How to use Microsoft certutil.exe –url or –urlcache to find CRL and OCSP on Windows manually, or utilize our freeware tool crlcheck.exe, which performs the same function fully automatically for all EXE files on your system.
crlcheck.exe

What is a CRL Certificate Revocation List file?
Each certificate authority (CA) periodically issues a certificate revocation list (CRL) to a public repository.
The CRL identifies revoked certificates by serial number.
After the CA revokes a certificate, the next CRL update will include the serial number of that certificate.
Manual steps to verify such a list
certutil.exe –url
certutil.exe is a command-line utility used in Windows operating systems to interact with cached URLs. It enables users to inspect and manipulate the cache of URLs stored locally on the computer.
certutil.exe operates in the security context of the current session context (That means the user calling it)
Verify with cerutil.exe –url
usage:
CertUtil [Options] -URL InFile | URL
Verify Certificate or CRL URLs
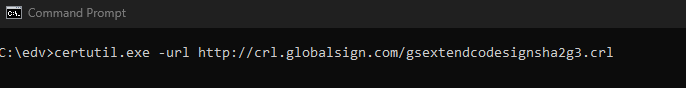
certutil.exe -url http://crl.globalsign.com/gsextendcodesignsha2g3.crl
Options:
|
-f |
Force overwrite |
|
-Unicode |
Write redirected output in Unicode |
|
-gmt |
Display times as GMT |
|
-seconds |
Display times with seconds and milliseconds |
|
-split |
Split embedded ASN.1 elements, and save to files |
|
-v |
Verbose operation |
|
-privatekey |
Display password and private key data |
|
-pin PIN |
Smart Card PIN |
|
-sid |
WELL_KNOWN_SID_TYPE
Numeric SID
22 — Local System 23 — Local Service 24 — Network Service |
CertUtil -? — Display a verb list (command list)
CertUtil -URL -? — Display help text for the “URL” verb
CertUtil -v -? — Display all help text for all verbs
certutil.exe -url http://crl.globalsign.com/gsextendcodesignsha2g3.crl
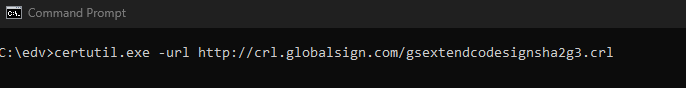
If you do that will open the URL Retrieval Tool
Select CRL’s (From CDP)
Press the Retrieve button
The tool/utility from Microsoft will now try to fetch that single CRL from the internet. Thats is the process and work for a single Certificate or CRL. With our crlcheck.exe you can do that autoamtic for any EXE on your client fully automatic and save a lot fo time.
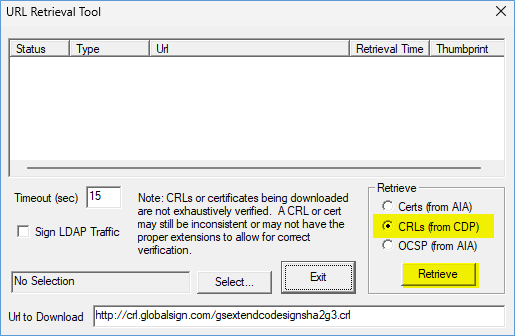
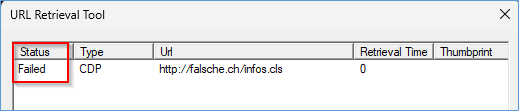
If it shows OK or VERIFIED all should be fine. Notice that CRL are 99% servced over http port 80.
This shows a failed CRL download
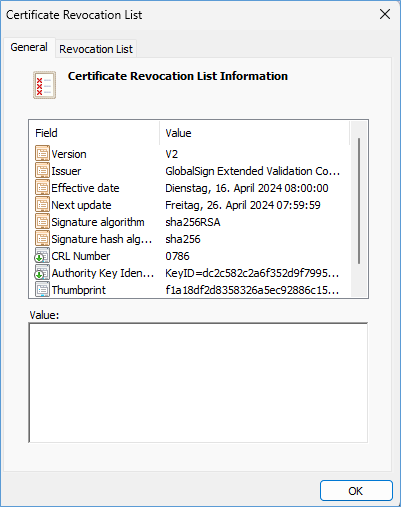
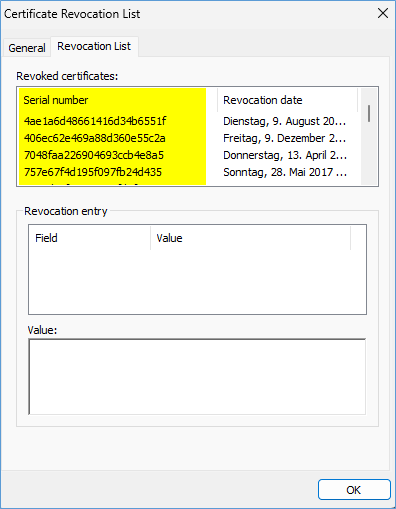
If you have an OK you should be able to open the Certificate Revocation List with a double click on the URL
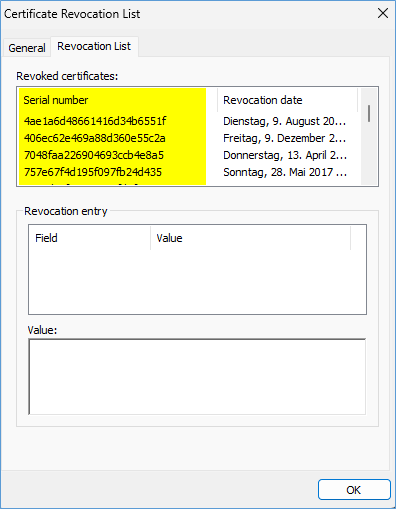
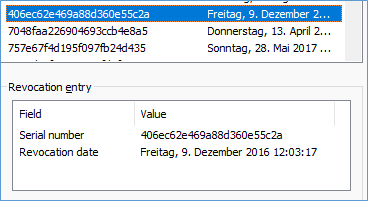
You will now see the Serial number and revocation date list.

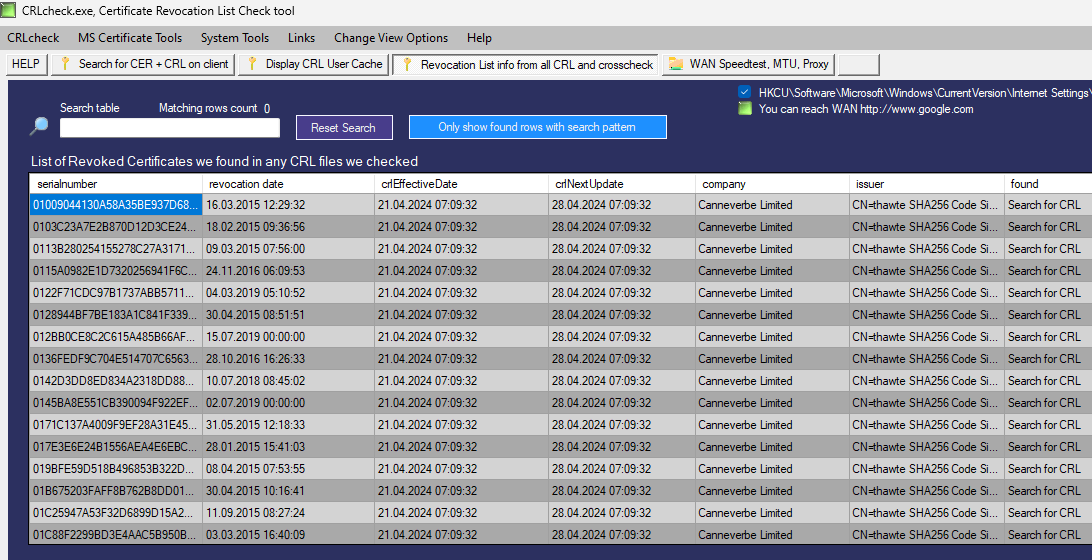
You can get the same list for ALL EXE files you run on your system fully automatic with our freeware tool crlcheck.exe.
Here is a sample view of the tool of the same information but for all files in the cache
certutil.exe –urlcache
Displays or deletes URL cache entries. It is a command-line utility used in Windows operating systems to interact with cached URLs. It enables users to inspect and manipulate the cache of URLs stored locally on the computer.
certutil.exe –urlcache CRL
certutil.exe –urlcache OCSP
certutil.exe [Options] -URLCache [URL | CRL | * [delete]]
[-f] [-v] [-split]
Options:
|
URL |
cached URL |
|
OCSP |
operate on all cached CRL URLs only |
|
CRL |
operate on all cached CRL OCSPs only |
|
* |
operate on all cached URLs |
|
delete |
delete relevant URLs from the current user’s local cache |
|
-f |
to force fetching a specific URL and updating the cache |
Options:
|
-f |
Force overwrite |
|
-Unicode |
Write redirected output in Unicode |
|
-gmt |
Display times as GMT |
|
-seconds |
Display times with seconds and milliseconds |
|
-split |
Split embedded ASN.1 elements, and save to files |
|
-v |
Verbose operation |
|
-privatekey |
Display password and private key data |
|
-pin PIN |
Smart Card PIN |
|
-sid |
WELL_KNOWN_SID_TYPE
Numeric SID
22 — Local System 23 — Local Service 24 — Network Service |
CertUtil -? — Display a verb list (command list)
CertUtil -urlcache -? — Display help text for the “URL” verb
CertUtil -v -? — Display all help text for all verbs
certutil.exe –urlcache CRL
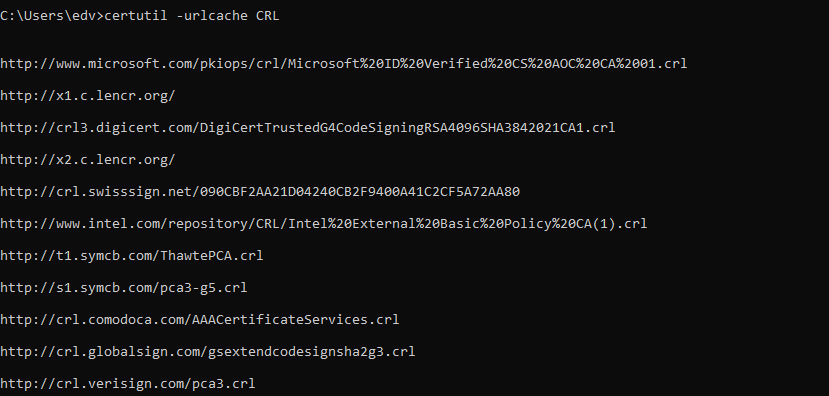
certutil.exe –urlcache
Screenshot below shows the sample output from the Windows users CRL cache. This are CRL that the current user used.
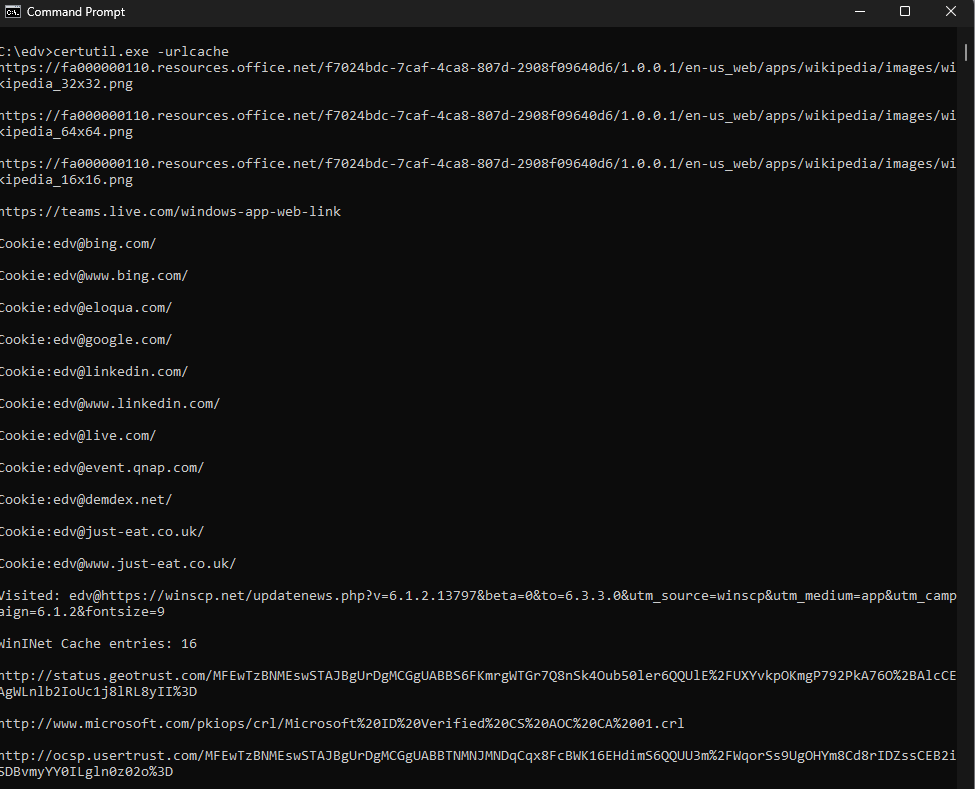
You can archive the same using our freeware tool crlcheck.exe. You can also extract and search all information the cached CRL files like a list of Revocaked Certificates, serials and dates.
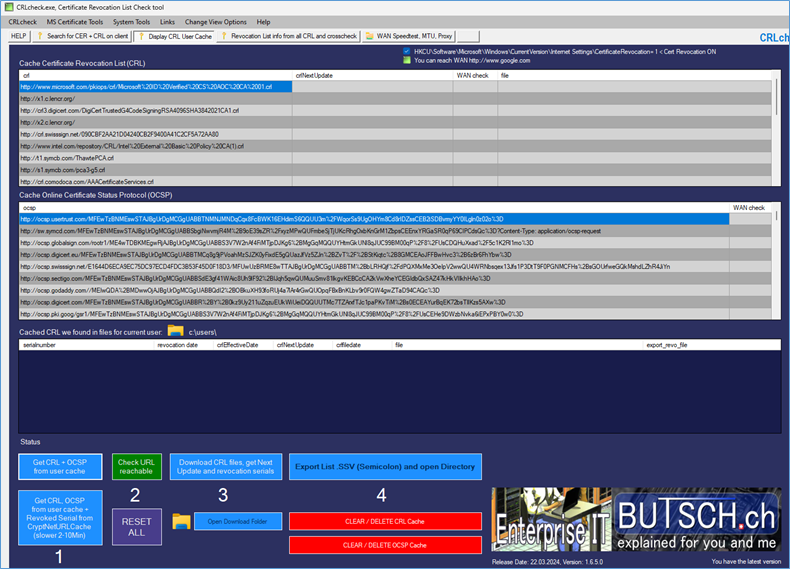
How to check if a Executable is Digital Signed and uses a CRL Certificate Revocation List
Let us check the freeware too Treesize.exe or treesizefree.exe which often i used on servers to check what uses space.
Right click on the EXE
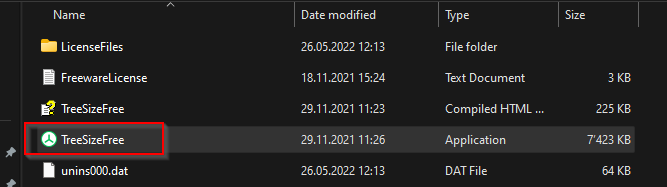
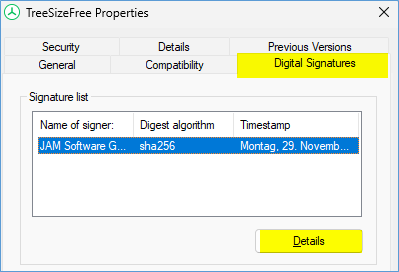
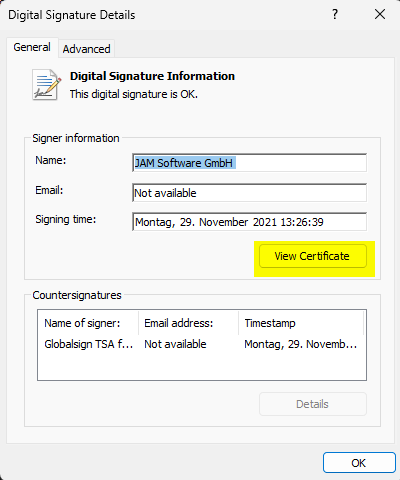
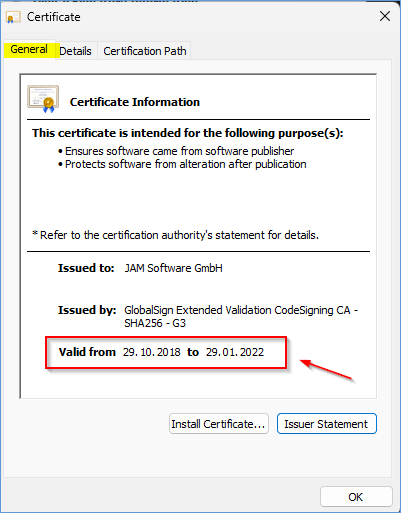
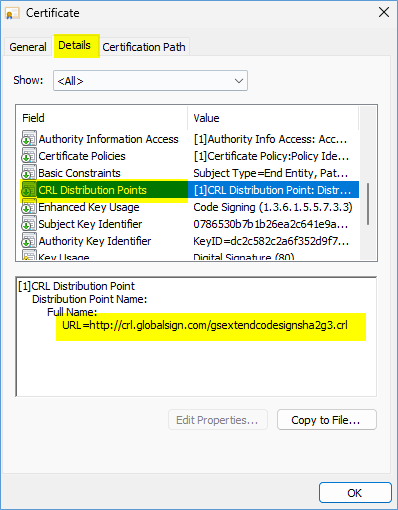
Copy and paste the URL for the CRL from the Cert into your browser and try to open the file.
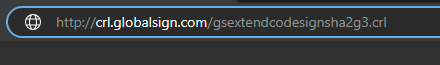
If you can open it all looks fine from the retrieval process. That is often the point where companys have problems if their clients are behind a Proxy or web filter and not allow all CRL fetching. (Blocked)
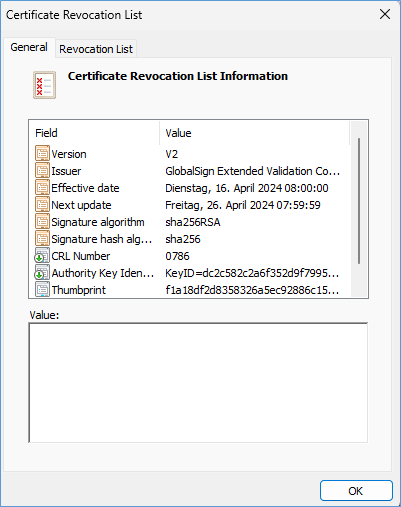
CRL and ocsp URL we had on Windows 11 23H2 system around April 2024
|
http://crl.certum.pl/cscasha2.crl |
|
http://crl.comodoca.com/COMODORSACodeSigningCA.crl |
|
http://crl.globalsign.com/gscodesignsha2g3.crl |
|
http://crl.globalsign.com/gsextendcodesignsha2g3.crl |
|
http://crl.globalsign.com/gsgccr45codesignca2020.crl |
|
http://crl.globalsign.com/gsgccr45evcodesignca2020.crl |
|
http://crl.godaddy.com/gdig2s5-6.crl |
|
http://crl.microsoft.com/pki/crl/products/CodeSignPCA.crl |
|
http://crl.microsoft.com/pki/crl/products/CSPCA.crl |
|
http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl |
|
http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl |
|
http://crl.microsoft.com/pki/crl/products/Microsoft Code Signing PCA(2).crl |
|
http://crl.sectigo.com/SectigoPublicCodeSigningCAR36.crl |
|
http://crl.sectigo.com/SectigoRSACodeSigningCA.crl |
|
http://crl.thawte.com/ThawteCodeSigningCA.crl |
|
http://crl.usertrust.com/UTN-USERFirst-Object.crl |
|
http://crl3.digicert.com/assured-cs-g1.crl |
|
http://crl3.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA2562021CA1.crl |
|
http://crl3.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA3842021CA1.crl |
|
http://crl3.digicert.com/EVCodeSigning-g1.crl |
|
http://crl3.digicert.com/EVCodeSigningSHA2-g1.crl |
|
http://crl3.digicert.com/sha2-assured-cs-g1.crl |
|
http://crl3.digicert.com/sha2-ha-cs-g1.crl |
|
http://crl4.digicert.com/assured-cs-g1.crl |
|
http://crl4.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA2562021CA1.crl |
|
http://crl4.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA3842021CA1.crl |
|
http://crl4.digicert.com/EVCodeSigningSHA2-g1.crl |
|
http://crl4.digicert.com/sha2-assured-cs-g1.crl |
|
http://crl4.digicert.com/sha2-ha-cs-g1.crl |
|
http://CSC3-2004-crl.verisign.com/CSC3-2004.crl |
|
http://csc3-2010-crl.verisign.com/CSC3-2010.crl |
|
http://evcs-crl.ws.symantec.com/evcs.crl |
|
http://evcs-ocsp.ws.symantec.com |
|
http://ocsp.comodoca.com |
|
http://ocsp.digicert.com |
|
http://ocsp.globalsign.com/gsgccr45codesignca2020 |
|
http://ocsp.globalsign.com/gsgccr45evcodesignca2020 |
|
http://ocsp.godaddy.com/ |
|
http://ocsp.sectigo.com |
|
http://ocsp.thawte.com |
|
http://ocsp.verisign.com |
|
http://oneocsp.microsoft.com/ocsp |
|
http://pki.intel.com/crl/IntelCA7B.crl |
|
http://secure.globalsign.com/cacert/gscodesignsha2g3ocsp.crt |
|
http://secure.globalsign.com/cacert/gsextendcodesignsha2g3ocsp.crt |
|
http://sf.symcb.com/sf.crl |
|
http://sv.symcb.com/sv.crl |
|
http://sw.symcb.com/sw.crl |
|
http://tl.symcb.com/tl.crl |
|
http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl |
|
http://www.microsoft.com/pkiops/crl/Microsoft ID Verified CS AOC CA 01.crl |
|
http://www.microsoft.com/pkiops/crl/Microsoft ID Verified CS EOC CA 02.crl |
|
http://www.microsoft.com/pkiops/crl/Microsoft Windows Phone Production PCA 2012.crl |
|
http://www.microsoft.com/pkiops/crl/Microsoft Windows Third Party Component CA 2012.crl |
|
http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl |
Tags:
Certificate Revocation Lists (CRLs), Certificate validation, pki, cache, reboot, delay, windows, debug, logon, critrix, vdi, ivanti, intunes, CRL troubleshooting, Certificate status checking, Digital certificates, Certificate management, Certutil.exe, Certificate authority (CA), Cryptographic operations, Certificate authentication, Digital signature verification, Cybersecurity, IT professionals, Cyber threats, Certificate integrity, Certificate validation processes, Security posture, Network security, Online security, Whitepapers, Certificate validation best practices, Certificate expiration, Certificate revocation, Digital transaction security, IT security management.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.