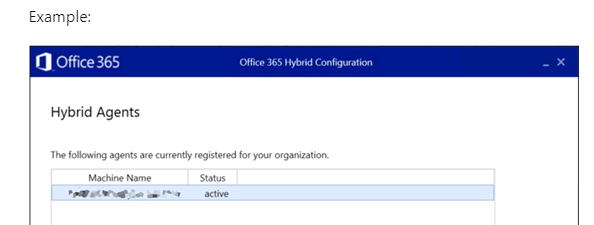
Exchange Modern Hybrid Topology: Enabling Extended Protection in “Exchange Modern Hybrid Topology” is NOT supported. If you run in “Modern Mode” you are using an “Hybrid Agent” (A MSI Agent you had installed). See below to find out if you have “CLASSIC” or “Modern Hybrid” activated in your Hybrid enviroment.
In HCW Hybrid Wizard GUI:
https://learn.microsoft.com/en-us/exchange/hybrid-configuration-wizard-options
|
Attention Hybrid Environment Administrators: |
|
|
|
|
|
If your organization relies on a hybrid Exchange environment, heed this crucial information regarding Extended Protection and Modern Hybrid configuration:
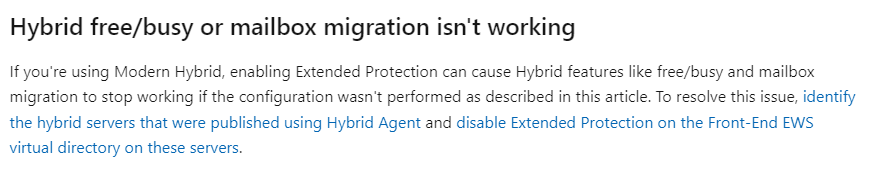
Warning: Enabling Extended Protection on hybrid servers configured with Modern Hybrid settings poses a severe risk to operational stability.
Danger: Incompatibility exists between Extended Protection and Modern Hybrid configuration. Attempting to enable Extended Protection on servers operating under Modern Hybrid settings will result in catastrophic disruptions, jeopardizing essential functions like mailbox migrations and Free/Busy functionalities.
Action Required: Take immediate action to safeguard your hybrid environment:
Identify all Hybrid Servers published via the Hybrid Agent.
DO NOT enable Extended Protection on these identified servers to avoid operational disruptions. Failure to comply with these directives may lead to significant service interruptions and operational downtime.
This warning is of utmost importance for maintaining the integrity and functionality of your hybrid Exchange environment. |
|
|
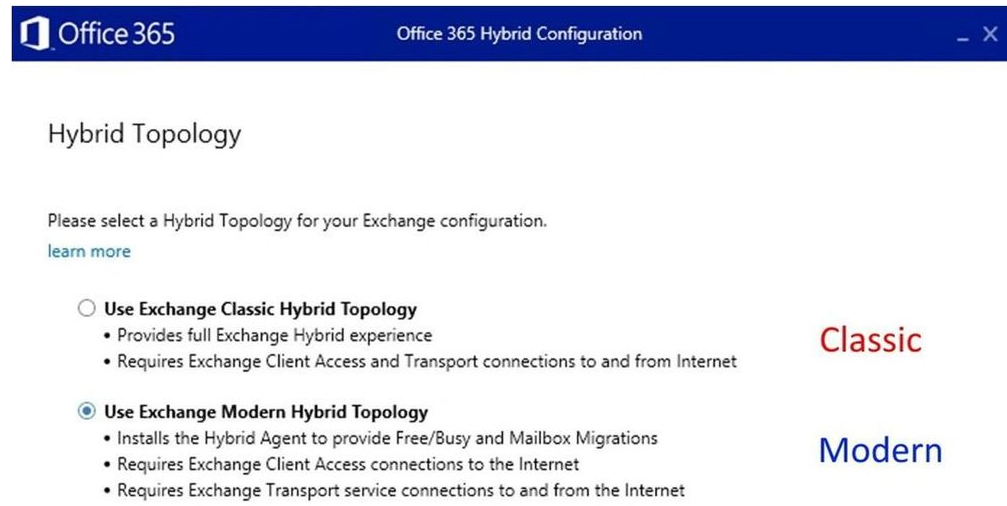
Here is a screenshot where you see the “Modern Hybrid” which will NOT work with Extended Protection
|
|
Hybrid Configuration wizard >HCW/Hybrid Mode on-premises<>M365/EXO/Cloud customers: Re-check what you have active by GUI:
|
|
|
|
|
|
|
|
|
|
|
Relevant/Important SCREEN where you choose “CLASSIC” or “MODERN”. Notice that with the “Modern Hybrid Topology” you had to install an “HYBRID AGENT” for Free Busy and Mailbox Migration. If you DO NOT have that AGENT installed you did choose CLASSI Mode the time you setup the HCW. |
|
|
Trick to identify if you are in CLASSIC or MODERN Hybrid MODE or IF you EVEN are in “Hybrid Mode or not!”
- The Modern Hybrid Mode uses Agents (Not the HCW Hybrid Configration Wizard tool). After you did RUN the HCW and choosed the HYBRID Mode > Then if you choosed MODERN Hybrid MODE > After that you had to Deploy/Install some Agent via the HCW or with MSI package.
-
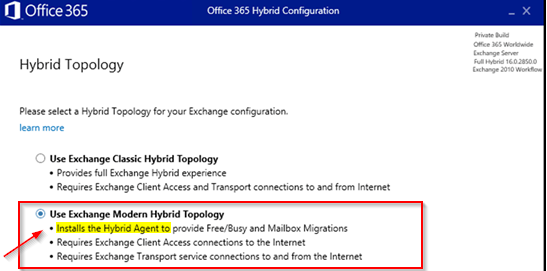

You maybe installed additional “HYBRID AGENT” like with “Msiexec /i MSHybridService.msi”.

If you NEVER done BOTH that THEN to 99% your are in CLASSIC Hybrid Mode and you can activate EP (If you checked any other points).
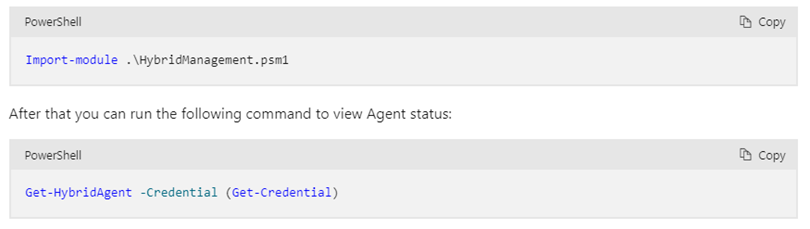
Check “Hybrid-Agent” with PowerShell:
Import-module .\HybridManagement.psm1
After that you can run the following command to view Agent status:
Get-HybridAgent -Credential (Get-Credential)
Trick to identify if you are in CLASSIC or MODERN Hybrid MODE or IF you EVEN are in “Hybrid Mode or not!”
|
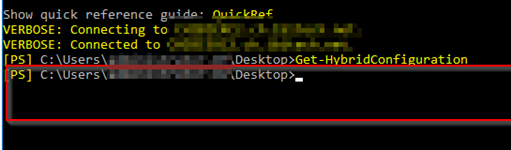
M365/EXO side: Connect-ExchangeOnline -UserPrincipalName <YourAdminAccount> -ShowProgress $true Get-HybridConfiguration | Select-Object -ExpandProperty ModernHybrid On-premises on the Exchange 2013/2016/2019: Get-HybridConfiguration | fl C:\Windows\system32>Get-HybridConfiguration | fl RunspaceId : ************************** If nothing appear and you have the permission THEN you are NOT in ANY on-premises <> M365/EXCO/Cloud Mode
Above: That customer has NO Hybrid Mode |
|
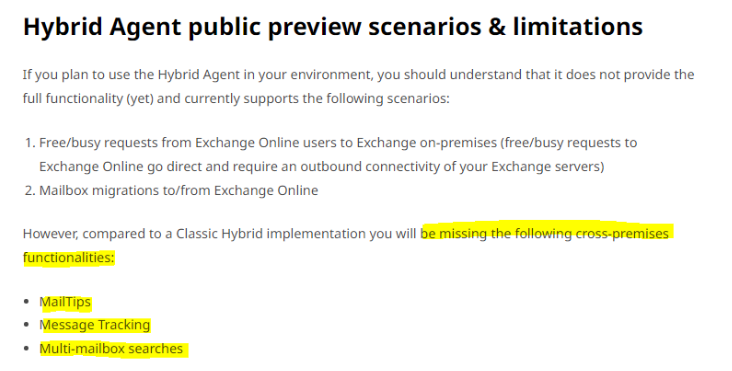
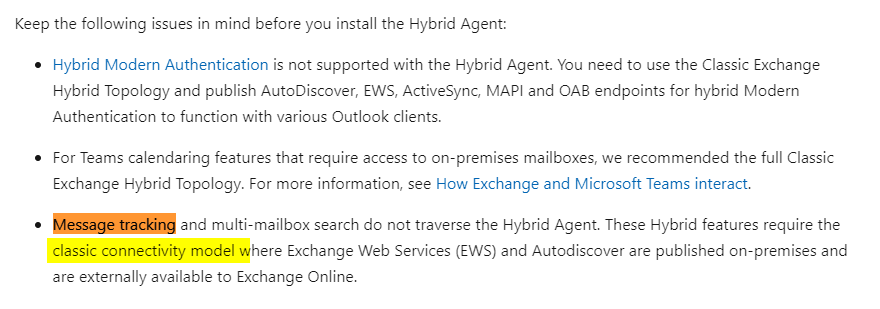
IF under FEATURES: You see “Mailtips”, “MessageTracking” you are in CLASSIC MODE |
|
|
|
IF under FEATURES: You see “Mailtips”, “MessageTracking” you are in CLASSIC MODE |
|
|
|
https://learn.microsoft.com/en-us/exchange/hybrid-deployment/hybrid-agent |
Technical Scenario Overview:
Microsoft’s February 14, 2024 advisory updates detail critical vulnerabilities in Microsoft Exchange Server (CVE-2024-21410) and Outlook (CVE-2024-21413), both rated 9.8 on the CVSS scale. These vulnerabilities allow attackers to exploit NTLM relay weaknesses, gaining unauthorized access and potentially executing code.
Exchange Server Vulnerability (CVE-2024-21410):
The CVE-2024-21410 vulnerability, addressed in the February Patch Tuesday, facilitates unauthorized access to Exchange Servers. Exploiting this flaw, attackers can use stolen Net-NTLMv2 hash values to authenticate and execute actions with the victim’s permissions. Notably, this vulnerability carries a CVSS score of 9.8, signifying its critical severity.
Mitigation Measures:
To address these vulnerabilities, IT security personnel should prioritize implementing Extended Protection (EP) features. Exchange Server 2019 CU14 includes EP as a default security measure. For older versions, manual activation of EP is necessary. Microsoft introduced EP as an optional feature in Exchange Server 2013 (End of Support), 2016, and 2019.
Please plan this carefully if you have KEMP/F5 Load Balancers or you have a HYBRID Setup.
Configuration and Verification:
Configuration guidelines and prerequisites for EP activation are available in Microsoft’s documentation. The “ExchangeExtendedProtectionManagement.ps1” script facilitates pre-activation configuration checks to prevent post-activation issues. Additionally, the HealthChecker Tool aids in verifying EP activation status on Exchange Servers.
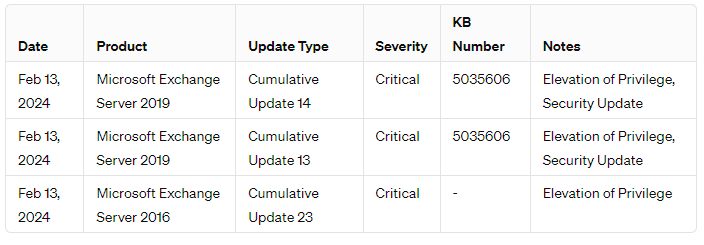
Patch Application:
While Microsoft assesses the likelihood of exploitation for CVE-2024-21413 as low, prompt patching is recommended. Applying Cumulative Update 14 for Exchange Server 2019 (KB5035606) and reviewing additional security advisories from the recent Patch Tuesday are crucial steps in maintaining system integrity and security.
Links used for research:
LINK0:
Exchange Release and Build numbers:
LINK1:
CVE-2024-21410 – Microsoft Exchange Server Elevation of Privilege Vulnerability
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-21410
LINK2:
Configure Windows Extended Protection in Exchange Server
LINK3:
ExchangeExtendedProtectionManagement Tool
https://microsoft.github.io/CSS-Exchange/Security/ExchangeExtendedProtectionManagement/
Powershell: ExchangeExtendedProtectionManagement.ps1
LINK4:
Cumulative Update 14 for Exchange Server 2019 (KB5035606)
LINK5:
HealthChecker Tool
https://microsoft.github.io/CSS-Exchange/Diagnostics/HealthChecker/
LINK6:
CVE-2024-21413 – Microsoft Outlook Remote Code Execution Vulnerability
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-21413
Fromt KEMP itself:
Extended Protection enabled in Exchange Server (KB5017260):
https://support.microsoft.com/en-us/topic/extended-protection-enabled-in-exchange-server-kb5017260-edee0d85-f65e-4e19-a52c-e63583ce9727#:~:text=Extended%20Protection%20enhances%20the%20existing%20authentication%20functionality%20in,be%20supported%20on%20servers%20that%20run%20Exchange%20Server
Exchange Server Support for Windows Extended Protection:
https://microsoft.github.io/CSS-Exchange/Security/Extended-Protection/
-
The Master LINK for EP Extended Protection done by MS after the phone lines where busy….
02/13/2024
Yes it works for Apple Macintosh MAC now because they did not lock it down fully. We wait for an exploit on MAC with Exchange now right? It is just the OAB Offline Adressbook where all the confindential data Like Phone Number and private numbers are in….


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.