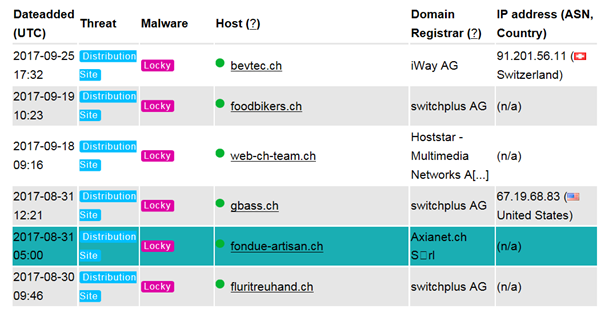
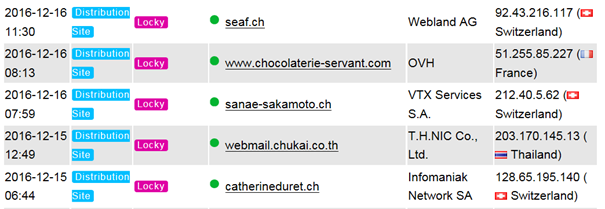
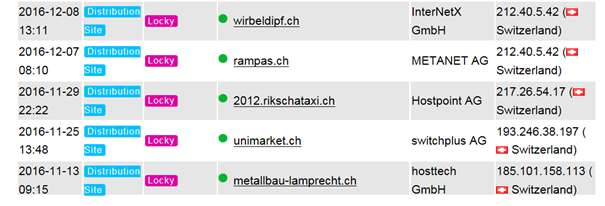
Domains with .CH (Switzerland) extension active spreading Locky Ransomware in 2016/2017.
We would like to state that the provider almost can’t do anything if the infect is with a hosting website and the customer has access via FTP and the customers client gets targeted. If they have a key logger or snigger on the client running and the user connects via FTP or portal they have access to the website. Often management solutions which providers offer to their customer have exploits too or people run unsecure blogs and users are able to post to that blog and inject code. Most providers with expensive IPS and IP-reputation Firewall will block access to those websites as soon as someone knows that they spread new variants. However only if someone reports the infection or the Antivirus send info back to P2P/Cloud as sample GTI Network from Mcafee.
80% of below samples did not infect via the Main domain thus as example www.sample.ch and mostly by some random string www.sample.ch/rtzdiiU64z which then leads to the malware dump code. We think the first init still has happened by E-Mail Spam which then leads to the specific URL.
The risk that a URL reputation Firewall will block such Domains is slighter lower so they have more success. Also the human Enduser factor plays a role if you see a URL from your own country which sounds normal.
List pulled from www.abuse.ch in 01/2019
Check out the website it offers extreme good lists of such things.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.