CVE-2024-38063, CVSS 9.8
|
|
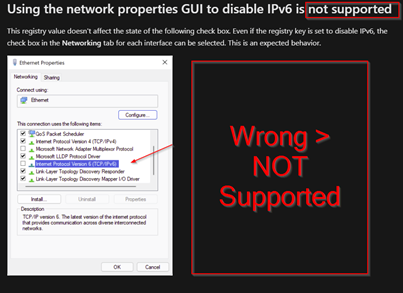
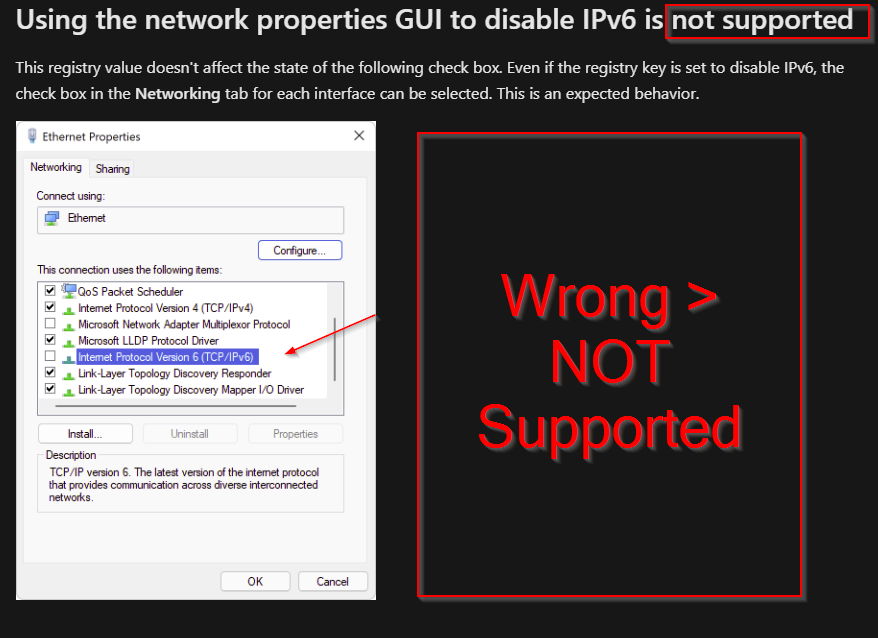
Using the network properties GUI to disable IPv6 is not supported This registry value doesn’t affect the state of the following check box. Even if the registry key is set to disable IPv6, the check box in the Networking tab for each interface can be selected. This is an expected behavior. |
CVE-2024-38063, CVSS 9.8, how to Import the older 2008R2 + 2012R2 patch into WSUS.
16.08.2024: Tested on German and US-English OS:
Server 2008R2,2012,2012R2, 2016, 2019, 2022 (Trellix EPO, WSUS Server, Rapid 7, Citrix Servers, Exchange 2016/2019 Servers incl. DAG Cluster, DC all OS version from oldest to latest.
NO current problem seen from what we can see.
Recommandation 16.08.2024
- There is a patch from 2008-2022+ Server so use it
- If you can’t patch then as least options CAREFULLY consider disabling IPV6 the correct way and fully (Not on Cluster, Exchange, Domain Controllers etc.) We have all the info below on how to do it correct (NOT in the GUI and just uncheck IPV box). Prefer IPV4 over IPV6 settings in Registry WILL NOT protect you
CVE-2024-38063
- Only IPv6 enabled endpoint are affected
- Do not disable IPV6 on Exchange, Cluster, DAG, Domain Controller, Direct Access (MS VPN) etc.
- IF you disable IPV6 do it the right way and NOT via GUI and unselect IPV6 checkbox ONLY (WRONG) See at end of this POST on how to do it correct and also NOT only change to Prefer IPv4 over IPv6 (Which would not stop CVE-2024-38063)
- There is a patch released 15.08.2024 from MS for Server 2008/2008/2012/2012R2, which can be downloaded from Microsoft without an ESU (Extend Support contract)
- There is a strange message about the 24H2 not released OS (you might first see this on mobile when you do not expand the KB), which causes most people to overlook how important this patch is (even if you do not actively support IPv6 in your network).
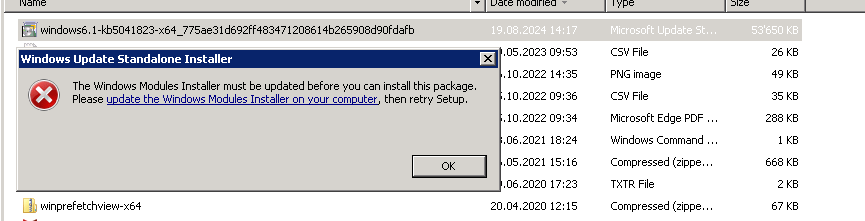
Powershell import > ONLY: If you encounter problems importing (downloading) the patches with the Microsoft PowerShell, please note that you may need to fix some TLS settings on your 2019 and 2022 WSUS servers (this applies only if you receive the error mentioned like this).
Here is HOW to get the 08/2024 CVE-2024-38063 Updates for 2008, 2008R2, 2012, 2012R2 into WSUS server so you don’t have to run after those machines. You could always install the patch manualy from the main MS LINK below. All links are listes and you do need an ESU contract to patch your old servers.
- Download ImportUpdateToWSUS.ps1 PS to your WSUS Server:
WSUS and the Microsoft Update Catalog | Microsoft Learn
- Get the Updateid per OS and patch (Sample: f34e1747-fedb-4962-bdae-dcbfbeda9c5a ) from https://www.catalog.update.microsoft.com/Search.aspx?q=5041838
- Import the Updates on the WSUS Server per Powershell
Explained more complex here:
Per patch info:
Lets start with the complicated 2008R2:
|
ONLY for 2008R2 where the 07-2024 want update |
|
Yes there is a link but the download links are EMPTY there for the KB 😉
So lets try all Update backwards maybe one brought it and we missed in WSUS or the ESU? We tried all below but could not get it running > All where already installed.
2008R2 > None of these resolved it KB5028264: Servicing stack update for Windows Server 2008 R2 SP1: July 11, 2023 – Microsoft Support https://catalog.update.microsoft.com/Search.aspx?q=KB5028264
The KB5028264 seemed to have some parts in it we could install this. (KB5028264: Servicing stack update for Windows Server 2008 R2 SP1: July 11, 2023)
Also here would be the corrrect latest way for ESU Extended Support customers:
So the order for an existing ESU integrated 2008R2 would be: The March 12, 2019 servicing stack update (SSU) (KB4490628). https://www.catalog.update.microsoft.com/Search.aspx?q=KB4490628 The latest SHA-2 update (KB4474419) released September 10, 2019. https://www.catalog.update.microsoft.com/Search.aspx?q=KB4474419 Extended Security Updates (ESU) Licensing Preparation Package https://www.catalog.update.microsoft.com/Search.aspx?q=KB4538483 Update for the Extended Security Updates (ESU) Licensing Preparation Package https://www.catalog.update.microsoft.com/Search.aspx?q=KB4575903 And then finally the 08/2024 Update. https://www.catalog.update.microsoft.com/Search.aspx?q=5041838
IF you want those PRE REQ Packages the 2008R2 patch in WSUS:
.\ImportUpdateToWSUS.ps1 -Updateid 1d4f0343-a41a-4782-8aed-18a620431171 .\ImportUpdateToWSUS.ps1 -Updateid ac54099f-27ab-4e36-befd-a29c67ddeb6f .\ImportUpdateToWSUS.ps1 -Updateid 44551c76-c430-4655-b791-665fea339ea8 .\ImportUpdateToWSUS.ps1 -Updateid 86381c48-1c0b-4479-8459-b1a8740bc63c
Servicing stack update for Windows Server 2008 R2 SP1: July 11, 2023 .\ImportUpdateToWSUS.ps1 -Updateid 298a1725-f89c-4759-a722-e6befc97c060
2008R2 08-2024 .\ImportUpdateToWSUS.ps1 -Updateid f34e1747-fedb-4962-bdae-dcbfbeda9c5a |
2008R2
https://www.catalog.update.microsoft.com/Search.aspx?q=5041838
Monthly Rollup (418MB)
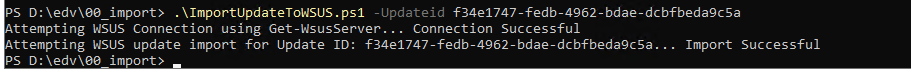
2008R2, KB5041838, UpdateID: f34e1747-fedb-4962-bdae-dcbfbeda9c5a
.\ImportUpdateToWSUS.ps1 -Updateid f34e1747-fedb-4962-bdae-dcbfbeda9c5a
https://www.catalog.update.microsoft.com/Search.aspx?q=5041823
Security Only (54MB)
2008R2, KN5041823, UpdateID: fa579db5-9512-46c4-8ade-a01dcf632759
.\ImportUpdateToWSUS.ps1 -Updateid fa579db5-9512-46c4-8ade-a01dcf632759
2012
https://catalog.update.microsoft.com/Search.aspx?q=KB5041851
Monthly Rollup (454B)
2012, KB5041851, UpdateID: f7364dfe-4c34-4de0-8e43-2eb251360a4b
.\ImportUpdateToWSUS.ps1 -Updateid f7364dfe-4c34-4de0-8e43-2eb251360a4b
2012 R2
Also here you MAY need to pre-installed the latest Service Stack Update

KB5041588: Servicing stack update for Windows Server 2012 R2: August 13, 2024 – Microsoft Support
https://www.catalog.update.microsoft.com/Search.aspx?q=KB5041588
.\ImportUpdateToWSUS.ps1 -Updateid 28a65867-6253-4fcc-992a-6847443e4444
https://catalog.update.microsoft.com/Search.aspx?q=KB5041828
Monthly Rollup (593MB)
2012R2, KB5041828, UpdateID: b32b2e3a-04d2-4430-abed-0e7d0702b7e5
.\ImportUpdateToWSUS.ps1 -Updateid b32b2e3a-04d2-4430-abed-0e7d0702b7e5
Import all older Server OS patches into WSUS at one:
PRE-REQ foer 2008 R2 + 2012 R2
.\ImportUpdateToWSUS.ps1 -Updateid 28a65867-6253-4fcc-992a-6847443e4444
.\ImportUpdateToWSUS.ps1 -Updateid 298a1725-f89c-4759-a722-e6befc97c060
:: SERVER
.\ImportUpdateToWSUS.ps1 -Updateid b32b2e3a-04d2-4430-abed-0e7d0702b7e5
.\ImportUpdateToWSUS.ps1 -Updateid fa579db5-9512-46c4-8ade-a01dcf632759
.\ImportUpdateToWSUS.ps1 -Updateid dba384c3-1ddb-482e-9242-09c145362516
.\ImportUpdateToWSUS.ps1 -Updateid 63a8ef5d-1856-402b-9a6e-446f772a3882
.\ImportUpdateToWSUS.ps1 -Updateid f7364dfe-4c34-4de0-8e43-2eb251360a4b
.\ImportUpdateToWSUS.ps1 -Updateid b32b2e3a-04d2-4430-abed-0e7d0702b7e5
.\ImportUpdateToWSUS.ps1 -Updateid f7364dfe-4c34-4de0-8e43-2eb251360a4b
.\ImportUpdateToWSUS.ps1 -Updateid f34e1747-fedb-4962-bdae-dcbfbeda9c5a
:: CLIENT (Older W10, LTSCx)
.\ImportUpdateToWSUS.ps1 -Updateid dd1cc492-bf28-49aa-a572-4a25d96efded
.\ImportUpdateToWSUS.ps1 -Updateid 54a3dd89-48da-47cc-a665-a314c36107bc
.\ImportUpdateToWSUS.ps1 -Updateid c4691b36-a271-46e0-a16c-740ad974cb26
.\ImportUpdateToWSUS.ps1 -Updateid 2544cf80-b99a-46ac-876f-c7221c1d9035
.\ImportUpdateToWSUS.ps1 -Updateid 0bc9bc55-b222-4ddd-aeaf-8f1b93cc2646
.\ImportUpdateToWSUS.ps1 -Updateid ce44bc72-4a70-4279-8dca-8a469bb1c3d1
.\ImportUpdateToWSUS.ps1 -Updateid c5be226e-6b25-426f-9ad2-c70eb6c52cfc
.\ImportUpdateToWSUS.ps1 -Updateid ca33b003-3266-416b-87ec-23e13e4dc60f
.\ImportUpdateToWSUS.ps1 -Updateid 74c3b930-b6fa-4f08-8477-312204c04ad4
.\ImportUpdateToWSUS.ps1 -Updateid 885fd69c-02e4-4a9e-8b8e-524b4a0da3ba
.\ImportUpdateToWSUS.ps1 -Updateid ab9f0f51-c7bb-4eb0-acb5-35923a602e2c
.\ImportUpdateToWSUS.ps1 -Updateid 3a02c92d-32c7-48d6-a526-608264568ba8
.\ImportUpdateToWSUS.ps1 -Updateid d2b4510c-1189-477c-b302-0e3d6533466b
.\ImportUpdateToWSUS.ps1 -Updateid 3fbb8433-d343-4663-a075-42af80924661
.\ImportUpdateToWSUS.ps1 -Updateid 1a0e8fce-c32e-457f-bb40-728edb42caff
MAIN LINKS:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38063
NVD – CVE-2024-38063 (nist.gov)
https://nvd.nist.gov/vuln/detail/CVE-2024-38063
Interesting Links:
What about the allways ON VPN aka Directaccess from MS?
DirectAccess and CVE-2024-38063 | Richard M. Hicks Consulting, Inc. (richardhicks.com)
https://directaccess.richardhicks.com/2024/08/15/directaccess-and-cve-2024-38063/
|
IPV6 disable or not;-) If then absolute carefully and the correct way.
Configure IPv6 for advanced users – Windows Server | Microsoft Learn https://learn.microsoft.com/en-us/troubleshoot/windows-server/networking/configure-ipv6-in-windows |
|
|
|
Problem when you turn off IPV6:
Example 1: On Domain Controllers, you might run into where LDAP over UDP 389 will stop working. See How to use Portqry to troubleshoot Active Directory connectivity issues Example 2: Exchange Server 2010, you might run into problems where Exchange will stop working. See Arguments against disabling IPv6 and Disabling IPv6 And Exchange Example 3: Failover Clusters See What is a Microsoft Failover Cluster Virtual Adapter anyway? and Failover Clustering and IPv6 in Windows Server 2012 R2. |
|
Built-In Dependence on IPv6
Compatibility and Future-Proofing
Active Directory and Group Policy
Networking Issues and Supportability
Incorrect Disabling Can Cause Problems
Performance Considerations
While there might be specific scenarios where disabling IPv6 could be justified (such as certain legacy applications or devices that do not support it), the general recommendation is to keep IPv6 enabled. Disabling it can lead to significant issues in a modern domain-joined Windows Server environment, including Active Directory problems, connectivity issues, and a lack of support from Microsoft.
If there is a need to address specific issues related to IPv6, it is better to troubleshoot and configure IPv6 properly rather than disabling it entirely. |
Just a sample from Exchange. This is JUST a sample you can look at Sharepoint or any such larger on-premises MS product.
That person says you can disable the next one says not. The third one disables it wrong and not fully.
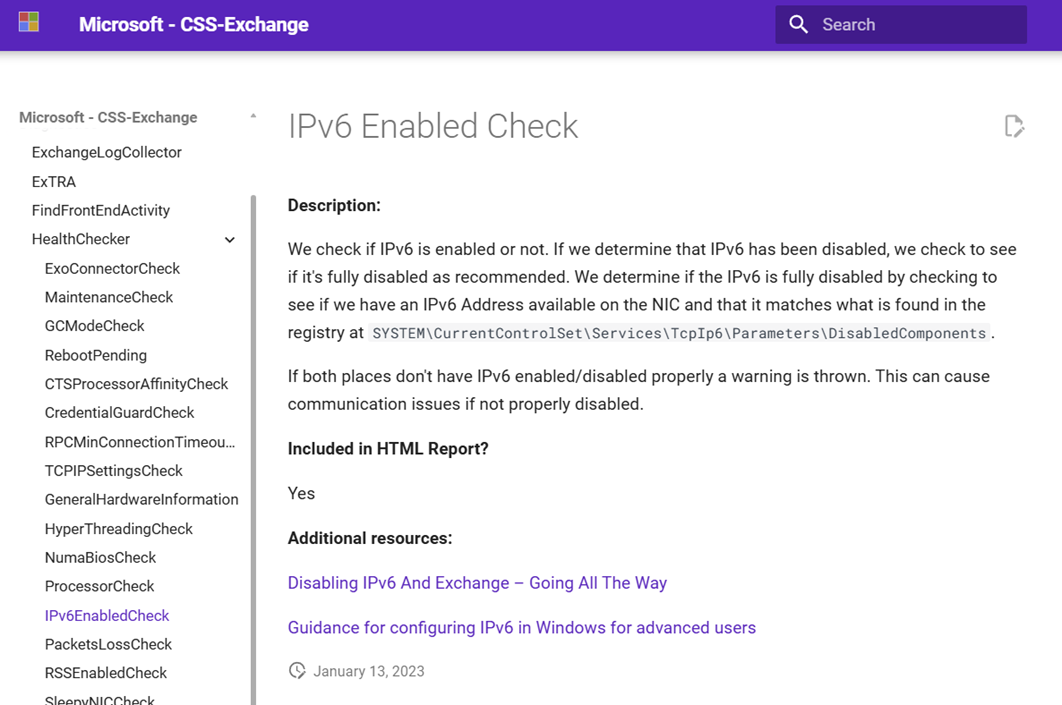
IPv6EnabledCheck – Microsoft – CSS-Exchange
https://microsoft.github.io/CSS-Exchange/Diagnostics/HealthChecker/IPv6EnabledCheck/
|
How to disable IPV6 the corect way on Windows Server 2016, 2019, and 2022 so it protects from: CVE-2024-38063 |
Method 1 would not stop the CVE-2024-38063 Method 1 |
|
Disabling IPv6 on Windows Server 2016, 2019, and 2022
Disable IPv6 Completely
1. Open the Registry Editor (regedit). 2. Navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters
3. Create a DWORD (32-bit) value named DisabledComponents. 4. Set the value to 0xFF (Decimal 255) to disable IPv6 entirely. 5. Restart the server for the changes to take effect.
Summary of Key Registry Values
– Disable IPv6: 0xFF (Decimal 255) |
Prefer IPv4 over IPv6 1. Open the Registry Editor (regedit). 2. Navigate to: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters. 3. Create a DWORD (32-bit) value named DisabledComponents. 4. Set the value to 0x20 (Decimal 32) to prefer IPv4 over IPv6. 5. Restart the server for the changes to take effect. Method 1 would not stop the CVE-2024-38063
This recommandation comes from the KNOW problem with disabling IPV6 full. But in the case with the leak this is a problem because it does not protect you.
Important Considerations
Do Not Disable IPv6: Disabling IPv6 can cause issues with Windows components. It’s generally recommended to configure your system to prefer IPv4 over IPv6 instead of disabling IPv6 entirely. BUT: THIS would not stop the CVE-2024-38063 |
|
Disable IPV6 via REGISTRY https://learn.microsoft.com/en-us/troubleshoot/windows-server/networking/configure-ipv6-in-windows |
||||||||||||||||||||
|
The IPv6 functionality can be configured by modifying the following registry key: Location: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters\ Expand table
|
|
Cmd.exe > Reg.exe One liner (Also below values to do it right) |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters” /v DisabledComponents /t REG_DWORD /d <value> /f |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Replace the value part as needed https://learn.microsoft.com/en-us/troubleshoot/windows-server/networking/configure-ipv6-in-windows |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
How to calculate the registry value
|
|
Name |
Setting |
|
Tunnel |
Disable tunnel interfaces |
|
Tunnel6to4 |
Disable 6to4 interfaces |
|
TunnelIsatap |
Disable Isatap interfaces |
|
Tunnel Teredo |
Disable Teredo interfaces |
|
Native |
Disable native interfaces (also PPP) |
|
PreferIpv4 |
Prefer IPv4 in default prefix policy |
|
TunnelCp |
Disable CP interfaces |
|
TunnelIpTls |
Disable IP-TLS interfaces |
For each bit, 0 means false and 1 means true. Refer to the following table for an example.
Expand table
|
Setting |
Prefer IPv4 over IPv6 in prefix policies |
Disable IPv6 on all nontunnel interfaces |
Disable IPv6 on all tunnel interfaces |
Disable IPv6 on nontunnel interfaces (except the loopback) and on IPv6 tunnel interface |
|
Disable tunnel interfaces |
0 |
0 |
1 |
1 |
|
Disable 6to4 interfaces |
0 |
0 |
0 |
0 |
|
Disable Isatap interfaces |
0 |
0 |
0 |
0 |
|
Disable Teredo interfaces |
0 |
0 |
0 |
0 |
|
Disable native interfaces (also PPP) |
0 |
1 |
0 |
1 |
|
Prefer IPv4 in default prefix policy. |
1 |
0 |
0 |
0 |
|
Disable CP interfaces |
0 |
0 |
0 |
0 |
|
Disable IP-TLS interfaces |
0 |
0 |
0 |
0 |
|
Binary |
0010 0000 |
0001 0000 |
0000 0001 |
0001 0001 |
|
Hexadecimal |
0x20 |
0x10 |
0x01 |
0x11 |
If you consider turning IPV6 OFF do it right! Do not forget things like:
|
And what about prefer IPV4 over IPV6 which some have active on Windows Servers? |
|
Ever used? Remember where? How does this come INTO the mix with IPV6 disable dont right or wrong?????
– `0x01`: Disable IPv6 on all interfaces except the loopback interface. – `0xFF`: Disable IPv6 entirely.
Method 1: Prefer IPv4 over IPv6 (See below THIS would not stop the CVE-2024-38063) |
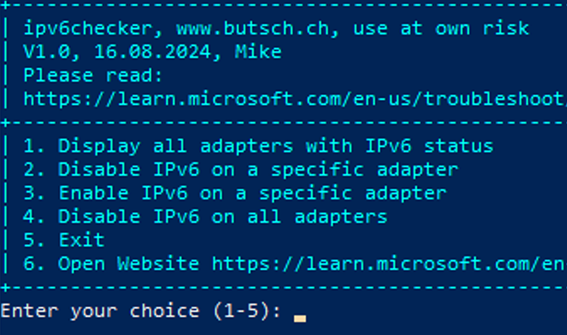
You can also use our interactive Powershell ipv6checker.ps1 to disable easy:
Please see:
MS SRV Disable IPv6 the correct way CVE-2024-38063 – www.butsch.ch
https://www.butsch.ch/post/ms-srv-disable-ipv6-the-correct-way-cve-2024-38063/


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.