Error after importing a SAN/UC Certificate in Exchange 2010:
Error 1: “The certificate is invalid for exchange server usage”
This is because of a missing ROOT and Intermediate CA not imported.
Now Error After you resolved you get:
Error 2: “The certificate status could not be determined because the revocation check failed”
That means the Certificate Service (Certutil) can reach some URL from Microsoft or from the Cert PKI provider (Example Comodo)
Error: When your see the second error you are unable to”Export” a certificate in EMC / Exchange 2010 GUI. (Like for Load Balancer or CAS-Array)
HINT> If the certificate Status is NOT valid you still are able to “ENABLE” the imported Certificate with Powershell. We are unsure if Export would work.
See https://www.butsch.ch/post/Generate-SAN-UC-Certificate-SSL-on-Exchange-2010.aspx on how to do that.
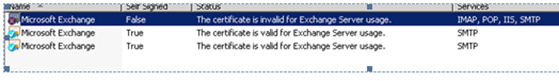
First error comes “The certificate is invalid for exchange server usage” because suddenly your up to date Windows Server does not have an actual updated ROOT CA from some Cert Publishers.
-
Import the Root CA Files you got together with the provider on your Exchange 2010 CAS Server.
-
If you have a ROOT CA (Certificate Authority) you may publish the Root CA through your OWN CA to the Windows Domain. Type CERTUTIL in command to find out if you have/had one and then please ask the PKI-Engineer in your environment to help (If you have one 😉
Here is how to manual import on the Exchange 2010 CAS:
The file you got from your PKI-Provider together with your certificate.

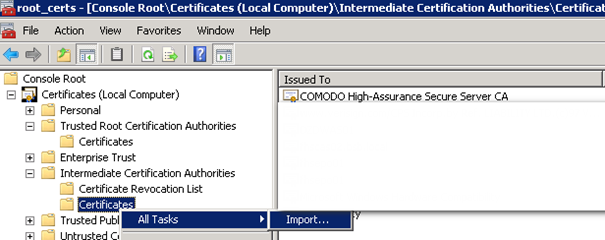
Start > mmc
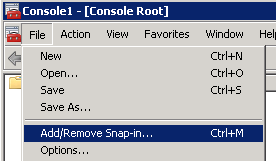
Import the Root CA you got from your ISP to your Exchange 2010 CAS Server.
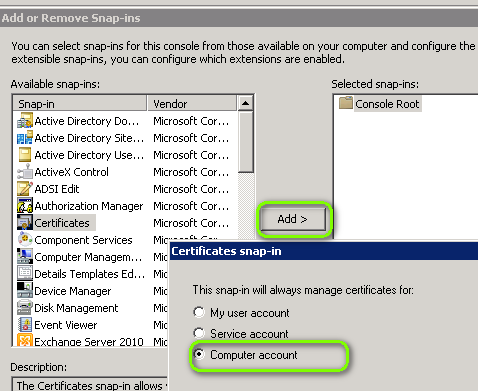
- ROOT CA (Most with Root in the name) to “Trusted >Root Certification Authorities”)
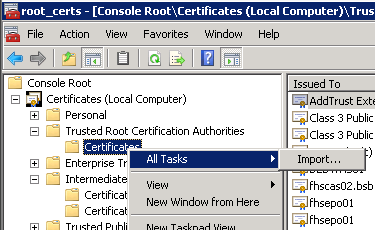
Import the second Certificate you got from the Provider to “Intermediate”
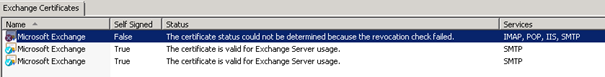
After this you see in the Exchange 2010 EMC under Server (on right side)
The certificate status could not be determined because the revocation check failed
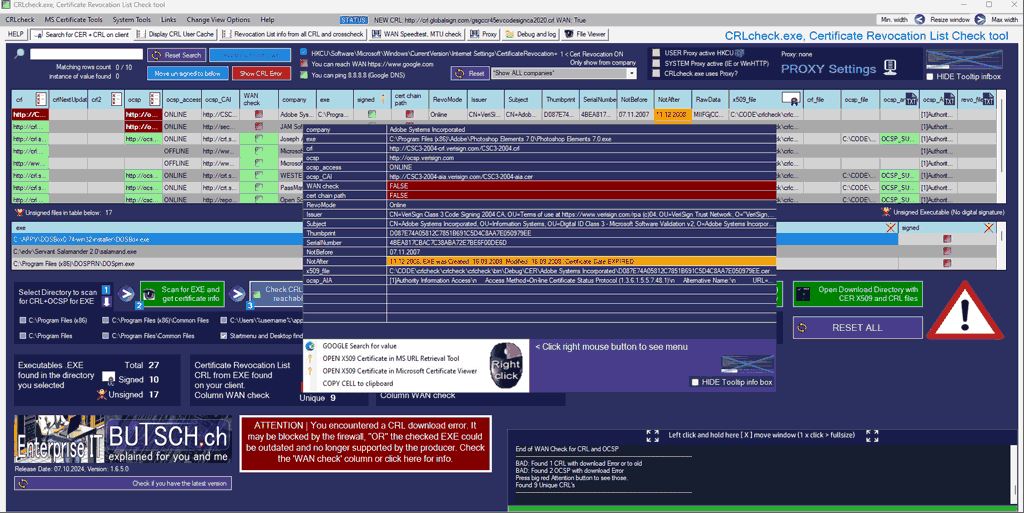
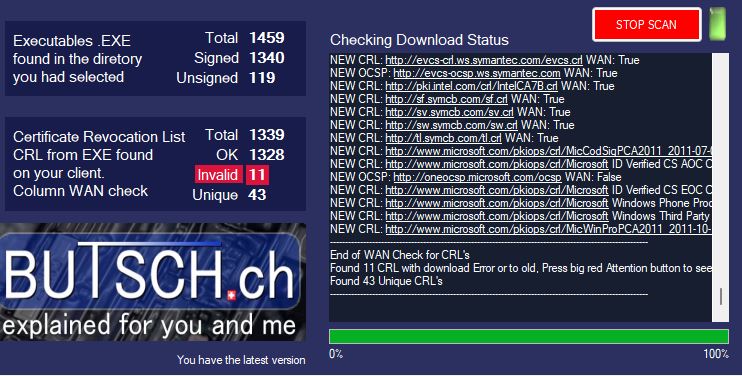
Check which Certificate paths the Exchange wants to have access to AND open those on the FIREWALL/WEBFILTER or use the correct PROXY Settings. Open the URL string you see in a Browser and check if you can download the files. Just make sure your Exchange 2010 can reach those URLs.
certutil -URLcache CRL (Check)
Here is an output from certutil -URLcache
http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab
http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl
http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl
http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab
http://crl.microsoft.com/pki/crl/products/CSPCA.crl
http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab
Also and esp. for Comodo Certificates check and validate where your CERT itself want to go and OPEN those URL.
certutil -verify -urlfetch c:\edv\13296984.crt (13296984.crt filename of your provider Certificate)
—————- Certificate AIA —————-
Failed “AIA” Time: 0
Error retrieving URL: The operation timed out 0x80072ee2 (WIN32: 12002)
http://crt.comodoca.com/COMODOHigh-AssuranceSecureServerCA.crt
—————- Certificate CDP —————-
Failed “CDP” Time: 0
Error retrieving URL: The operation timed out 0x80072ee2 (WIN32: 12002)
http://crl.comodoca.com/COMODOHigh-AssuranceSecureServerCA.crl
—————- Certificate OCSP —————-
Failed “OCSP” Time: 0
Error retrieving URL: The operation timed out 0x80072ee2 (WIN32: 12002)
Revocation Check Failed “Certificate (0)” Time: 0
[0.0] http://crt.usertrust.com/AddTrustExternalCARoot.p7c
Verified “Certificate (1)” Time: 0
[0.1] http://crt.usertrust.com/AddTrustExternalCARoot.p7c
Revocation Check Failed “Certificate (0)” Time: 0
[1.0] http://crt.usertrust.com/AddTrustUTNSGCCA.crt
—————- Certificate CDP —————-
Verified “Base CRL (0bbc)” Time: 0
[0.0] http://crl.usertrust.com/AddTrustExternalCARoot.crl
—————- Base CRL CDP —————-
No URLs “None” Time: 0
—————- Certificate OCSP —————-
Verified “OCSP” Time: 63
[0.0] http://ocsp.usertrust.com
OPEN these URL on the Firewall also:
http://crt.comodoca.com/COMODOHigh-AssuranceSecureServerCA.crt
http://crl.comodoca.com/COMODOHigh-AssuranceSecureServerCA.crl
http://ocsp.comodoca.com
http://crt.usertrust.com/AddTrustExternalCARoot.p7c
http://crt.usertrust.com/AddTrustUTNSGCCA.crt
http://crl.usertrust.com/AddTrustExternalCARoot.crl
http://ocsp.usertrust.com
PROXY
If you have a PROXY do not to EXCLUDE your > Exmaple > *.domain.local from the PROXY or your Exchange EMC want work anymore!
If you can’t open the CAS Server to those URL or you don’t have the right to do so. Check how to configure the Proxy Setting with NETSH.
http://exchangeserverpro.com/exchange-2010-certificate-revocation-checks-and-proxy-settings/
http://www.geekmungus.co.uk/microsoft-exchange/exchange2010-ucccertificatethecertificateisinvalidforexchangeserverusage
http://blogs.technet.com/b/pki/archive/2007/09/13/how-to-refresh-the-crl-cache-on-windows-vista.aspx
http://blogs.technet.com/b/exchange/archive/2010/07/26/emc-and-certificates-with-failed-revocation-checks-in-exchange-2010.aspx
http://support.microsoft.com/kb/979694/en-us
http://msexchangeguru.com/2012/11/12/certificate-revocation/
certutil -urlcache crl delete (Clean Cache)
certutil -urlcache ocsp delete (Clean Cache)
CRL check, Zertifikatsperrlisten Software, Certificate Revocation List Check Tool zum suchen aller geblockten CRL in Firmenumgebungen, crlcheck.exe


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.