Activesync with Exchange 2013 does not work, ADMINSHOLDER Flag (an old bad friend)
ERROR YOU SEE: Access+is+denied.%0d%0aActive+directory+response%3a+00000005%3a+SecErr%3a+DSID-03152612%2c+problem+4003+(INSUFF%5FACCESS%5FRIGHTS)%2c+data+0%0a_
We just had a user with Activesync with a user migrated from 2007 to 2013. The user was fresh made on 2007 and migrated forth and back a few times.
https://testconnectivity.microsoft.com/
Did show all info he can get and one thing triggered alerts with us. 4003+(INSUFF%5FACCESS%5FRIGHTS)
This was back 2003 > 2007 Migrations but comes again and again. Strange thing is that the test user account is only in a few groups and we never made him LOCALADMIN. But one group still seems to trigger the ADMINSHOLDER flags which should protect special accounts like “IISUSER” or Administrator.
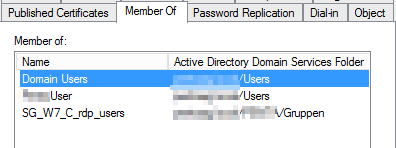
Then we did see why.
If the user is member of the group “PRINT OPERATORS” this will be the case.
So GPO, Activesync and many other things will not work. This has been mentioned here:
Good explanation from John Pollicelli
https://technet.microsoft.com/en-us/magazine/2009.09.sdadminholder.aspx
https://technet.microsoft.com/de-de/magazine/2009.09.sdadminholder.aspx
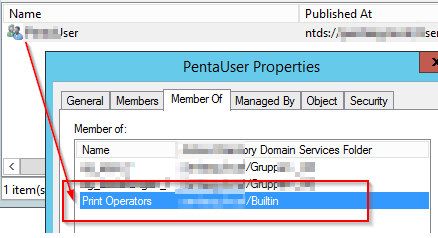
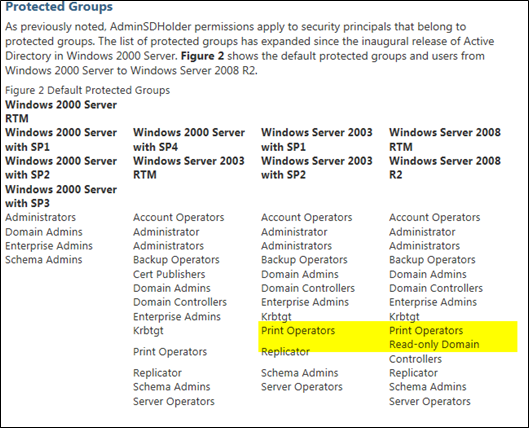
Resolution:
FIX the Inheritance of the account and all will work fine. See our other two posts on how to do that.
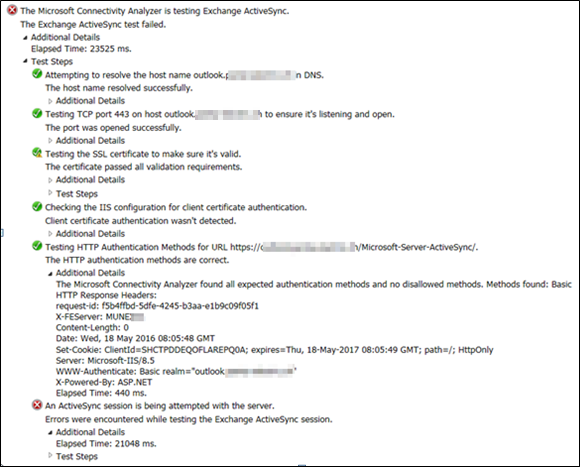
The Red part below (RED-X)
|
Activesync Log from https://testconnectivity.microsoft.com/ |
|||
|
Get a list of all user who have such a behaviour:
Windows Server 2008R2, blaue Powershell aufmachen
Import-Module ActiveDirectory
Get-ADUser -LDAPFilter “(objectcategory=person)(samaccountname=*)(admincount=1)”
Es gibt eine einfache Möglichkeit, um festzustellen, welche Benutzer und Gruppen in Ihrer Domäne AdminSDHolder geschützt.Sie können Abfragen das Attribut AdminCount, um festzustellen, ob ein Objekt durch das AdminSDHolder-Objekt geschützt ist.Die folgenden Beispiele verwenden das ADFind.exe-Tool, das von Joeware gedownloadet werden kann.NET.
-
Suchen alle Objekte in einer Domäne, die durch AdminSDHolder geschützt sind, geben Sie:
Adfind.exe -b DC=domain,DC=com -f “adminCount=1” DN
-
Suchen alle Benutzerobjekte in einer Domäne, die durch AdminSDHolder geschützt sind, geben Sie:
Adfind.exe -b DC=domain,DC=com -f “(&(objectcategory=person)(objectclass=user)(admincount=1))” DN
-
Suchen alle Gruppen in einer Domäne, die durch AdminSDHolder geschützt sind, geben Sie:
Adfind.exe -b DC=domain,DC=com -f “(&(objectclass=group)(admincount=1))” DN
Hinweis: Ersetzen Sie in den vorherigen Beispielen, DC = Domain, DC = com mit dem definierten Namen Ihrer Domäne.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.